A fresh Trojan dropper named xHelper has been seen spreading slowly but steadily to Android since May, with more than 32,000 smartphones and tablets infected over the last four months.
Trojan droppers are instruments used by threat players to supply additional hazardous malware strains to already compromised equipment, including clickers, trojans and ransomware.
xHelper, known as Android / Trojan. Dropper.xHelper from scientists in Malwarebytes Labs who found it, was originally marked as a generic trojan dropper to be fully updated after climbing into the top ten most identified mobile malware of a safety provider in a matter of months.
DEX packages encrypted and obscured instead of APKs
In addition to the big amount of devices it was discovered on, xHelper also contains a number of further peculiarities, including the reality that it spreads using JAR camouflaged DEX (Dalvik Executable) files containing Android application code compiled.
This way of infecting fresh Android devices is quite distinctive because most mobile Trojan droppers would use an APK (Android Package) packed with an infected APK, which is then put into the Assets folder and then installed and carried out on their compromised smart phones or tablets.
The encrypted DEX files that XHelper uses as part of its infection are decrypted first and then converted into an ELF (Executable and Linkable Format) binary with the dex2oat compiler instrument, which is native to the device’s processor.
By using this complicated method, the writers of xHelper drastically reduce their opportunity of being detected and also disguise their real intentions and end goals.
The scientists have allowed an Android device to infect to evaluate the encrypted DEX file in order to export the decrypted version from their storage. This version was however disguised and contained differences in source code for all the samples found, “making it hard to determine precisely what the portable malware aims to achieve.”
“Nevertheless, it’s my belief that its main function is to allow remote commands to be sent to the mobile device, aligning with its behavior of hiding in the background like a backdoor,” says Malwarebytes Labs‘ Senior Malware Intelligence Analyst Nathan Collier.
“Regardless of its true intentions, the clever attempt to obfuscate its dropper behavior is enough to classify this as a nasty threat.”
Semi-stealth xHelper version
Stylish but not truly
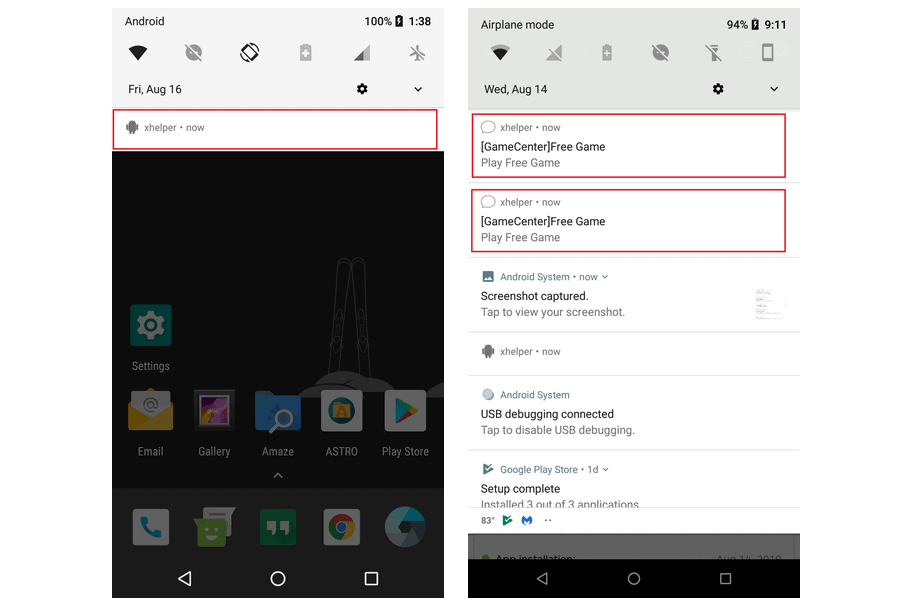
Following analysis of all samples, scientists also found that xHelper has two separate versions, one that passes its malicious duties in complete stubborn mode, and the other intended to semi-stubbornly operate through compromise Android devices while demonstrating some hints of their existence.
The stealthy version prevents any icons from being created on the infected device and does not display any sort of alert that shows its existence. The only sign that shows it is an xhelper listing in the app details.
The version with only half its capacity is much bolder, creates an xhelper icon from the notifications menu and then progressively pushes more alarms into the notifications field.
Once they have received one of these notifications, victims are redirected to websites with browser games that, although harmless, allow malware operators to receive their share of pay for the click revenues that are produced on each visit.
The vector of infection remains unknown
xHelper is certainly a danger to be taken into account, given its proven ability to rapidly infect new equipment. Malwarebytes Labs discovered it in nearly 33,000 portable phones over just four months, covering only Android phones where Android malwarebytes have been installed.
The scientists claim that every day, hundreds of fresh objectives get infected with compromise smartphones and tablets.
While the exact infection vector has not yet been discovered, “assessment demonstrates that xHelper is hosted at US IP addresses, one in New York City, New York, another in Dalle, Texas.” Thus, the investigators also add that “that this mobile infection is spread through Web redirects, it is secure to say that it is a U.S.-led attack.”
Not the first, not the last
This is not the first malware targeted at Android users that was discovered in August and that is now a malicious module in the Android CamScanner app, downloaded more than 100 million times from the Google Play Store, by Kaspersky.
Doctor Web scientists earlier found a Trojan Clicker bundled in more than 33 applications and spread across the Google Android office, which is also downloaded by unsuspecting customers more than 100 million times.
Just last week, another Android app including the open-source spyware functionality of the AhMyth Android RAT was able to bypass the automated malware protection of the Google Play Store twice in two weeks as scientists from the ESET research community discovered.
Credit: Bleeping computers











Leave a Reply