A group based in Hong Kong has been identified behind the recent outbreaks of malicious ads via Windows 10 apps and Microsoft games. This group is behind millions of ads that forward users to bundles of scams, malware and adware.
BleepingComputer reported in April and June of this year that malvertising was targeting German and French users with technological support, phishing pages and counterfeit sweepstakes. The striking fact is that ads appear in Microsoft free games and Windows 10 apps to get the app out of hand and run unwanted sites on a default user’s browser. This attack was unusual.
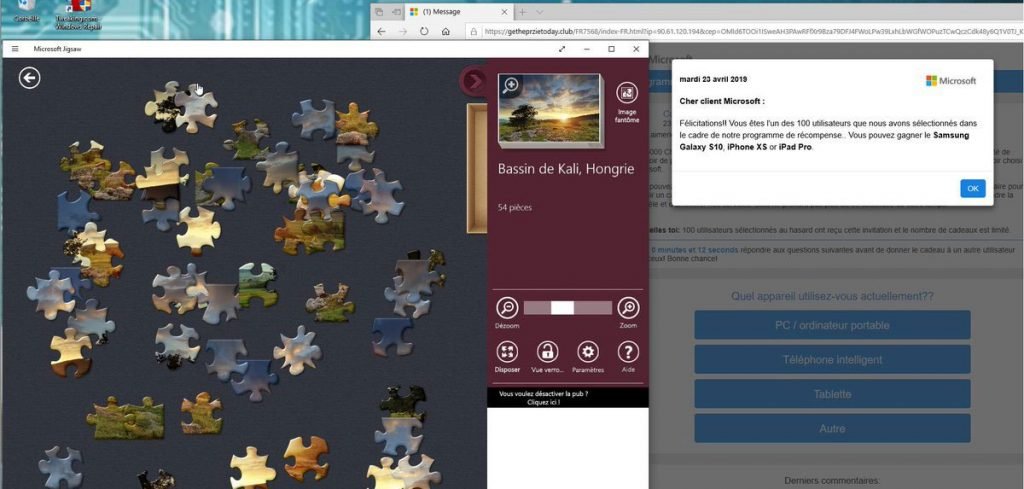
Malvertising in Microsoft Jigsaw
The advertising security company Confiant has found an advertiser based in Hong Kong who created corporate identities for partnerships using DSPs (demand side platforms), a report shared with BleepingComputer. Then its low quality and often malicious ads would be distributed to other ad networks and publishers by way of DSPs.
“We were fortunate enough in March 2019 to receive comments on a campaign that fit in the assignment model for this assailant from one of our customers in the platform,” confident security engineer and investigator Eliya Stein said. “It was reported the buyer,” fiber-ads. “It was also told that they have recently pivoted on a new corporate identity,’ clickfollow.” “Fibreads” were also involved in advertising marketplace MyMediAds as well as partnering directly with DSPs. “It was also reported to us that this was an exact buyer.
Confident shows how the malverter actively sought access to premium and self-service platforms. They also wanted to publish gift cards, free Samsung or iPhone, and scams for sweepstakes.
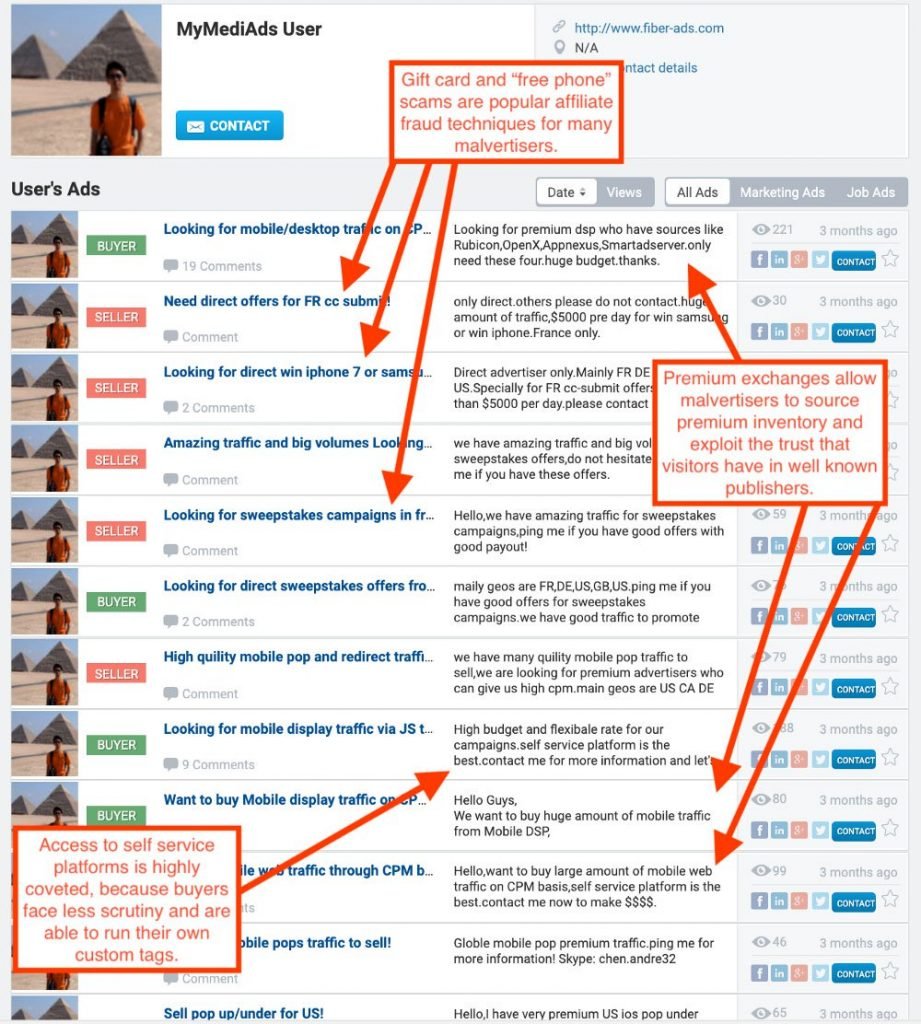
MyMediaAds profile for fiber-ads
With over 100 million advertising shown in 2019 alone and two of their highest peaks in May 2019 and June 2019, this malvertising group has been successful. The May campaign took place approximately at the same time as those ads were reported by French users, while June was when German users reported them.
