A new wave of malware Emotet distribute Nozelesn’s ransomware to hospitality-based endpoint systems through malicious word documents.
Telemetry had over 14,000 spam detections distributed around the world between 9 January 2019 and 7 February 2019 through emotet spam messages. These mass infections primarily target countries such as the United Kingdom, Cyprus, Germany, Argentina, Canada and various locations in different times.
This new campaign was initially uncovered through the Trend Micro Managed Monitoring System (MDR) where researchers discover nearly 580 similar Emotet attachment samples.
Attackers using most common e-mail techniques such as “latest invoice,” “shipping details,” “wire dispatch today” and “urgent delivery to compromise victims to click on the link or to open malicious documents attached to the link.
Having opened the attachment, spam emails contain an attached word document, a macro will execute and then eventually call PowerShell to download a malware from a remote server. In this case, spam e-mails include a attached text document Once a macro executes the attachment, Power Shell will eventually be called to download another malware from a remote server.
During the investigation, researchers found a suspect file called “How Fix Nozelesn files.htm” in the endpoint Server where an indication of Nozelesn ransomware infection was also found. Additional analysis of the root cause chain found that a malicious document file had been opened in Microsoft Word and downloaded via Google Chrome.
PowerShell.exe runs once the victims open the file to connect to a number of IP addresses to create another 942.exe file.
According to Trend Micro analysis, “Based on its behavior, the malware may have been connecting to multiple IP addresses to download another malware which it will execute in the system. In this case, we noticed that it was also continuously downloading an update of itself, contacting a new set of command-and-control (C&C) servers each time.
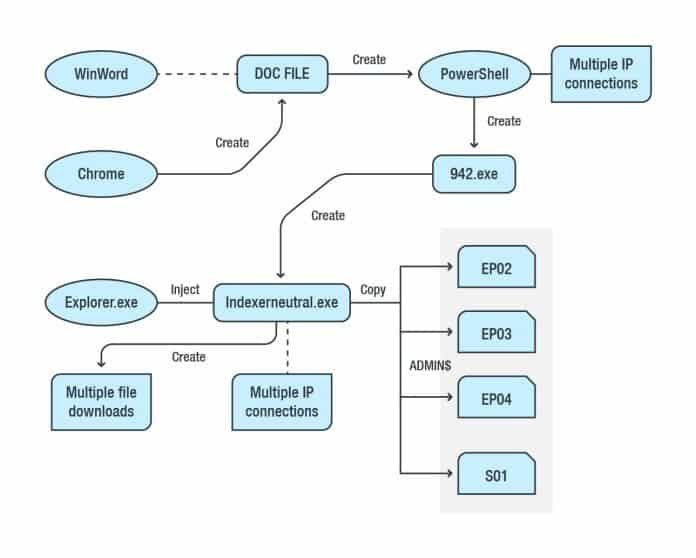
A root cause analysis of the Emotet malware infection
The secondary payload, which is very similar to the Nymaim, which is connected to Nozelesn ransomware, is then dropped. Finally, the Nozelesn ransomware was uploaded into the infected system and files in the endpoint system (server) were encrypted via shared folders.
Reference Source:











Leave a Reply