Kaspersky scientists noted a new malicious Android BRATA remote access tool (RAT) known as the WhatsApp and SMS messages to infect and spy with Brazilian users.
The fresh RAT was appointed based on the Kaspersky Global Research & Analysis Team (GReAT) researchers ‘ description “Brazilian RAT Android,” which found it in the wilderness in January.
Until now, scientists have discovered over 20 distinctive BRATA versions of Android apps supplied via the Google Play Store, some of which were also found in informal Android app stores.
BRATA operators used several infection vectors such as push notifications sent via websites affected, “emails supplied via WhatsApp or SMS and Google Search sponsored connections.”
However, according to researchers, the vast majority of the BRATA variants found in the wild have been camouflaged as updates to the popular WhatsApp.
After downloading and running, several fake updates would exploit the CVE-2019-3568 vulnerability to infect targeted Brazilian users ‘ Android phones.
“If a victim’s device is infected,’ BRATA’ allows its keylogging functionality to be enhanced by real-time streaming,” the scientists discovered. “Android utilizes the accessibility service feature to communicate with other apps installed in the device of the user.”
Among the features BRATA has, it enables operators to unlock the phones of their victims, collect device data, disable the device screen to execute functions in the background subreptitiously, and disinstall it and delete any traces of infection.
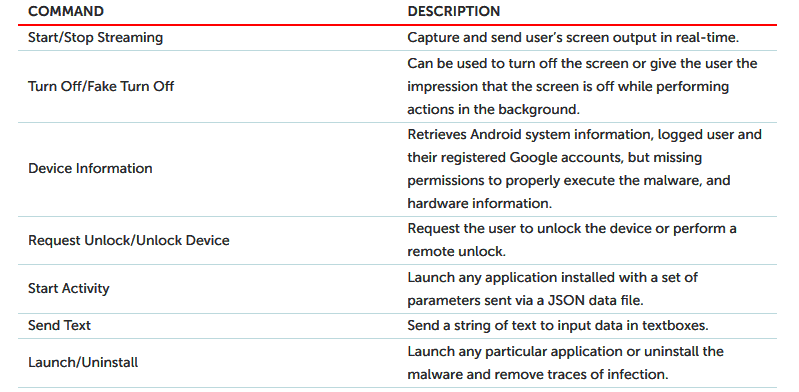
BRATA RAT capabilities
At the end of the write-up, the Kaspersky researchers provide compromise indicators (IOCs) of BRATA RAT malware in the form of a malware sample MD5 hash.
RATs are a common assault instrument
This month, Attackers used several RAT flavours, which target different objectives this month alone with the Revenge and Orcus Remote Access Trojans being targeted at governments and financial institutions, while a distinct phishing campaign used false resume attachments for the provision of Quasar RAT payloads.
The threat performers of Adwind RAT (also known as jRAT, AlienSpy, JSocket and Sockrat) assaulted utility companies last week.
Multiple Balkan entities were also targeted by ESET scientists who first detected the assaults using a combination of fresh backdoor and RAT malware, called BalkanDoor and BalkanRAT.
In early August, a fresh exploit kit distributed via malvertising was abused by the PopCash ad network, the so-called Lord EK, and was used as a njRAT payload after an Adobe Flash vulnerability was exploited.
A few days before. A few days before. Researchers from the Proofpoint Threat Insight team revealed that a fresh RAT malware known as LookBack was detected and sent through a spear phishing campaign to attack staff of the three U.S. utilities.
Credit: Bleeping computers











Leave a Reply