The year 2021 saw some of the biggest cyberattacks in history including the SolarWinds security breach, the attempt to poison people in Florida through a water system hack, and the Colonial Pipeline attack that resulted in a six-day shutdown of operations for the largest pipeline system for refined oil products in the United States.
After several years of cybersecurity developments and global cooperation, it is reasonable to expect that defenses should have improved. Indeed they have, and so have the attacks. Cybercriminals don’t seem to run out of tricks to defeat security controls. Unfortunately, organizations also keep committing mistakes that lead to the weakening of their own security solutions.
Simply installing security controls is no longer adequate. Enterprises need a cybersecurity solution that includes continuous security validation as well as automated penetration testing. These two features ensure that possible events that may open up vulnerabilities are eliminated or at least minimized significantly.
Cybercriminals do not follow schedules
Cybercriminals attack unannounced. They compromise networks and devices whenever they please. There is no reason to be tied to a periodic security validation routine. Every minute or hour that security controls are left unchecked for weaknesses or failures is an opportunity for bad actors to put their plans to work and tweak their attacks to exploit vulnerabilities.
It is advisable to use a cybersecurity platform that supports continuous security validation, such as Cymulate, which guarantees security visibility across the full cyber kill chain to provide timely alerts on security gaps with its proactive testing of existing security controls as well as the handling of processes and the behavior of people in an organization.
Cymulate’s continuous threat intelligence-led risk assessments, which by the way can be launched out-of-the-box, make it possible to get a bird’s eye view of the threat landscape an organization is facing. With scores and color-coded indicators for the threats or vulnerabilities detected, it becomes easier for organizations to spot areas of concern and act on the most urgent threats.
Cymulate also features an Immediate Threats Intelligence Assessments dashboard, which shows a summary of the different immediate threats that have been tested by the cybersecurity platform. This summary includes a score of the threats found (higher means more urgent), the vectors, and statuses. There are also Action buttons, which make it easy to act on the different threats right within the dashboard. Additionally, there are report generation buttons, which provide a convenient way to produce reports from the immediate threats intelligence assessments.
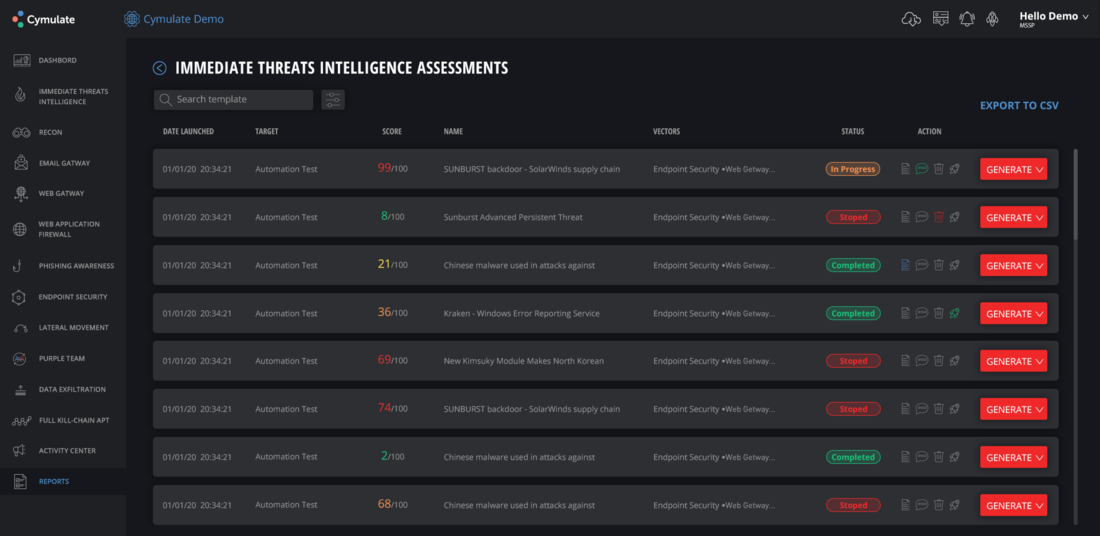
Everything here can be done automatically and continuously to see to it that organizations have real-time awareness of the cyber threats they are facing. It does not make sense to rely on reports that only come out at predetermined intervals. It might already be too late to act on a threat if organizations were to wait for the periodic reports to arrive.
Evolving threats are difficult to catch
Another reason why it is advisable to follow a continuous approach in security validation is the fact that evolving attacks are difficult to detect, identify, and block. Zero-day attacks are a constant threat for CIOs, CISOs, and others responsible for the security posture of an organization.
