In Cooperstown, NY, the National Baseball Hall of Fame website was hacked with a malicious MageCart script that stoles payment data from clients who bought products on the site.
According to a request lodged with the California safety violation notification service, between 15 November 2018 and 14 May 2019, the National Baseball Hall of Fame website injected malicious written in its online store.
“The National Baseball Hall of Fame (“Hall of Fame”) values and respects the privacy of your information, which is why we are writing to advise you of a recent incident that may have involved some of your personal information,” the notification alerted affected users. “On June 18, 2019, we learned that some of your information could have been obtained by an unauthorized third-party that placed malicious computer code on the Hall of Fame web store (shop.baseballhall.org) e-commerce system. The code may have targeted certain personal information of customers who made a credit card purchase via the web store between November 15, 2018 and May 14, 2019.”
The data that could be robbed involves the name, email and loan or debit card data of a customer, including the CVV code.
This attack impacted only clients buying products from the website and not the museum itself. It should be observed.
You should report the situation to your credit card business and track your statements for fraudulent shopping if you bought anything from the National Baseball Hall of Fame site at https:/baseballhall.org/.
Payment data stolen by a MageCart attack
Attackers have been granted access to the website of the Hall of Fame and have injected a malicious script on the site to track and then forward the submitted payment data to the attackers.
While this script is no longer present on the website, Cyberguards was able to find the code on Archive.org in a snapshot.
As shown in the picture below, attackers have placed what appears to be a Google Analytics script at first glance. But if you look closer, the script is read from www.googletagstorage.com.
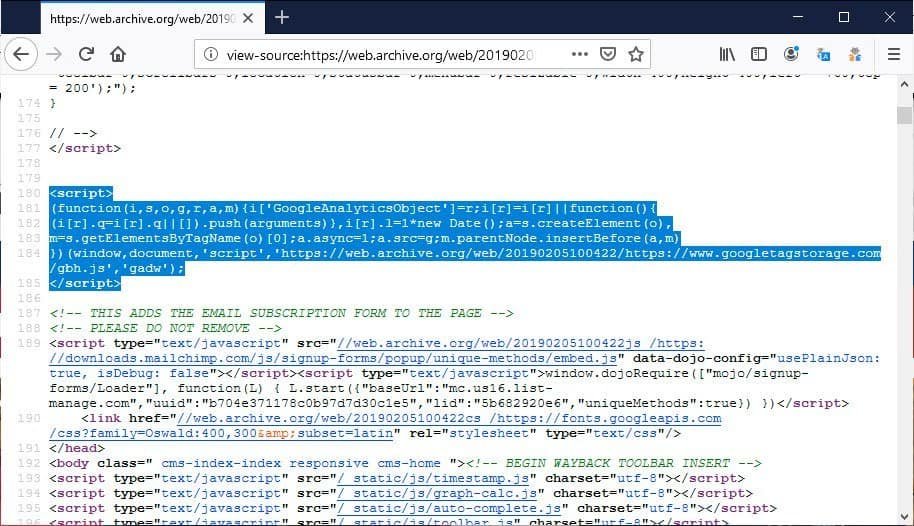
Although the domain is Google’s, www.googletagstorage.com is not currently registered and resolves its IP address in Lithuania. In the past, this same host was also used in other assaults as the IOCs on AlienVault and Xforce Exchange of IBM showed.
The script looks as if it was a lawful Google Analytics script, but if you analyze it, you can see that it monitors the shop’s billing form, which has a “co-filling form” identification.
Although no confirmation is given that this is the same group, the techniques used for this assault are comparable to the earlier mentioned MageCart Group 4 in a RiskIQ study.











Leave a Reply