Cloud computing, which enables users to access their data and apps regardless of location or time, has rapidly become an essential component of today’s rapidly changing business processes. It may be adjusted to any scale with just a few mouse clicks. Even if you can scale down the entire environment with just a few clicks of a button, it also saves a significant amount of money.
However, because many businesses are moving their data and apps to the cloud, there is a requirement for increased security to keep sensitive information from being compromised by cybercriminals or other types of online attackers. In recent years, the utilization of software-defined perimeters for the purpose of cloud data security has emerged as a solution that has seen a rise in acceptance among industry professionals.
Software-Defined Perimeter: How Does It Work?
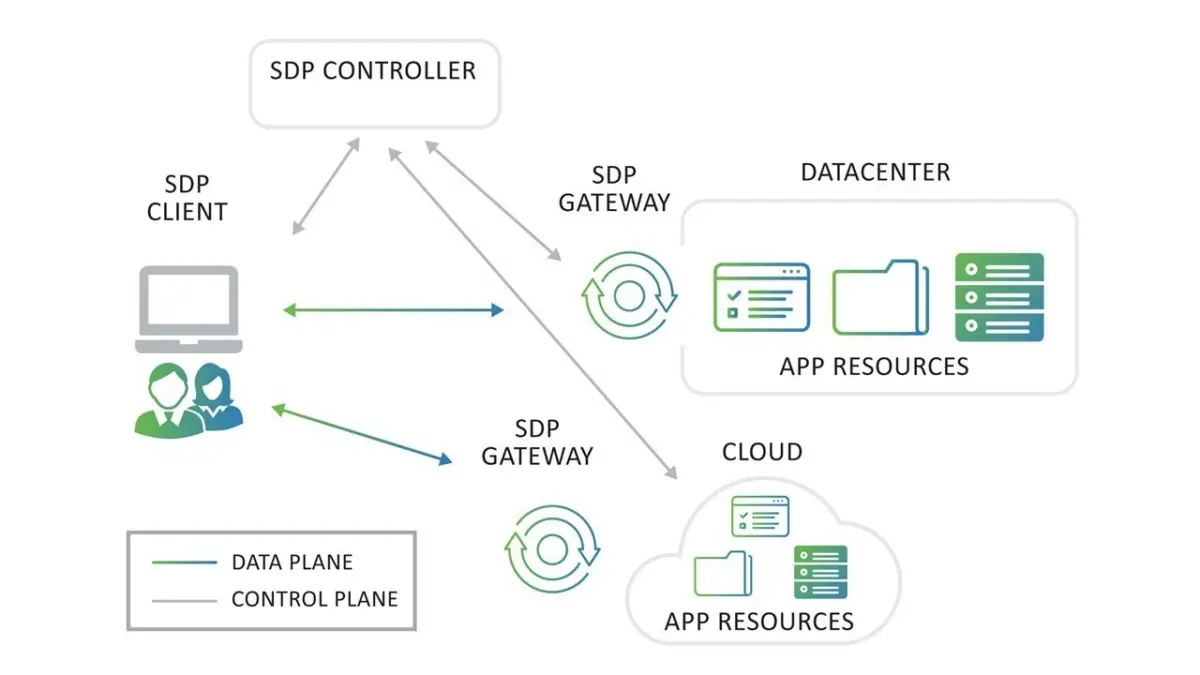
A software-defined perimeter is a network security practice in which one generates a secure perimeter around a network. This renders the network invisible to any unauthorized users or attackers, ensuring that only authorized users can access it. It operates under the premise of a zero-trust network environment, which means that every access request is first regarded as suspicious unless it can be proven otherwise.
Because of this, it is possible to acquire more control over access. There is no longer a requirement for conventional network segmentation, which can be difficult to manage due to its complexity.
In addition, software-defined perimeters provide an approach to cloud data security that is adaptable and tailored to a company’s specific requirements. This makes it possible to create virtual perimeters like geo-fencing that can be modified according to the user’s needs, including the addition and removal of any resources. In turn, you can make better use of the available resources, which in turn helps reduce expenses for various cyber security tools and the amount that may be spent after data breaches.
