CafePress, a well-known custom T-Shirt and goods site, has experienced a violation of data that discloses 23 million of its customers ‘ personal information.
The users became aware of the infringement today, not through CafePress, but through Troy Hunt’s notifications I was pwned..
Having heard of a breach of CafePress data, Hunt requested the help of Jim Scott, a security scientist who had helped him in the past with other infringements, such as Evite.
“Security researcher Jim Scott is just fine. About 2 weeks ago I got notified by Troy that CafePress.com data breach was circulating and if I had seen it. At that time, the only public source of this data breach was from the data breach search engine WeLeakInfo and was not being sold as far as I know. With the help of my colleagues, I started to search for the database more thoroughly until I found it,” Scott told
Research shows that a CafePress dehashed database of 493,000 accounts is sold in hacker forums. It is not known whether this is the same infringement.
According to HIBP, in February 2019, CafePress was hacked and personal data were revealed to 23,205,290 users. This data includes email, names, passwords, phone numbers and physical addresses. This information is available.
Scott also said that half of the compromised passwords of users had been encoded into base64 SHA1, which is a very low standard algorithm. The other half of users had third-party tokens for Facebook and Amazon logins.
“It came to my attention that Troy forgot to add that passwords were also affected in this security incident when first announcing this data breach, which has now been corrected. Out of the 23 million compromised users, roughly half of them had their passwords exposed encoded in base64 SHA1, which is a very weak encryption method to use especially in 2019 when better alternatives are available. The remaining users who used CafePress through third-party applications, such as FaceBook or Amazon, had no compromised passwords.”
At the time of this writing, CafePress did not answer the queries and did not issue a statement concerning the infringement of data.
The only indication is that users of CafePress are forced to reset their password while logging into the site. There is no mention of the violation in this reset password policy.
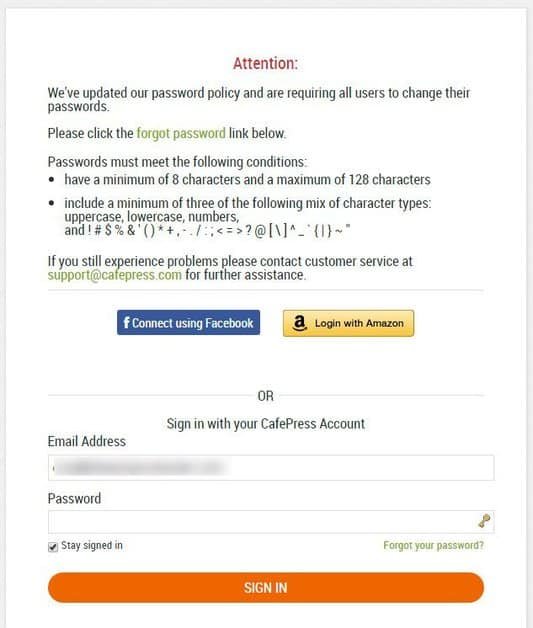
Passwords resets
Companies must do better to control their own data for their users. In the event of a data breach, the companies need to divulge this information to protect themselves adequately.
However, for the second time in a week a company has decided to reset the password for the first time. First on StockX and now on CafePress.
Password reset notifications shall be made simultaneously with infringement notifications.
Not before, not after, not before.











Leave a Reply