According to a report from IBM X-Force, attackers were observed targeting companies worldwide in the last two months with the HawkEye malware keylogger.
During April and May, a malicious campaign was launched to target business users using male spam emails aimed at organizations in numerous sectors, such as transport and logistics, healthcare, import and export, marketing, agriculture, and more. “HawkEye is designed to rob infected devices of information, but also can be used as a loader to leverage its network.
HawkEye campaigns in April and May
The malspam campaigns that disseminate the keylogger actively target business users in order to steal account credentials and sensitive data which can be used as part of taking on account or compromise attacks on business email.
In April or May, spam emails were disguised by attackers on spam servers in Estonia as messages from Spanish banks or legitimate companies, distributing both HawkEye Reborn v8.0 and HawkEye Reborn v9.0.
While the spam e-mails used generic greetings and featured bad texts and content and did not contain any company logos, “the spammers succeeded in spotting the address they had sent from the domain of a major bank.” Spam e-mails come with attachments with fake trade invoices that will drop HawkEye malware in the background when the victims open it.

Sample malspam email
The IBM X-Force analysis explains that “samples we checked reached users in Spain, the US and the United Arab Emirates for HawkEye Reborn v.9.
A mshta.exe binary dropped by PhotoViewer when the victim attempts to open the fake invoice will use PowerShell to connect to the command-and-control (C2) server and drop additional payloads of malware to infect the victims with the keylogger / stealer malware.
The malware gains persistence on the compromised system by using an AutoIt script in the form of an executable called gvg.exe that adds itself to the Windows Registry as an AutoRun entry, thus ensuring that it is automatically relaunched after each system restarts.
The IBM X-Force researchers also discovered that “the second line in the script shows a file called AAHEP.txt. This file contains all the necessary instructions regarding the actual Hawkeye keylogger functions and commands.”
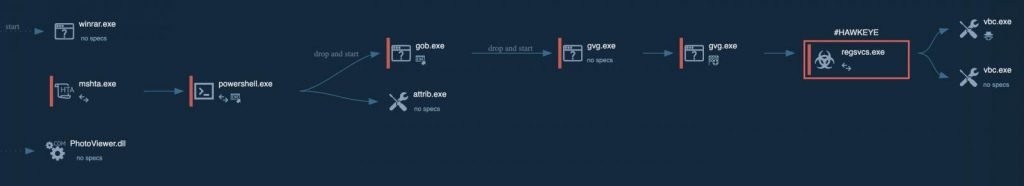
Infection process
Malspam campaigns powered by HawkEye
In the April and May 2019 lists of compromise indicators, X-Force researchers found another malspam campaign from the Turkish server “between 11 February 2019 and 3 March 2019,” with the IP address of that same Class C network.
Together with the fact that both campaigns feature very similar patterns of attack with emails dropping malware payloads disguised as commercial invoices infecting targets with an info-stealing Trojan, X-Force researchers have led them to believe that they are operated by the same threat actor.
During April, Cisco Talos also detected other malspam campaigns spreading the Hawkeye keylogger, as well as My Online Security during May, with the latter noticing that the data was either exfiltrated to the servers of another keylogger named Spytector or that the attackers used a compromised Spytector email to collect the stolen data.
Email sent by the Hawkeye Keylogger to its operators
The HawkEye Reborn v9 malware kit
Since about 2013, the HawkEye keylogger and information stealer malware kit has been in development with a multitude of new features and modules added over the years by its developers to boost their monitoring and data theft capabilities.
Hawkeye is being sold on dark web markets and hacking forums by its development team and is currently being distributed by resellers after changing owners in December 2018.
HawkEye Reborn v9, the latest version of the malware kit, can collect information through protocols such as FTP, HTTP, and SMTP from various applications that it then ships to its operators.
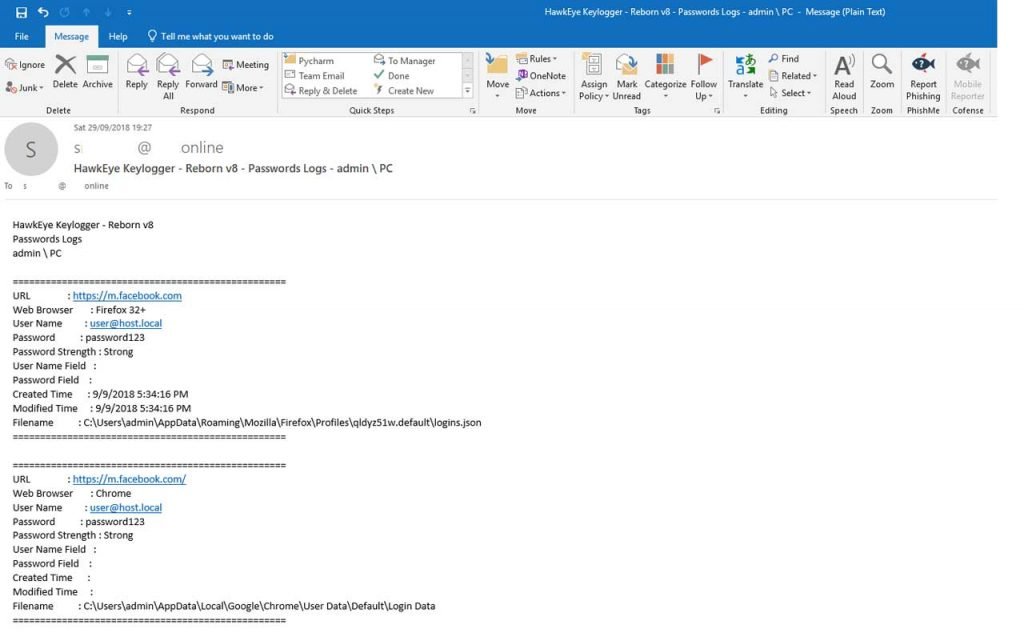
HawkEye Reborn UI
“Recent changes in HawkEye Reborn Keylogger / Stealer’s ownership and development efforts demonstrate that this is a threat that will continue to experience ongoing development and improvement moving forward,” Cisco Talos ‘ research team said in its analysis of HawkEye Reborn v9 keylogger / Stealer.
“HawkEye has been active throughout the threat landscape for a long time and is likely to continue to be leveraged in the future as long as this kit developers can monetize their efforts.”











Leave a Reply