Cloudfare blocked attempts to exploit a highly critical vulnerability discovered in the Drupal Content Management Software (CMS) on February 20 using Web Application Firewall (WAF) rules designed to protect the websites of its customers from being compromised.
The websites affected by the vulnerability tracked as CVE-2019-6340 are those that have turned on the Drupal 8 core RESTful Web Services (rest) module and also allow PATCH or POST requests; according to the security advisory from the Drupal project team.
In order to avoid having to ask each of their customers to update their installations after Drupal released a patched version on the same day, Cloudfare “identified the vulnerability type” within 15 minutes and “were able to deploy rules to block the exploit well before any real attacks were seen.”
The exploit
As the release announcement of Drupal explains, a site will be affected if: it has enabled the Drupal 8 RESTful API
48 Hours After Vulnerability
After an in-depth analysis of Drupal’s patch, the security team of the company discovered that a potential exploit would be based on deserialization that can be abused using a maliciously crafted serialized object.
The worst thing was that potential attackers were able to exploit CVE-2019-6340 without authentication requirements to modify or delete all data on the system. After several tweaks, Cloudfare finally used a WAF rule that was named D0020, and was very effective when attackers tried to exploit the extremely critical vulnerability present in unpatched Drupal installations were automatically blocked.
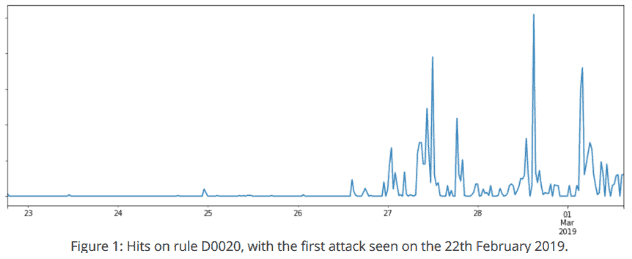
Source: Cloudflare
Cloudfare says, “The rule was already deployed in’ drop’ mode when our first attack was observed around 7 pm UTC on Friday, February 22, 2019, and has matched zero false positives to date, less than 48 hours after Drupal’s announcement.”
While threatening actors were firstly investigated only by remotely calling commands such as phpinfo and executing trial payloads for vulnerable Drupal installations, the attacks soon began to attempt to drop backdoor payloads designed to help crooks maintain access, even if the server was later patched.
The pattern that we have seen here is quite typical of a recently announced vulnerability.[…] This vulnerability was armed within two days, but that is by no means the shortest time frame that we have seen,» Cloudfare concludes.










Leave a Reply