Software-defined perimeters function in a pattern similar to user IP address whitelisting. Unless you have been permitted to do so, you won’t be able to connect to the server. A person must be authorized to be able to connect to any of the services because it is technically impossible. If software-defined perimeters are enabled, users will only be granted access to resources after their identities have been validated and the state of the device has been evaluated.
In the event that everything is in order, the user will be verified, after which they will be linked to the network. Once the authentication is successful for both the user and the device, the software-defined perimeter will establish a unique network connection between the device in question and the server. In this scenario, an authenticated user is not logged into a broader network. Instead, that user is provided with their own network connection, which no one else can use and which only contains the services to which that user has been granted authorized access.
Therefore, even if user credentials are compromised, an attacker will not be able to enumerate the entire network or execute pivoting to get access to other components of the network, and it might even be impossible to connect because the state of the device might not have been the same as the actual user has.
It’s possible to think of this as being similar to a web server that’s simply linked to the internet. If you try to connect to this web server, it will behave like a server that is located behind a firewall. In this scenario, it will not have any ports that are exposed, it will not accept any connection requests, and there will be times when you will get the impression that it is not connected to the internet.
This is exactly the same as having an outdated server. If you do not have the authorization, you will only see a basic server when connecting to it. If you do have the authorization, then you can connect to it.
Advantages of Software-Defined Perimeters
After implementing a software-defined perimeter, an organization will gain various benefits, the most common of which are a zero-trust implementation and the right segmentation of their networks. So let’s have a conversation about them.
Zero-Trust Network
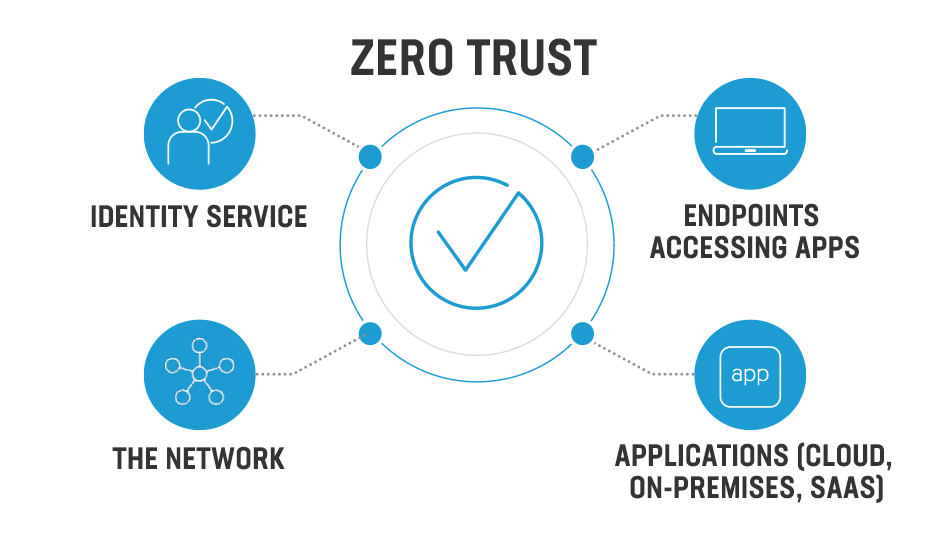
The software-defined perimeters protocol produces a network with “zero trust” because access is only provided to the user after their identification and the state of their device have been satisfactorily verified. After that, it will only build a secure connection to the resources that the user is authorized to access. Therefore, access is granted based on authentication and permission, which lowers the danger of unauthorized access and helps keep an organization’s critical data safe.
Proper Segmentation
Software-defined perimeters help establish a protected and segmented network that is cut off from the public internet. Since the web server that has this enabled will simply appear to be a simple web server linked to the internet that does not have any ports open and to which no one can connect, it will be much more difficult for an attacker to get into the network since the attacker might think that the server has a firewall which can’t be accessed.
Conclusion
Software-defined perimeters can be implemented in any infrastructure without making many changes, as it is easy to implement and has many benefits that are basic needs for today’s infrastructures. In this blog, we discussed a couple of advantages. It is different from the VPNs as VPNs need to be separately deployed for each department when you implement zero trust. On the other hand, software-defined perimeters can be implemented without hassle as they provide access to resources based on authorization. Hence it is best when implementing Zero Trust and cloud security.











FIND US ON SOCIALS