These attacks come in different forms. They can be email attachments, links that point to downloadable and readily installable malware, and sites that forcibly install malicious software or trick users into installing unwanted software into their systems. Examples of which include Trickbot, Emotet, Dridex, and the ransomware Ryuk.
Together with external threat intelligence including the MITRE ATT&CK framework, continuous security testing promptly detects the newest threats to prevent them from penetrating. If there are those that managed to breach the first few levels of cybersecurity, mitigation measures are quickly implemented to avoid aggravation.
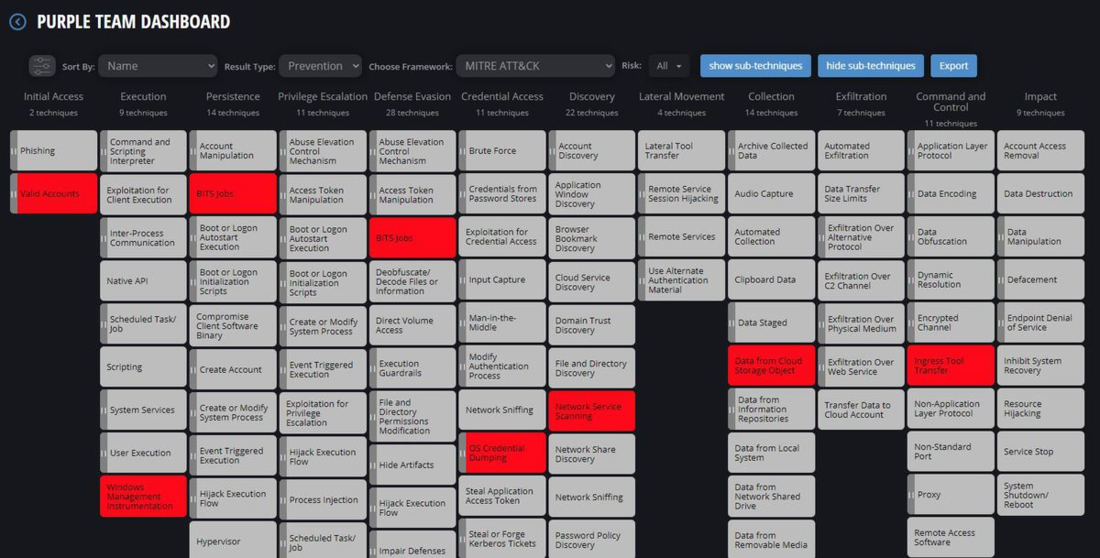
Many cybersecurity platforms already integrate MITRE ATT&CK to develop customizable cyber-attack simulation templates that are then automatically and continuously run to challenge the effectiveness of security controls across environments. This is one of the most effective ways to undertake simulations on the entire flow of advanced persistent threats (APT) and ensure that protection across the entire cyber kill chain works as intended.
Changes in the organization can create vulnerabilities
When talking about cybersecurity, it is not uncommon for organizations to focus on external threats. They prepare for the attacks launched by cybercriminals outside of the defense lines they establish. However, external threats are only a component of the entire landscape of cyber problems.
Internal issues can also emerge. These are not limited to deliberate attempts of insider bad actors to dismantle cyber defenses. The changes organizations implement or go through can also result in vulnerabilities that can then be exploited by cybercriminals.
Migrating to the cloud, for example, can be a risky process without a knowledgeable IT team directing and overseeing the process. Changes in data protocols, security policies, or the handling of the IT assets can mean configurations or modifications in processes that are advantageous to cyber attackers. These can open organizations to data exfiltration and other similar attacks.
