A number of phishing campaigns aimed at hundreds of people in the Middle East and North Africa.
The aggressor targets HRDs, journalists, politicians. Amnesty International has published a report on several campaigns involving self – described “secure email ” services, such as Tutanota and ProtonMail, and another campaign aimed at bypassing the two – factor authentication procedure.
Crafted Phishing Sites–Secure Email Providers
The phishing campaign focused primarily on popular secure email providers such as Tutanota and ProtonMail. Threat actors used a well crafted phishing page–by acquiring the tutanota[.]org domain, while the service provider ‘s original domain is tutanota[.]com.
A phishing attack is one of the dangerous social engineering attacks that lead to a victim’s username and password being stored on an attacker’s machine and subsequently reused. Amnesty also noted that the attackers registered a phishing site protonemail[.]ch as an original valid protonmail[.]ch website.
Phishing campaign bypass 2-Factor authentication
When users enter login credentials in the fake pages, the credentials are stolen by attackers. Google and Yahoo–Phishing Campaigns The targeted phishing campaign designed to bypass the two – factor authentication of the attacker and the campaign likely to be the same.

Attackers used a crafted phishing email from an invitation to edit documents on Google Drive or a call for Google Hangout calls. “We have seen less sophisticated tricks in social engineering in this case. This attacker most often used the common” security alert “scheme, which involves falsely alarming targets with some fake notification of a potential account compromise, reads Amnesty’s report.”
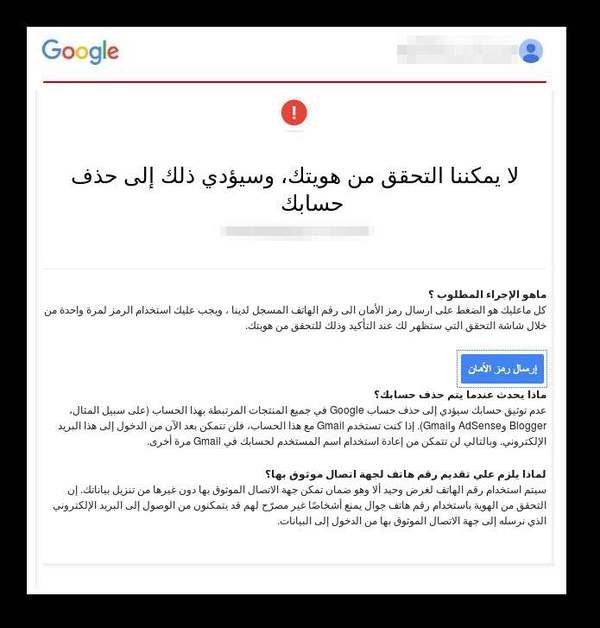
The phishing pages contain a link that redirects to a well-designed and convincing Google phishing website designed to reveal its two – step authentication code to victims. Once the victim has logged in on the phishing page, they will be forwarded to another page that has sent a 2-step verification code, and once the victims have submitted the 2-step verification code, they will submit a form requesting us to reset the password for our account.
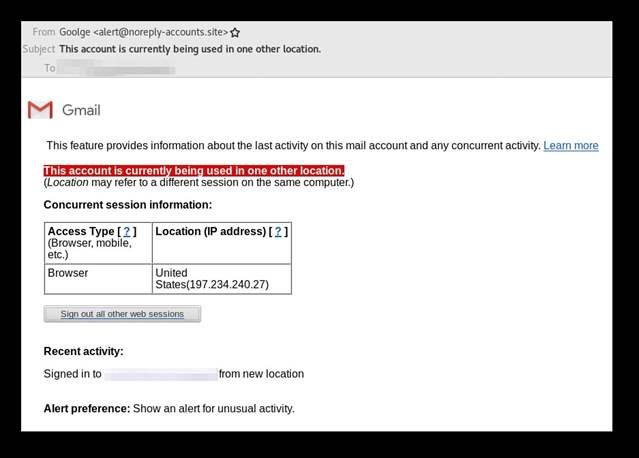
After that Amnesty noticed a change in the password was actually issued by the attackers ‘ Windows computer, apparently connecting from an IP address that Google is geo-locating in the USA. The same applies to the Yahoo account, which also set up two – factor authentication using the phone number.
How to maintain security?
1. Have a unique email address.
2. Do not open connections without correct validation.
3. Don’t open volunteer e – mails.
4. Use Spam Filters & Gateway Antispam.
5. Never answer spam emails.











Leave a Reply