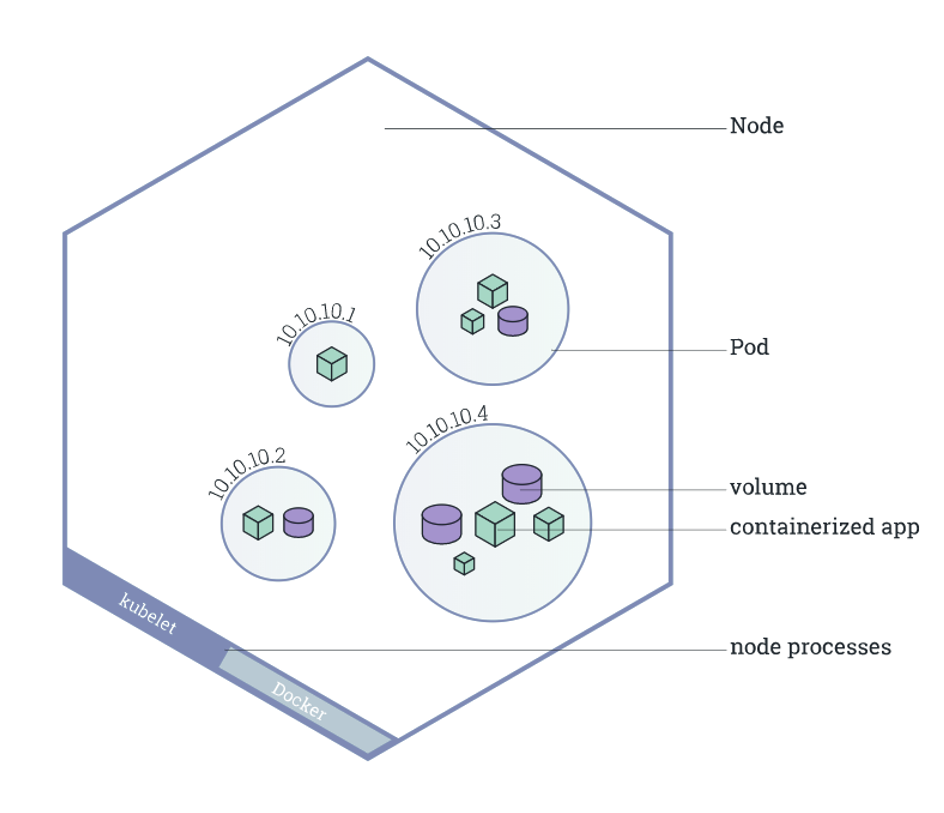
Alike a pod of whales or a pea pod, a pod in Kubernetes is a collection of one or more Linux containers and the smallest executable unit. Containers in the same pod use shared compute resources. These resources are put together to form clusters. If a process runs on a container and the pod fails, Kubernetes can create a replica of the same pod to continue the process. This process is known as replication. This isn’t carried only for the failover process but also horizontal scaling when one or more containers are overloaded.
One obvious question would be, why can’t Kubernetes run the containers directly without needing this extra group? The reason extends to the relationship between pods and clusters; running containers in pods enables the communication between different containers in the pod and, simultaneously, has a degree of isolation.
What is Pod Security?
Pod security is usually regulated through a Kubernetes admission controller, which check pod specifications against pre-established security standards to determine whether a pod should run. Simply put, pod security is a list of security policies, and each pod must obey these policies to run. This process ensures no malicious code or process runs in any insecure pods.
Let’s look at some of the fool-proof methods for pod security.
Logging and Monitoring Pods and Clusters
Auditing, logging, and monitoring are key security features that should not be disregarded to improve your pods’ security posture. Audit logs for Kubernetes are thorough records of each request to the Kubernetes API server. These audit logs can be used for auditing, compliance, and security analysis, as well as providing important information about what is going on in a pod. In addition, security records in Kubernetes audit records can assist in discovering aberrant behavior and access to critical resources by capturing the whole sequence of events.
Enabling audit logging and saving the audit logs to a secure repository for examination in the case of a compromise is recommended. Kubernetes also has cluster-based logging, which logs container activities to a central logging system.
Defining Pod Security Standards
The pod security politics are cumulative policies ranging from highly permissible to highly restrictive. There are three primary policies: privileged, baseline, and restricted.
The privileged policy gives the widest possible permissions and is left open intentionally. This is suitable for system- and infrastructure-level workloads managed by privileged, trusted users.
The baseline policy offers a very simple base-level permissibility. It is for common containerized workloads and gives the bare essentials to prevent privilege escalations while not being as open as the privileged policy. This policy is primarily for non-critical application operators and developers.
Finally, as the name implies, the restricted policy is the most restrictive. It enforces pod-hardening best practices while sacrificing ease of use. This is the highest security level and is meant for lower-trust users.
Based on your application goals, you can incorporate these security policies accordingly.
Apply Network Policies to Secure Your Pod
There are no limits on which nodes can run a pod by default. However, you can use network policies to specify communication rules for pods within a cluster. The network plugin implements network policies, and using them may necessitate using a network driver that supports policies.
Consider employing a combination of network policies to secure communication and security lists. This will protect host-level network communication for the optimal network security posture. In addition, the Kubernetes pod security context aids in defining a pod’s or container’s privilege and access-control settings.
Set Limits on Resource Usage
While safeguarding APIs and clusters is important, setting limits on CPU, memory, and persistent disk space can also help with pod security. This practice can protect your cluster from denial-of-service attacks if a single container consumes all available resources. For namespaces, quotas and limit ranges can define resource restrictions. For containers, you can use requests and limits to set resource limits.
Safeguard Confidential Data with Secrets
In Kubernetes, you can use the Secret method to store sensitive data. This works well for storing passwords, keys, and other sensitive information. They can be used to store textual data, Docker configurations, certificates, tokens, and files. You can use K8 Secrets in containers by mounting them as data volumes or exposing them as environment variables.
Conclusion
So these are some of the trusted methods for pod security. While these methods improve security, it is also important to consider other methods like using RBACs, Keeping Kubernetes up to date, securing container images, etc. Pod security policy has much more influence over many other parts of the pod, so you should utilize it wisely, depending on your cluster’s and applications’ needs.











FIND US ON SOCIALS