Mozilla announced on Thursday that it has extended its bug bounty program to include a new category focused on bypassing methods for vulnerability detection, security features, and Firefox defense-in – depth measures.
Mozilla claims mitigation bypasses have until now been categorized as low- or moderate-severity problems, but as part of the new Exploit Mitigation Bug Bounty, they are now eligible for a reward associated with a high-severity bug.
This means preventing bypasses with privileged access will result in researchers earning up to $ 5,000 if they submit a high quality study. Nevertheless, if mitigation is bypassed without privileged access — which typically involves chaining more than one weakness — researchers will receive a reward for the vulnerability itself and a mitigation bypass bonus of 50 per cent.
Mozilla says it still allows researchers to test Firefox Nightly, the browser’s testing and development update, but bugs discovered in Nightly will only qualify for a bounty if they aren’t identified internally by Mozilla within four days of the code change that introduces the bug posted to the primary repository.
Some have criticized Mozilla for increasing the bug bounty program shortly after some of its cybersecurity employees were laid off. The company, however, told that the recent layoffs had no effect on the Firefox browser and Firefox services security teams that were responsible.
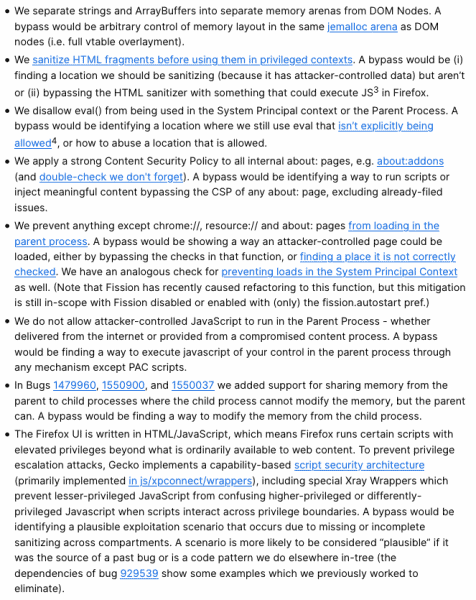
Mozilla has posted a list of the mitigations the Exploit Mitigation Risk Bounty covers:











Leave a Reply