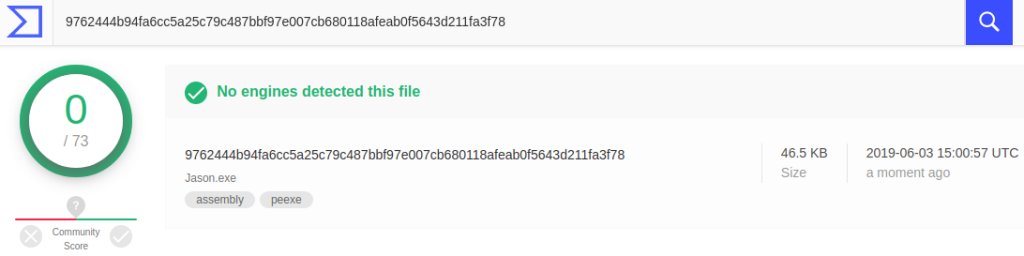
A tool used by the OilRig hacker group to hijack Microsoft Exchange email accounts was leaked online. The utility is called Jason and antivirus engines on VirusTotal do not detect it.
The release occurred on the Telegram channel of the leaker a few hours ago saying that it is used “for hacking emails and stealing information” by the Iranian Government.
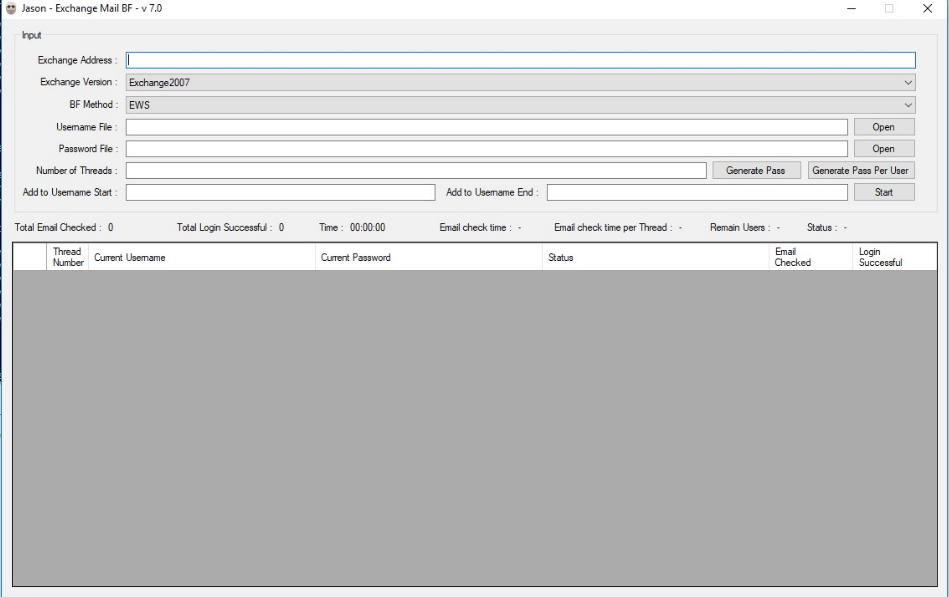
Simple tool for brute-force attack
Jason email hijacking works by trying different login passwords until the right one is found. A list with password samples and four text files containing numerical patterns supports brute-force activity.
credit: Omri Segev Moyal
Omri Segev Moyal, co-founder and research vice president at Minerva Labs, analyzed the email hijacking tool from Jason, stating that it “looks to be a relatively simple brute force attack against online exchange services.”
The analysis of VirusTotal shows that the utility was compiled in 2015. It circumvents all the detection engines available in the scanning service at the time of writing.
OilRig, also called APT34 and HelixKitten, is an Iranian government-linked group. Using the alias Lab Dookhtegan, on March 26 someone started to leak the OilRig information, its tools for hacking and contact information for personnel alleged to be working in the Iranian Minister of Intelligence and Security (MOIS).
The previous tools released by Lab Dookhtegan have been confirmed as part of the threat actor APT34/OilRig’s arsenal by experts in the infosec industry.
The direct effect of the publication of these hacking tools is the disruption of the adversary’s future activities. Security companies have already developed detections for them, but they will no longer be used for attacks.
Cybercriminals quickly gather new sources to perpetuate and diversify their business. You now have access to new tools that you can modify or use to create new malware. There are now seven tools associated with the OilRig group available to the public:
– 2 PowerShell-based backdoors: Poison Frog and Glimpse – both are versions of a tool called BondUpdater, according to Palo Alto Networks
– 4 web shells: HyperShell and HighShell, Fox Panel, and Webmask (the DNSpionage tool analyzed by Cisco Talos)
– Jason email hijacking tool for Microsoft Exchange accounts











Leave a Reply