Volume of South Korean-issued records added to the dark web
Image: Gemini Advisory
The card records source remains a mystery. It could be a bank, a chain of restaurants, a provider of PoS.
South Korea’s authorities and firms should now struggle to track a major card violation after more than a million payment cards have been sold online for the last two months.
For the 890,000 and 230,000 payment cards in July and June, details were sold on the hacking forum, cyber security scientists from the Gemini Advisory told today.
Unidentified source of the violation
The source of the details on these payment cards has not been identified, researchers said. Because the card records only include CP (Card Present) details, web-based skimmers (Magecart script) are automatically excluded from online stores installed.
Possible sources of card records for crooks include (1) malware installed in stores or restaurants ‘ Point-of-Sale (PoS) systems; (2) breach of banks, payment service providers, or PoS; or (3) card skimmer equipment installed on ATMs or PoS terminals.
However, the third source seems very unlikely, as EMV cards are widely adopted in South Korea.
The Gemini Team also notes a high demand for the South Korean cyber card data from forums prior to the recent dumping which may have triggered cybercrime groups to follow South Korean targets and indirectly caused the current breach. Cards from South Korea and APAC countries are highly popular.
This large demand also explains why crooks sell this dumping card at a higher price than before.
In an email to ZDNet, a security researcher with the Gemini Advisory, Christopher Thomas, explained why cybercriminal groups have been focusing on South Korea in recent years and the Asia Pacific region as a whole.
“The demand for APAC banks ‘ payment card information was always high,” Thomas said. “While many of the financial institutions have fewer sophisticated anti-fraud systems than their Western counterparts, cybercriminals have learned that APAC cards ‘ investment returns are much higher compared with North American cards.
“Disturbingly enough, it appears that hackers have learned that South Korean payment infrastructure is especially vulnerable to attacks, which resulted in the massive breach that is currently unfolding,” Thomas added.
This case is similar to a February report this year in which security researchers of Group-IB found card records on an underground carding forum for 2.15 million US citizens.
A month later, the card dump was linked to an infringement by Earl Enterprises, a US corporation owning several restaurant chains, such as Planet Hollywood and Earl Sandwich, which has admitted hackers violating their IT network and planting PoS malware in different restaurants.
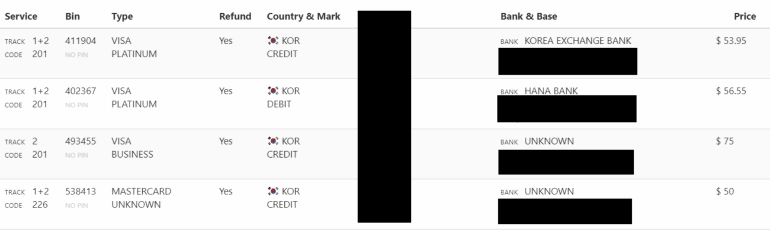
Image: Gemini Advisory (supplied)
For the time being, the mystery of the origin of this South Korean card remains unresolved. But that won’t remain a longer mystery.
As card-cloning groups start purchasing and using cards, owners begin to report fraudulent activities and, at the end of the day, authorities will track the payment processor in all victims ‘ reports.











Leave a Reply