A phishing campaign using fake Stripe Support warnings has been found when trying to collect details and user identifiers of customer bank accounts from booby-trapped customer Stripe login pages.
Stripe is one of the leading online payment processors, a company that supplies internet payment logistics companies with transactions via the internet from their e-commerce customers.
It makes Stripe customers the perfect target for intimidating actors trying to access their banking information since the company manages billions of dollars each year.
Phishers have for some time now targeted Stripe customers, as users and researchers ‘ studies [ 1, 2, 3, 4, 5 ] indicate and that users should always take care as they move on their personal information over the Internet.
 Stripe phishing mail sample
Stripe phishing mail sample
Modern Tricks Still Pay Off
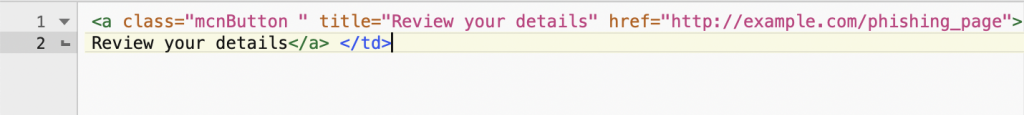
Cofense Phishing Defense Center (PDC) researchers recently noticed the Stripe phishing campaign. The attackers found that the actual destination was hidden on the built-in “Check your information” button, which redirects the Stripe clients to their phishing pages.
This known and demonstrated technique uses an HTML trick to adjust the tooltip when the mouse pointer is hovering over the reference by inserting an individual title attribute.
“The real purpose of this reference is obscured by adding a single tag title to the HTML tag, which shows the recipient the title” Check your information “when the recipient floats across the button rather than the URL,” the researchers found.
Hiding the landing page URL
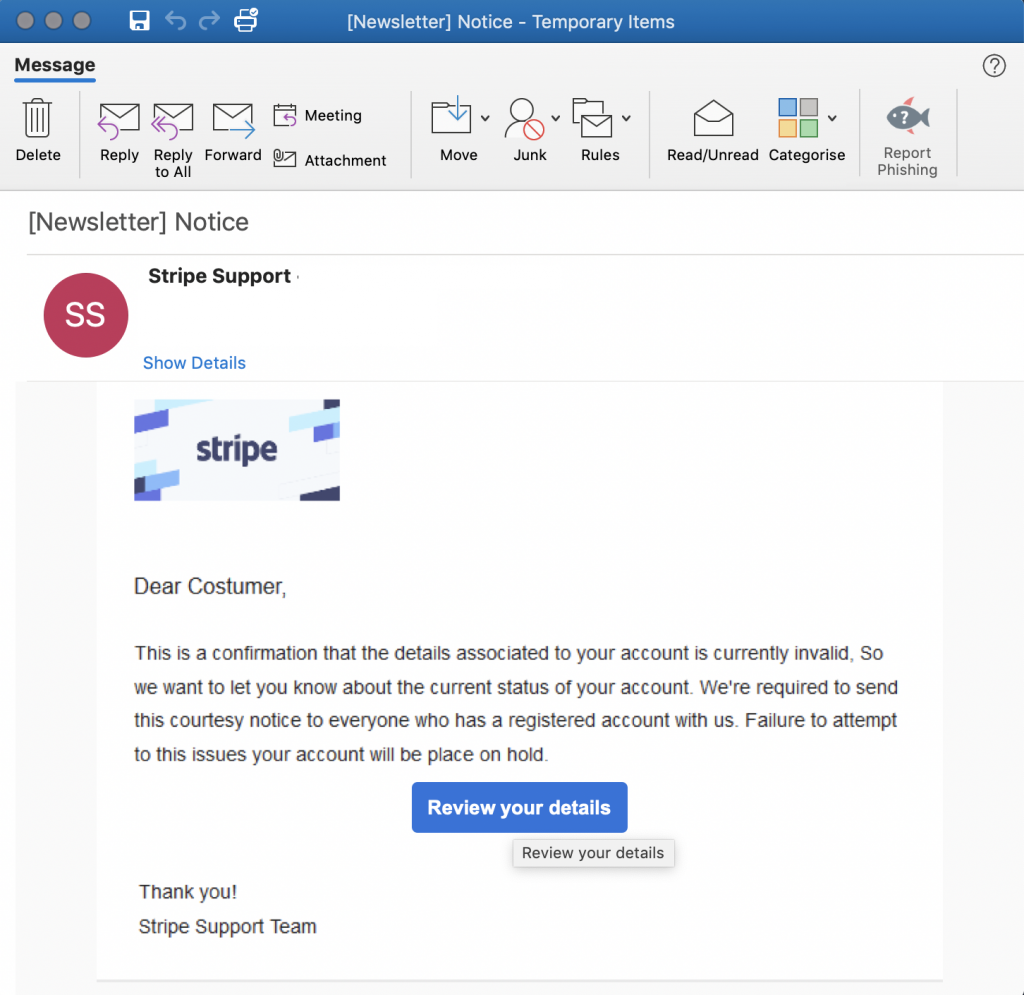
Invalid account alerts are used as phishing bait messages, with the bogus Stripe support message that’ This is a warning that the information related to your account are not correct at the moment’ and that’ Failure to try to solve these matters would bring your account on hold.’