“When visualized, campaign volumes associated with this attribution model paint a picture of a very active and persistent malvertiser. The two peaks below are approximately 28MM and 14.5MM impressions respectively with over 100MM impressions served this year as of mid June.”
Confidential currently monitors and blocks malvertising campaigns from this group, but the publicity security company warns advertisers that they have better work to take their advertisers into custody and should anything feel off, they must avoid business opportunities.
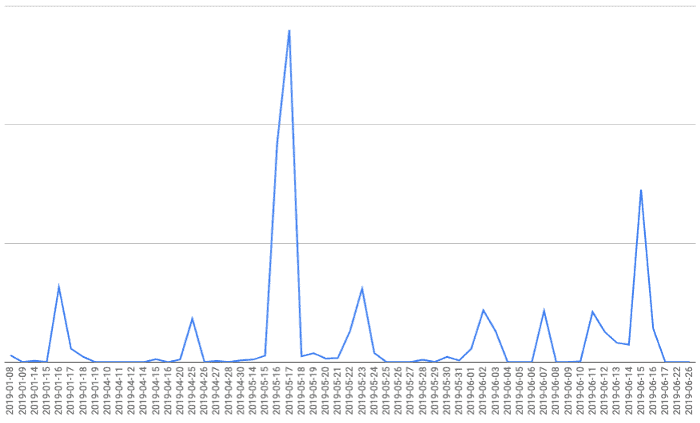
Impressions blocked by Confiant per day in 2019.
“As a parting thought, we would like to suggest that ad tech platforms take extra care to vet their advertisers — and if something smells a bit fishy, like a buyer incorporated in a dodgy jurisdiction, it might be prudent to bypass that business opportunity altogether.”
Misuse led to scams and malware
The malvertising campaigns were not distributed exclusively to Microsoft Games and Windows 10 apps. Rather, they target a specific subset of users and as in-app ads can monetize Microsoft apps, they are also shown here.
The malvertiser ad server will determine whether the user is a user who wants a scam ad to target when an ad from a malvertising campaign is sent to a user.
If not, the user showed a generic, fake ad, but the ad code would redirect the user to a scam page that displayed scams, free phone and tech support, if the user was one target.
Below are examples of the scam types that a mobile user has seen.

Apart from technology supports and free products, desktop users are shown to have even more damaging payloads in the form of pages that use unwanted security programs and adware packages.
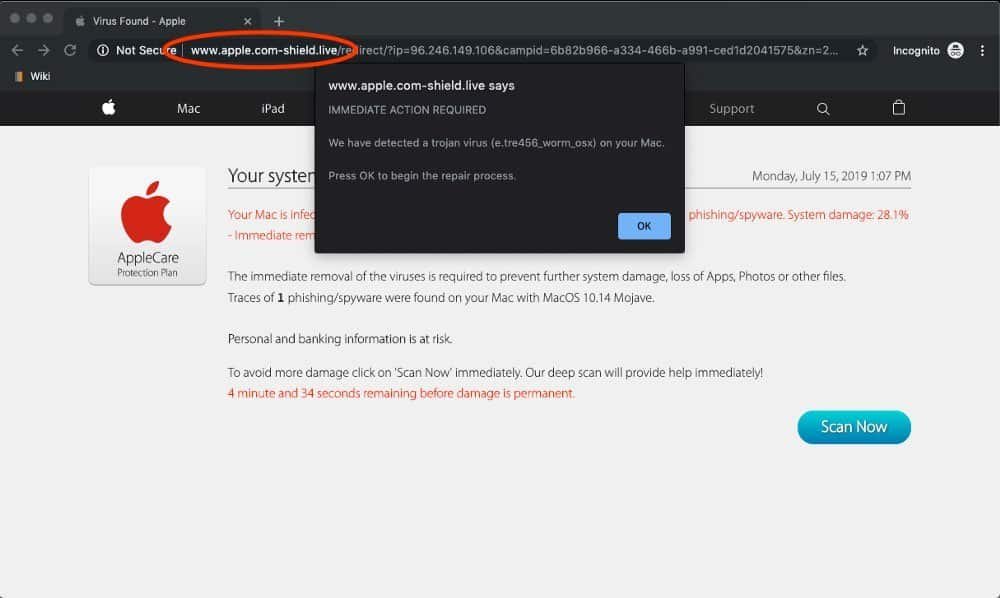
Apple tech support scam pushing unwanted software
As always, no software that states that a risk or security issue is found should be downloaded on a website by users. This often leads to the installation on a computer of malware and fake security programs.











Leave a Reply