A vulnerability has been found in Check Point’s Endpoint Security Initial Client Windows software that allows prospective attackers to increase privileges and code execution using SYSTEM privileges.
The CVE-2009-8790 privilege scale safety defect allows attackers to use system privileges and avoid anti-malware detection by bypassing whitelisting, a technique frequently used to avoid the execution of either unknown or possibly malicious applications.
Threats frequently exploit this kind of vulnerability at the later point of their assaults, following infiltration of the target machine and increased permission to create persistence and to compromise the target machine further.
Check Point Security is a software which includes various modules including information and network security, sophisticated threat avoidance, forensics, and remote access VPN solutions, with sections of the software being run as a Windows service that offers high-level NT AUTHORITY\SYSTEM permissions.
Arbitrary loading of unsigned DLLs
SafeBreach Labs safety researcher Peleg Hadar discovered that a safety problem “can be utilized to increase privilege and persist by loading a non-signed DLL arbitrarily into one of the Windows services used with the Check Point Endpoint Security software.
The vulnerability is due to the absence of secure DLL loading due to the use of a uncontrolled search path and the failure to validate the DLLs that are loaded by Hadar with digital certificates.
The investigator found that the Checkpoint Device Auxiliary Framework Service— one of the facilities used by target software with SYSTEM privileges and an executable signed with Checkpoint — is trying to load a missing DLL named atl110.dll from several folders into the Windows PATH environment variable.
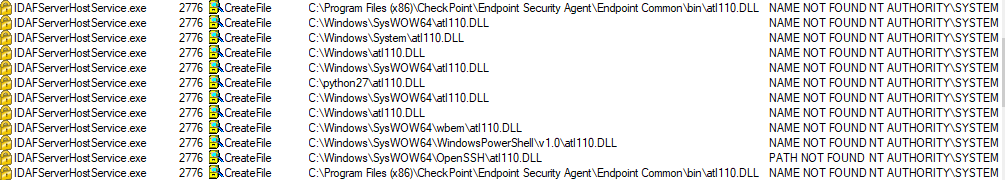
One of the directories that the service examined was C:/python27, a folder with an access control list (ACL) that provides write permissions to any authenticated user.
This enables the investigator to load unsigned DLL rights after loading them as a regular customer, with the end lead that the code has been performed within a method that was NT AUTHORITY\SYSTEM signed by Check Point.
On 27 August, after the vulnerability disclosure document sent by Hadar on 1. August, Check Point patched this vulnerability by releasing Endpoint Security Initial Client for Windows version E81.30.
Check Point Endpoint Security Initial Client for Windows before version E81.30 tries to load a DLL placed in any PATH location on a clean image without Endpoint Client installed. An attacker can leverage this to gain LPE using a specially crafted DLL placed in any PATH location accessible with write permissions to the user. – Check Point
This is Hadar’s third local privilege escalation vulnerability to a security vendor in August, when he found two more vulnerabilities affecting Trend Micro’s Password Manager and Bitdefender Antivirus’s free version.
Both could be used by attackers for persistently loading and executing malicious payloads and possibly preventing detection during subsequent phases of an assault.
Following receiving HADAR disclosure reports, Trend Micro and Bitdefender have patched security flaws (tracked as CVE-2019-14684 and CVE-2019-15295), with users receiving updates automatically built into the two apps.
Credit: Bleeping computers
Reference Source:











Leave a Reply