Google’s Threat Analysis Group (TAG) said that new Android zero day attacks targeting vulnerable Google Pixel, Huawei, Xiaomi, Samsung, Oppo, and Moto smartphones are being actively exploited in the wild.
This zero-day is a local privilege (LPE) kernel bug using an Android binder driver application-free flaw, which potential attackers can exploit to gain full control of unspatched apps.
“If the exploit arrives on the internet, only a rendering exploit must be combined as this vulnerability can be accessed through the sandbox,” said Google Zero Researcher Maddie Stone, the project’s researcher.
Although the problem had previously been patched in 4.14 LTS kernels without a CVE in December 2017 and the Android Open Source (AOSP) kernels of Android 3.18, 4.4, and 4.9, the vulnerability was re-introduced in later versions.
Impacts Smartphones Pixel, Apple, Xiaomi, Huawei
Stone says the CVE-2019-2215 vulnerability affects “most Android devices since fall 2018,” which need “little or no configuration per phone.” The following Android devices have been reported as susceptible in Project Zero’s bug tracker:
• Pixel 1 and 2 (and XL) with Android 9 and Android 10 preview
• Samsung S7, S8, S9
• Huawei P20
• Xiaomi Redmi 5A
• Xiaomi Redmi Note 5
• Xiaomi A1
• Oppo A3
• Moto Z3
• Oreo LG phones
Although Google’s Project Zero usually exposes vulnerabilities in 90 days, actively exploited vulnerabilities are subject to a 7-day time limit.
“After 7 days elapse or a patch has been made broadly available (whichever is earlier), the bug report will become visible to the public,” said Stone.
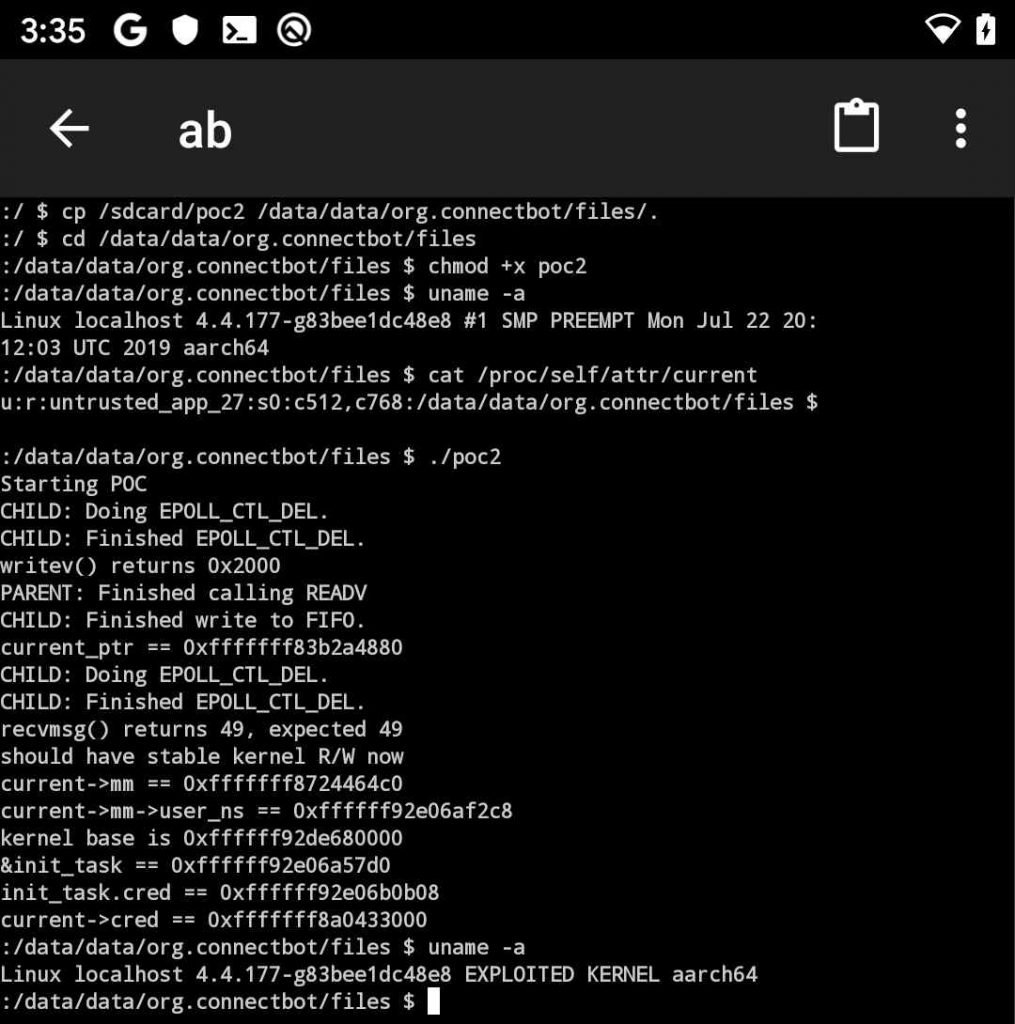 PoC exploit demo
PoC exploit demo
Allocated to the NSO Team
“The vulnerability was reportedly used or distributed by NSO Group,” a Israel-based company known for developing, manipulating and selling vulnerabilities and instruments such as the Pegasus Android and iOS spyware, says Google’s Threat Analysis Team.
Although a successful exploitation of this vulnerability could allow potential attackers to gain full control of Android devices that have been compromised, it cannot be used to compromise them remotely.
“The high severity of this problem on Android allows a malicious program for potential exploitation to be enabled by itself. Any other method, such as through a web browser, needs an additional exploit,” says an AOSP report.
“We’ve alerted Android partners, and the patch is available on the standard kernel for Android. Pixels 3 and 3a are not affected, whereas pixels 1 and 2 are patched as part of the October update on that issue”.











Leave a Reply