As SMS is now a common means of communication within a company, Business Email Compromise (BEC) scammers have begun moving via SMS message to their goals.
An attacker is a BEC phishing scam when he or she contacts an employee of a company and claims to be the CEO or another manager in the company. The victims are then asked to do a task for them that usually involves the employee transfering funds to an attacker’s account or buying more donation cards whose codes and PINs are then sent to their attackers.
BEC scams are traditionally done via email by spear-phishing a target and then directing victims to take different actions.. As text is now easier and more comfortable for people to perform a quick task, BEC scammers have begun switching to SMS text for their victims throughout the phishing process.
According to a new research by email security company Agari, these new attacks by the BEC start with a phishing email which asks for the mobile phone number of a target, so that the scammer can send data about a task that is needed.
After a victim answers, Agari says the attackers know that they have a victim who has fallen into a strong position for the scam.. You can change to SMS text messages to get what you need fast and efficiently. To do so, BEC mobile scammers use services such as Google Voice, which offers a wide range of features to perform several attacks on a U.S. telephone number.
The use of a service such as Google Voice makes operations against multiple targets easy for scammers to perform at once by sending the texts on the desktop website.
Once the target is communicated they can quickly send it to a local shop and buy gift cards. You then ask the goal to send the scratched codes via text back to you. The use of SMS texts makes it easier because the abusers can ask the victims not to type in photos of the scratched code.

SMS Message via Google Voice
“Once a recipient replies with their cell number, the actor is immediately placed in a strong position. They’ve minimized the risk of the initial display name deception being noticed, and they have established a method of communication that, by its very nature, places greater expectations to make a more instantaneous reply than that of its email counterpart. In terms of operational security, the scammers have not increased their risks of being identified by any tangible amount. Even if the gang was operating from a country other than the US, it costs no more than a few dollars to set up a temporary US-based number, and there are many legitimate services which provide numbers relating to any state, and even any country, available both online and on Google and Apple’s respective app stores. “
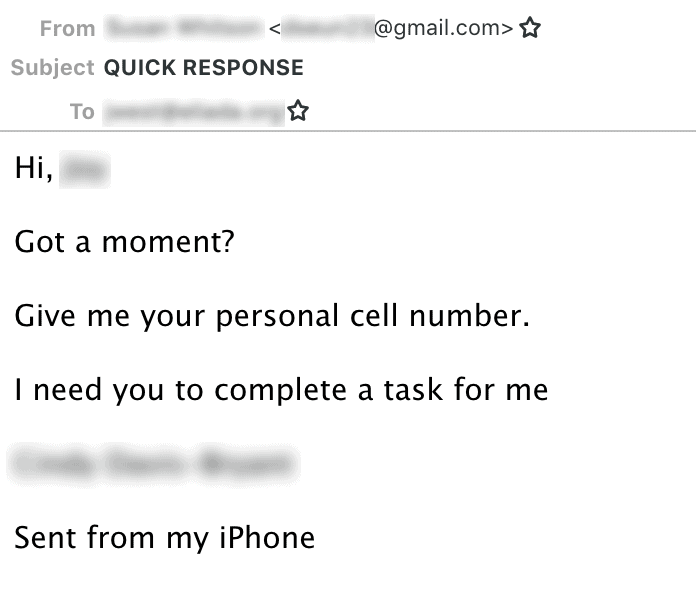
Phishing directing a target
Once the attackers have codes, they convert them quickly to bitcoin with online markets like Paxful. After converting the gift card into bitcoins, other services can be used to wash the bitcoins into a fiat currency.
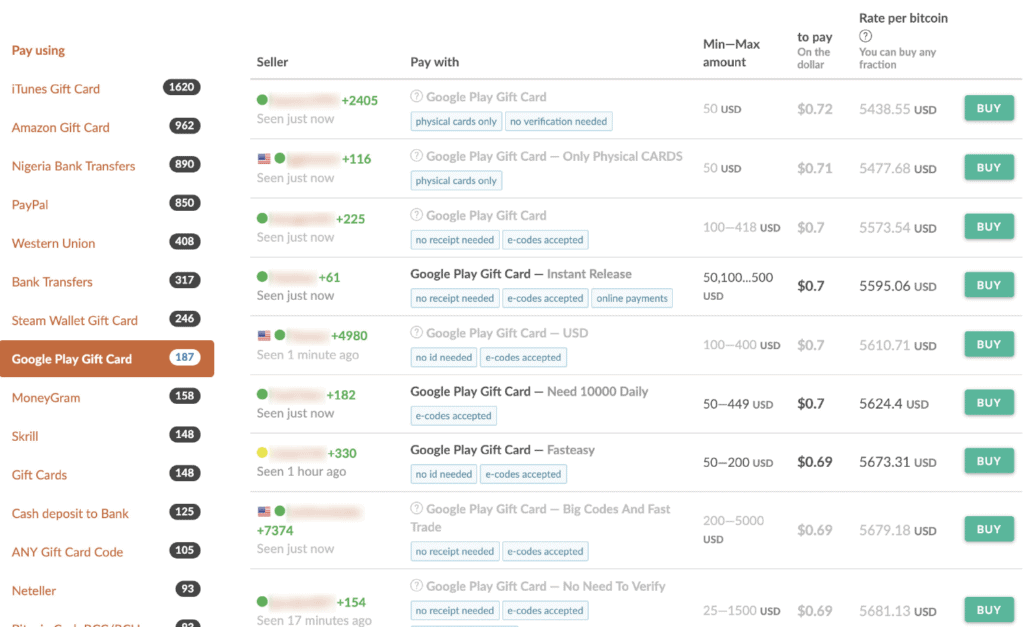
Source: Agari (supplied)
“Having access to a US number also enables the actor to create a Google Voice number, which still prove to be extremely popular with non-US based cyber-gangs. Features such as being able to create personalized greetings that can be assigned to specific callers makes the use of multiple personas easy to manage. You can also send and receive SMS messages directly from a computer, allowing the actor to remain within the environment from which they run the majority of their operations. There’s also the ability to record voice calls, and voicemails are automatically transcribed and forwarded to you contained within an email, which allows the gang to keep a detailed record of what has been said, helping to avoid any costly mixups. “
It’s important for employees to be properly trained to react and report e-mails requiring any financial task to protect themselves against such attacks.
In addition, the employees should confirm any request or other monetary transaction to transfer funds. This confirmation should not be made by e-mail if the account is compromise, but by calling and requesting the person who supposedly sent the e-mail.
Business insurance cannot cover BEC scams BEC phishing scams have become the nightmare for corporations that are liable to lose substantial income which may not be covered under business insurance policies.
For instance when Apache Corporation was tricked out of 7 million dollars due to a BEC attack, a judge held that the insurance policy was not covered, since they sent the money to the wrong bank account for the legitimate invoice. On the other hand, when the U.S.
Tooling Center had been scammed from $834,000, the judge ruled and declared that it had been covered by its policy because it was computer fraud.
Due to different interpretations of the court policies, it is important that business not only prevent such types of scams, but also ensure that their insurance coverage covers BEC attacks in particular.











Leave a Reply