Serendipitous discovery reveals a new threat to owners of MySQL servers.
At least one Chinese hacking crew is now scanning the Internet for Windows servers using MySQL databases so that they can use GandCrab ransomware to infect these systems.
These attacks are rather unique, as cybersecurity companies haven’t seen a threat actor until now who attacked MySQL servers running on Windows systems for ransomware.
Andrew Brandt, Sophos ‘ Principal Researcher, and the author of a honeypot log that detected these new attacks described them in cybersguards e-mail as a’ serendipitous discovery.’
The researcher published a blog post on the Sophos website today, which details this new scan activity and its payload.
ATTACKERS TARGET RARE, BUT JUICY, EXPOSED DBS MYSQL
Brandt said hackers would scan for accessible MySQL databases which accept SQL commands, check whether the underlying server would work under Windows, and then use malicious SQL commands to file the exposed servers which they would execute later by infecting the host to GandCrab ransomware.
While most system administrators usually protect their MySQL servers by passwords, these scans seemed to be an opportunity to exploit incorrect or passwordless databases.
According to Brandt, hackers seemed quite prodigious, but they didn’t fully know if they succeeded.
The Sophos researcher tracked such attacks back on a remote server which had open directory server software called HFS, exposing download statistics for the malicious payloads of the attacker.
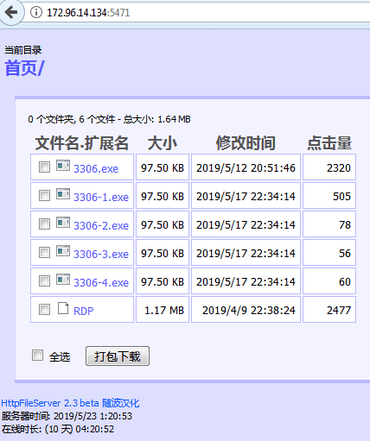
Image: Sophos Labs
“There seem to be over 500 downloads on the server in the MySQL download sample (3306-1.exe) but the sample named 3306-2.exe, 3306-3.exe and 3306-4.exe is identical to the sample file,” Brandt said.
“Together, almost 800 downloads have been made in the five days since they were placed on this server as well as more than 2000 downloads of the other GandCrab sample (approximately one week older) in the open directory.
“Although it isn’t a particularly massive or common attack, it poses a serious risk to MySQL server admissions who poked a hole in the port 3306 firewall of their database server to be reached externally,” he said.
As Brandt points out, such attacks are very rare. Hacker groups usually scan for database servers in order to infiltrate companies and steal data or intellectual property from them.
Instances, where ransomware is deployed by a group of hackers, are rare.











Leave a Reply