The attack by MarioNet allows hackers to create botnets from browsers of users.
Greek academics have developed a new browser-based attack that allows hackers to run malicious code within browsers of users even after users have closed or navigated away from the web page they have been infected with.
This new attack, called MarioNet, opens the door to users ‘ browsers to assemble giant botnets. These botnets can be used for crypto-mining (cryptojacking) in the browser, DDoS attacks, malicious hosting / sharing of files, distributed cracking of passwords, creation of proxy networks, click-fraud advertising and traffic stats, researchers said.
The MarioNet attack is an upgrade to a similar concept to create a browser – based botnet described 12 years ago in 2007 in the Puppetnets research paper.
The difference is that MarioNet can survive after users close the browser tab or move away from the malicious code hosting website.
This is possible because modern web browsers now support the Service Workers API. This mechanism allows a website to isolate operations that make the user interface of a page from operations that handle intense computer tasks so that the user interface of the web page does not freeze when processing large amounts of data.
Service workers are technically an update to an older Web Workers API. Unlike web workers, however, a service worker can live and run in the background of the page once registered and activated, without requiring the user to continue browsing the website that loaded the service worker.
MarioNet (a clever “marionette” spelling) takes advantage of the power of modern browsers service workers.
The attack routine involves registering a service worker when a user arrives on a website controlled by the attacker, and then using the interface of Service Worker SyncManager to keep the worker alive after the user navigates away.
The attack is silent and requires no user interaction because browsers do not alert users or request permission before registering a service employee. Everything happens under the hood of the browser while the user is waiting for the website to load, and users have no idea that websites have registered service workers, since there is no visible indicator in any web browser.
In addition, an attack by MarioNet is disconnected from the point of attack. Attackers, for example, can infect Website A users, but they later control all Server B service workers.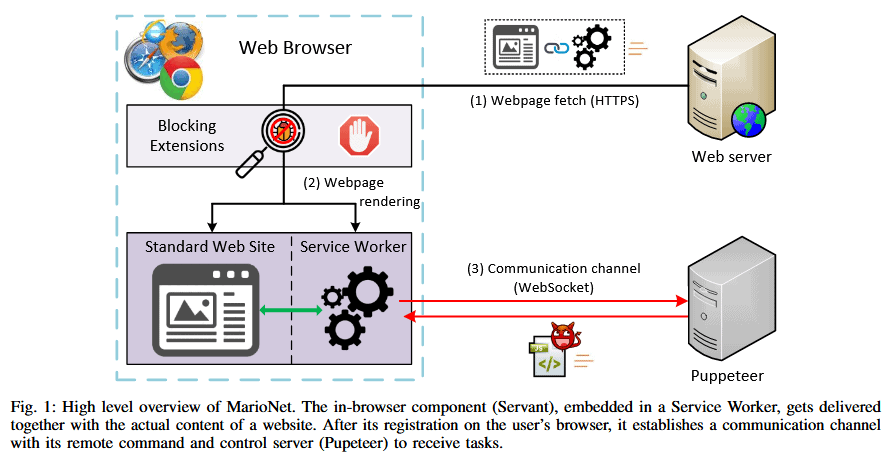
Image: Papadopoulos et al.
This allows attackers to place malicious code on high – traffic websites for a short period of time, gain a huge user base, remove the malicious code, but keep the infected browsers from another central server under control.
In addition, by abussing the Web Push API, the MarioNet attack can also persist through browser reboots. This would, however, require the attacker to obtain user permission from the infected hosts to access this API.
The subsequent botnet created using the MarioNet technique can then be used for a variety of criminal activities, such as in – browser crypto – mining (cryptojacking), DDoS attacks, malicious hosting / sharing files, distributed cracking of passwords, creation of proxy networks, click – fraud advertising and traffic stats.
Neither the original MarioNet attack nor subsequent botnet operations require attackers to exploit browser vulnerabilities, but only abuse existing execution capabilities of JavaScript and new HTML5 APIs.
For example, using infected MarioNet bots to host files requires built-in data storage APIs that are already available in browsers to store and retrieve files from the computer of a user.
This makes it nearly impossible to detect any MarioNet infections and subsequent attacks. Since service workers were introduced a couple of years ago, the MarioNet attack also works in almost every desktop and mobile browser. The only ones that did not work were IE (desktop), Opera Mini (mobile) and Blackberry (mobile).
The research team also describes methods by which MarioNet could avoid being detected by anti-malware browser extensions and anti-mining countermeasures in their research paper, and also proposes several mitigations that browser makers could take. The attack on MarioNet will be presented today at the NDSS 2019 conference in San Diego, USA.
More details on MarioNet can be found in an accompanying research paper entitled “Master of Web Puppets: Abuse of Web Browsers for Persistent and Stealthy Computation,” which can be downloaded in PDF format.











Leave a Reply