Cisco conducted an investigation after two counterfeit Cisco switches that appeared to exploit a previously unknown vulnerability were analyzed by F-Secure researchers.
An IT organization utilized the fake Cisco Catalyst 2960-X series switches. After the counterfeit devices were found in fall 2019, F-Secure was called in to perform an investigation. After a software update the switches stopped working, which led the IT company to discover that it had been using fake Cisco equipment unknowingly.
An inspection of the two devices, which seemed to look and function just like authentic Cisco products, revealed the existence of a vulnerability which allowed bypassing secure boot mechanisms designed to protect devices from firmware manipulation.
F-Secure told that it reported its findings to Cisco, but it wasn’t able to determine whether the vulnerability also affects genuine switches.
A Cisco spokesman said via email that the company “examines the results of the researcher with priority and, if new information is found that our customers need to be aware of it and respond to it, we will communicate it via our existing channels.”
F-Secure ‘s analysis of the fake Cisco switches focused on the safety implications of using these fake devices, particularly when the manufacturer was attempting to plant backdoors.
“Although no ‘backdoors’ were found in this situation, the fact that the safety functions were bypassed indicates that the device’s security posture was compromised. It could give attackers, for example, who have already achieved code execution via a network-based attack, an easier way to gain persistence, and thus affect the security of the entire enterprise, “F-Secure said in its report.
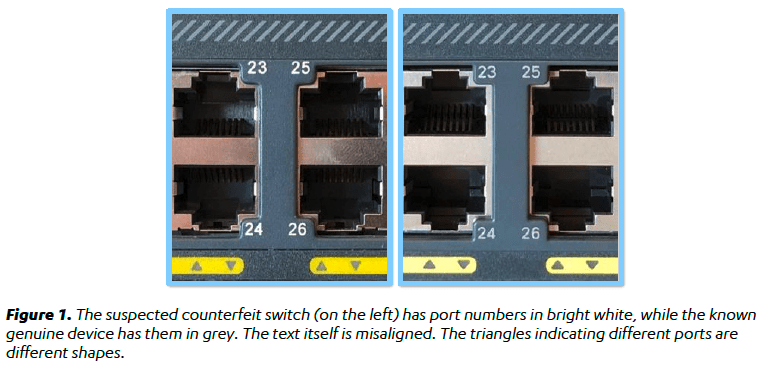
F-Secure concluded that the counterfeiters’ goal was likely to make money out of their sale, but the company warned that motivated threat actors were known to use similar approaches to open a backdoor to the systems of a company.
The manner in which the falsified equipment was created indicates that its creator either had access to Cisco ‘s proprietary engineering documentation, or “invested heavily in the complicated process of replicating original board design files based solely on genuine boards.”
Cisco has cautioned that counterfeit goods pose a significant risk to the efficiency , performance, protection and security of the network.
“We suggest that customers buy Cisco products from Cisco or through an approved partner to ensure that customers are getting genuine Cisco products that are approved. Cisco is constantly tracking the global counterfeit market to protect our customers as well as introducing a comprehensive and omnipresent Value Chain Security Infrastructure consisting of multiple security controls to deter counterfeiting,”Cisco told. Cisco also has a dedicated Brand Security unit to track, prevent and eradicate counterfeit activities. Fighting systematic counterfeiting and defending intellectual property rights are major problems facing the technology industry as a whole.











Leave a Reply