Vulnerabilities that researchers have discovered in VPN products primarily used for remote access to operational technology ( OT) networks will allow hackers to compromise industrial control systems ( ICS) and possibly cause physical damage.
Researchers from Claroty, an industrial cybersecurity firm, found potentially serious vulnerabilities in Secomea GateManager, Moxa EDR-G902 and EDR-G903, and eWon for HMS Networks. Several companies use the products for remote management and monitoring of ICS like programmable logic controllers ( PLCs), input / output devices, and field devices.
Claroty says the impacted VPNs are commonly used in the oil and gas and utility sectors and exploitation may lead attackers to gain access to field devices and potentially cause physical damage.
In Secomea GateManager, which enables users to connect from the internet via an encrypted tunnel to the internal network, researchers have discovered several security holes, including vulnerabilities that can be exploited to overwrite arbitrary data (CVE-2020-14500), execute arbitrary code, trigger a DoS state, execute commands as root by connecting via hardcoded Telnet credentials, and get user passwords due to weak hashing.
“[CVE-2020-14500] emerges due to the improper treatment of some of the client’s HTTP request headers. This could allow a remote exploitation of GateManager by an attacker to achieve remote execution of code without any authentication. If successfully carried out, such an attack may result in a total security breach that provides full access to the internal network of a company, along with the ability to decrypt all traffic going through the VPN, “explained Claroty.
Researchers have discovered a stack-based buffer overflow in the Moxa products which can be exploited to execute remote code. In a blog post earlier this month, Claroty identified this vulnerability, tracked as CVE-2020-14511.
As for HMS Networks’ eWON software, specifically its eCatcher VPN client, Claroty discovered a crucial stack-based buffer overflow (CVE-2020-14498) that can be abused to execute arbitrary code — and eventually take full control of the targeted computer — by making a user open a malicious website or email.
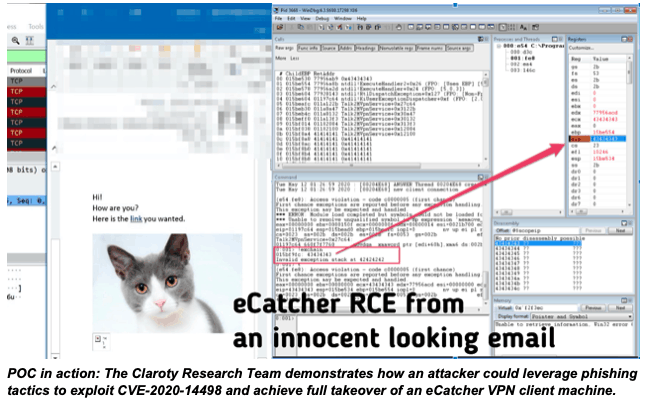
Claroty has told that attackers can use search engines like Shodan and Censys to find compromised instances of remote access servers affected. Once potential targets have been established, threat actors will remotely exploit the vulnerabilities to access devices, and ultimately the internal VPN network, without authentication.
The cybersecurity firm says it has mapped GateManager instances across the globe and found 337 live instances, of which 253 are still vulnerable to CVE-2020-14500. Claroty says that it is still trying to reach some of the companies that were found to use unpatched GateManager models.
Claroty disclosed the bugs to their respective vendors, who issued patches that would fix the flaws.
‘[Secomea] released a new version of GateManager 9.2c/9.2i to mitigate the vulnerabilities mentioned. You will consider the most up-to-date update at this time,’ explained Claroty. “Moxa recommends that users update EDR-G902/3 to version v5.5 by applying the respective available firmware updates for the EDR-G902 and EDR-G903 series. Finally, HMS Networks suggests that eCatcher upgrade users to version v6.5.5 or later.’











Leave a Reply