On Tuesday Oracle announced a remote code execution vulnerability patch affecting specific WebLogic Server versions. The bug overrides a previously fixed defect and researchers say it is being used actively in attacks.
The CVE-2019-2729 is now tracked and deserialized through XMLDecoder for Oracle WebLogic Server Web Services. This is the same as CVE-2019-2725, patched in April, used in past attacks to supply Sodinokibi crypto-currency and ransomware. The exploit bag of the newly discovered Echobot botnet is also included.
Returns old problem
Oracle warns in its advisory that, with a gravity of 9.8 out of 10, CVE-2019-2729 “can be used via a network without the necessity to have a username and password.” The affected WeBLogic Server versions are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0.0
On Saturday, KnownSec 404 team member warned that the earlier deserialization problem in Oracle WebLogic had been circumvented. The researchers said that the vulnerability was “actively used in the wild.” They concluded that the bypass was for CVE-2019-2725, which had the same critical gravity ranking of 9.8.
Then today, a new oracle webLogic deserialization RCE 0day vulnerability was found and is being actively used in the wild. We analyzed and reproduced the 0day vulnerability that is based on and bypasses the patch for CVE-2019–2725.
Oracle credits Badcode, a member of the 404 Knownsec team to report the new vulnerability to deserialisation, along with nine other security researchers.
Interim Patching solution
The deserialization issue in Oracle WebLogic is triggered by the components “wls9 async” and “wls-wsat.”
If patching is not possible immediately, two mitigation solutions are proposed by researchers:
- delete “wls9_async_response.war” and “wls-wsat.war” then restart the WebLogic service
- enforce access policy controls for URL access to the paths “/_async/*” and “/wls-wsat/*
Both vulnerabilities in deserialization were actively exploited by zero-days when Oracle learned about them and released an emergency patch. They work the same way and their leverage leads to the same effect of execution of remote code. The difference is that the first affects all versions of WebLogic Server while the second affects Oracle’s product specific releases.
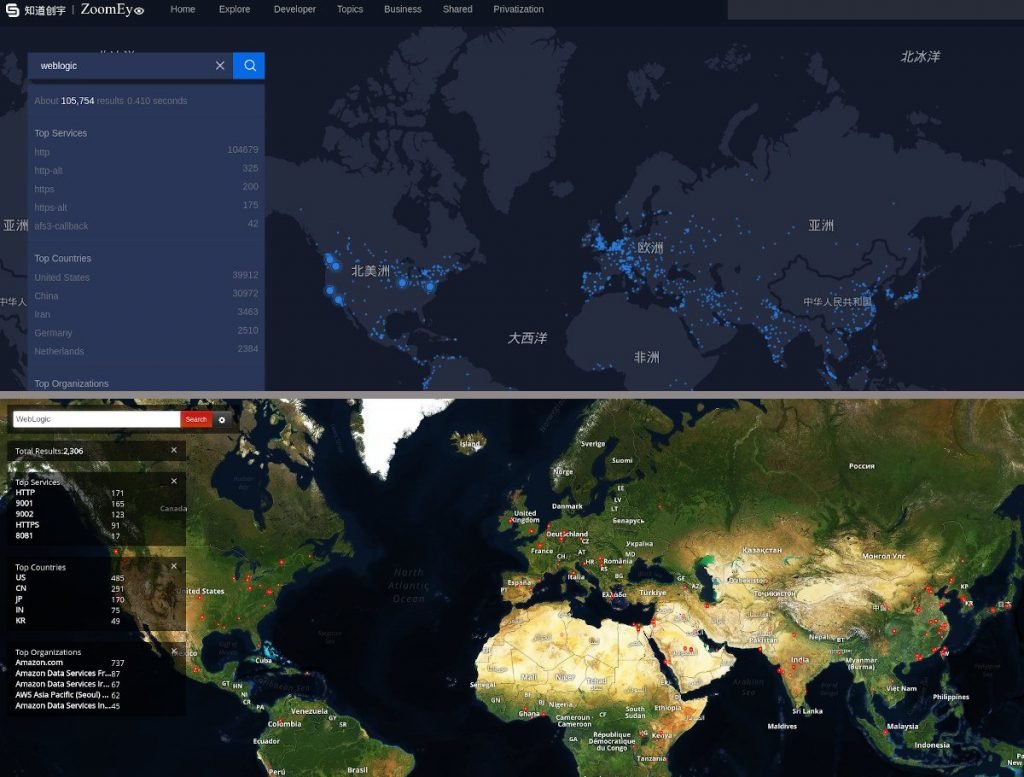
Accordingly, in 2019 nearly 42,000 instances of Oracle’s WebLogic Server are deployed, according to the ZoomEye search engine findings. A similar search on Shodan shows just over 2300 servers available online. The two engines agree that they are predominantly present in the United States and China.











Leave a Reply