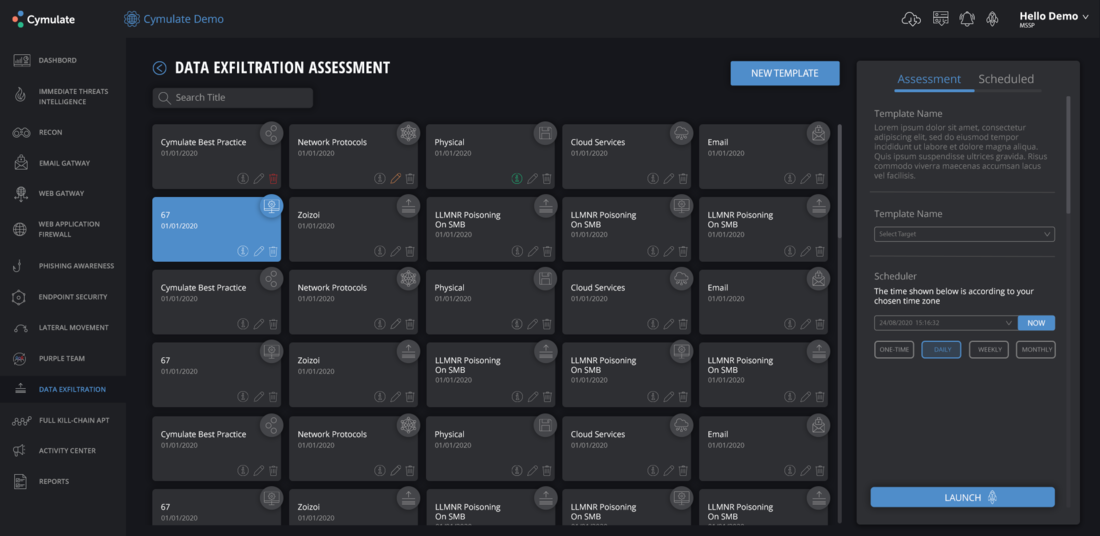
The security systems enterprises have in place may not cover the risks that can come out of organizational changes. By adopting a continuous security validation process, especially by using a dependable cybersecurity validation platform, accounting for the risks attributable to internal changes becomes automatic and compulsory.
Generating metrics and reports that fortify security posture
Continuous security testing is not only helpful in detecting and blocking attacks in real-time. It also provides the benefit of constantly generating metrics that help strengthen an organization’s cybersecurity posture.
Metrics such as the mean time to detect and respond, average time of remediation, number of systems with known vulnerabilities, and number of incorrect configurations can help organizations in more accurately assessing their state of cybersecurity and implement the necessary tweaks, adjustments, or replacements to optimize protection.
In addition to cybersecurity metrics, it also helps to have a purple teaming process or even a module within a cybersecurity platform to generate various useful threat information and insights useful in improving cyber defenses.
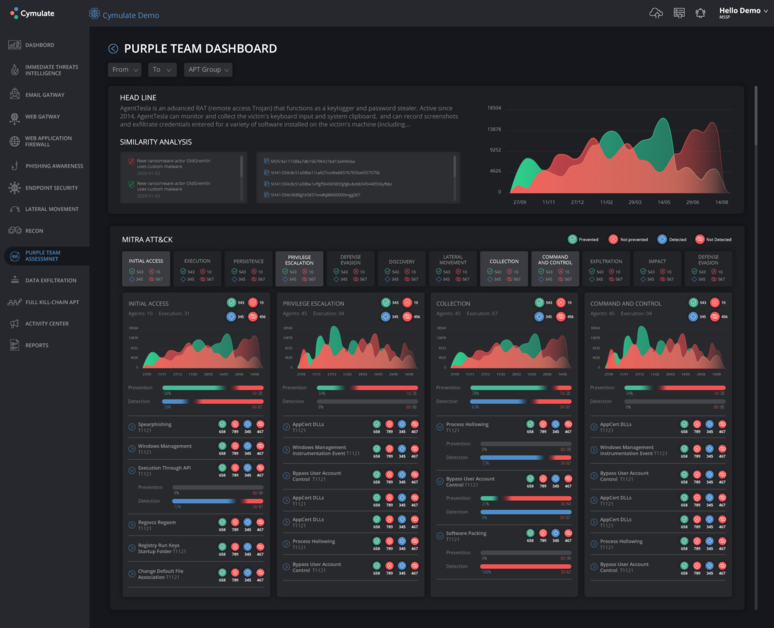
Purple teaming, which emphasizes adversarial perspectives in security validation, is a great addition to continuous security validation systems. Not only does it generate up-to-date information about threats, it also explores the extent to which attacks can go as they attempt to bypass or overwhelm security controls. With accurate metrics and adversarial perspectives, organizations can have a clear grasp of and the ability to anticipate real-world attacks.
Ensuring cyber resilience
Continuous security validation contributes significantly to achieving cyber resilience for organizations. It plays a crucial role in making sure that security controls are working properly and efficiently. It is the best approach in dealing with the unpredictability and ceaseless evolution of attacks by notoriously ingenious and persistent cyber criminals. Conducting security validation in a continuous manner with automatic tests ultimately ensures that organizations do not easily succumb to attacks, even to the most sophisticated ones the world has seen over the past years.










Leave a Reply