It will send targets that fell for the assailant tricks to the cloned Stripe customer contact site to collect their user credentials, bank account numbers and telephone numbers.
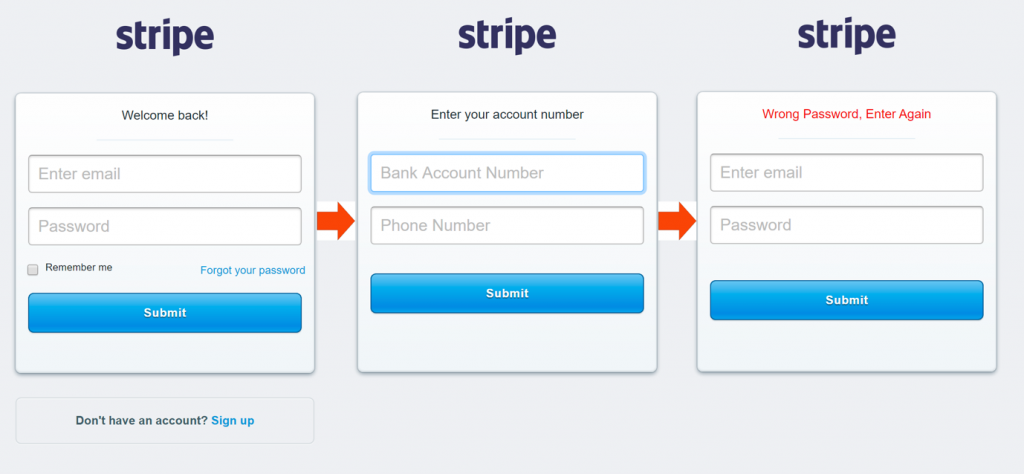
A series of fake log-in pages is used to collect data from the victims, each of which is intended to request a certain type of information, and the last to request their credentials one more time after they entered the incorrect password.
The last page shows a’ Wrong Password, enter again’ message and the attackers redirect their victims to the official login page of Stripe to avoid raising their suspicion and possibly blocking their accounts or modifying their passwords.
Stripe phishing landing page
On the support site of the organization, Stripe states that it also sends email notifications once in a while to its clients and it also offers following tips to help users prevent phishing:
• Check the web address (URL) before you click on a link. On a web browser, hover over the link and look at the URL that shows up on the bottom of your browser. Is it pointing to a page at stripe.com?
• Stripe emails will come from the “stripe.com” or “e.stripe.com” domains, and you can always reply directly to the message to get in touch with us.
• Only type your password into a website after confirming that it is the website you want, not one that was created to look like Stripe:
• Check the domain name for typos (such as “stirpe.com”).
• Check for our Extended Validation Certificate; this usually looks like a green lock next to the URL, and it lets you know that you are on the genuine Stripe website.
Stripe also suggests that consumers protect their accounts with strong passwords and incorporate a more reliable layer by allowing two-step verification. E-mails like a phishing attempt should be sent to support@stripe.com and phishing@stripe.com in full.
Phishers of Phishing Lures Juggling
Phishers have been detected by security researchers when tracking past phishing attacks, while using a wide range of other phishing techniques.
For example, infringement notices were used to prompt Instagram users to provide their credentials by filling out a’ Copyright Refusal Form’ within 24 hours to avoid suspension of their accounts.
In another phishing, assailants compromised US taxpayers via fake revenue tax refund emails with Amadey botnet worms which were also seen over a secure email gateway.
Phishers also employed CAPTCHAs to block the automated URL analysis feature of email gateways by analyzing the Microsoft account data collection landing page.
Another phishing campaign in June abused QR codes to guide targets to landing pages, essentially ignoring security solutions and controls to prevent such attacks from occurring.











Leave a Reply