On Tuesday, Microsoft warned in a series of posts on Twitter of a spike in gift card-themed company email compromise (BEC) attacks targeting K-12 school teachers by impersonating their peers.
A new increase in company email compromise (BEC) attacks has been observed demanding gift cards specifically targeting K-12 school teachers. Attackers impersonate classmates or school administrators to persuade beneficiaries to buy separate gift cards, warned Microsoft Security Intelligence.
We detected a recent spike in busines email compromise (BEC) attacks soliciting gift cards primarily targeting K-12 schoolteachers. Attackers impersonate colleagues or school officials to ask recipients to purchase various gift cards. pic.twitter.com/CFk37M5fpp
— Microsoft Security Intelligence (@MsftSecIntel) February 2, 2021
The attackers produce false email addresses impersonating school employees from K-12. Accounts are created on the basis of information open to the public that they gather from different websites or social media networks. To deliver scam emails to their targets, they then use these accounts.
Free email systems, including Gmail, Outlook, Mail.ru, Hotmail, iCloud, and Yahoo, are being exploited by attackers. Microsoft said there was no email spoofing used by the scammers, only newly registered accounts.
The threat actors, characteristic of BEC scams and phishing attacks, use different lures and situations to create a sense of authenticity and to indicate urgency.
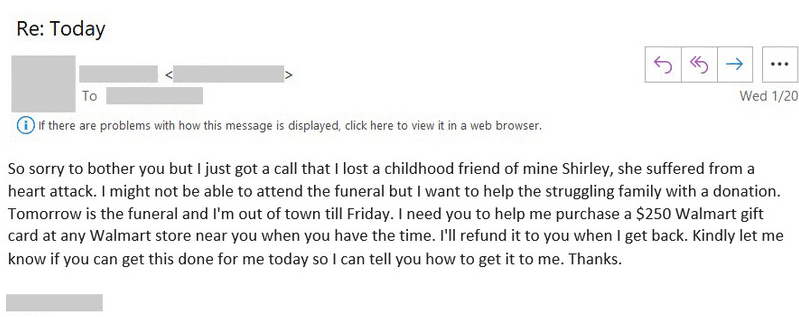
The attackers asked victims to buy actual gift cards and give them pictures of such cards in some of the instances the tech firm has posted on Twitter, pledging swift refund.
The same threat agents previously used COVID-19 lures in related BEC gift card projects, according to Microsoft.
Security analysts said that such BEC attacks have been underway for over a year in response to Microsoft’s tweets, and that colleges, along with K-12 settings, are now being attacked.
Microsoft was unable to share details about the amount of attack attempts detected. These events were not tied by the organisation to prior BEC promotions.
Organizations are encouraged to use protection tools capable of detecting domain spoofing and impersonation attempts to remain safe from this form of BEC attacks and other malicious behaviour, and to instruct workers to constantly be careful over the nature of the communications they obtain.











Leave a Reply