Microsoft said today that it has withdrawn 18 Azure Active Directory applications developed and exploited by a Chinese state-sponsored hacker community from its Azure portal.
In a study released today, the 18 Azure AD applications were pulled down from the Azure platform earlier this year in April, the Microsoft threat intelligence team said.
A Chinese hacker group known as Gadolinium (aka APT40, or Leviathan) identified recent techniques used in the paper.
The Azure apps were part of the group’s 2020 attack routine, which, due to its multi-stage infection phase and the extensive use of PowerShell payloads, Microsoft described as ‘especially difficult’ to detect.
Spear-phishing emails targeted at the target organisations, containing malicious information , usually PowerPoint files with a COVID-19 theme, started with these attacks.
PowerShell-based ransomware payloads will infect victims that have opened one of these scripts. This is where the fraudulent Azure AD software will come into play as well.
The Gadolinium hackers used the PowerShell malware to instal one of the 18 Azure AD applications on compromised devices, Microsoft said. The purpose of these applications was to encrypt the victim’s endpoint automatically “with the permissions required to exfiltrate data to the attacker’s own Microsoft OneDrive servers.”
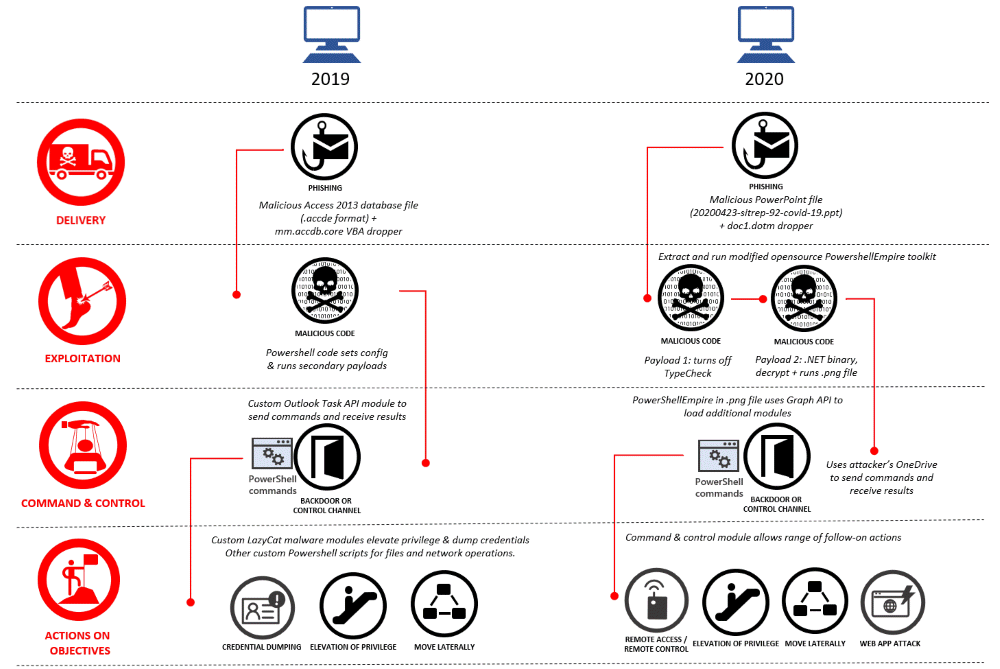
Microsoft crippled the Chinese hacker group’s attacks by eliminating the 18 Azure AD software, at least for a short time, but it also prompted the hackers to reconsider and re-tool their attack infrastructure.
Moreover, Microsoft said it had managed to take down a GitHub account that was used as part of its 2018 attacks by the same Gadolinium party. This action may not have had an influence on new activities, but it stopped hackers from reusing the same identity in the future for other attacks.
The actions of Microsoft against this Chinese hacker community aren’t an unusual event. Microsoft has regularly interfered over the last few years to eliminate ransomware equipment, whether it has been used by low-level cybercrime operators or high-end state-sponsored hacker organisations.
Microsoft has attacked the networks used by other national-state organisations related to Iranian, North Korean, and Russian cyber operations in previous interventions.











Leave a Reply