23 Web applications, CMS and forums Projects Impacted includes Drupal, Concrete5, Composr, SilverStripe, ZenCart, and others.
A team of South Korean academics discovered 30 bugs in the file upload processes used by 23 open-source web applications, blogs, shop builders, and content management systems (CMSes) through the use of an automated testing toolkit. Know complete details about file upload vulnerability here.
These types of vulnerabilities enable hackers to manipulate file upload forms while present in real-world web apps and to plant malicious files on the servers of a victim.
Such files may be used to execute code on a website, compromise existing security settings or act as backdoors, allowing full control of a server by hackers.
ACADEMICS developed their research tool
Utilizing FUSE, a new automated penetration testing framework designed to expose UFU (unrestricted file upload) and UEFU (unrestricted file upload) vulnerabilities in PHP applications, both file upload vulnerabilities have been uncovered.
The research team said they studied previous file upload vulnerabilities while developing FUSE, and established the eight most common patterns and strategies of manipulation.
FUSE consists of these eight types, together with five new variations created by the research team (see the table below for M5, M7, M9, M10, and M13).
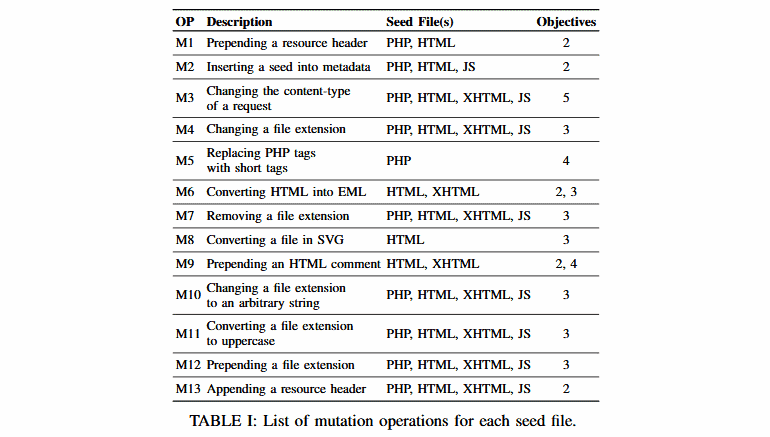
The research team said they picked the 33 most popular web apps since they developed FUSE, including the likes of forums, CMSs, consumer goods and online store builders.
The Korea Advanced Institute of Science and Technology Constitution (KAIST) and the Electronics and Telecommunications Research Institute (ETRI) researchers said that they had tested FUSE individually on the latest versions (in February 2019, at the time of the tests).
The researchers used a set of automatic requests to bypass file upload mechanisms in the 33 web apps to plant different types of malicious files (PHP, JS, Javascript, XHTML, htaccess) inside one of the checked web apps.
Scientists at KAIST and ETRI said the experiments uncovered 30 file upload vulnerabilities impacting 23 of the 33 applications they studied.
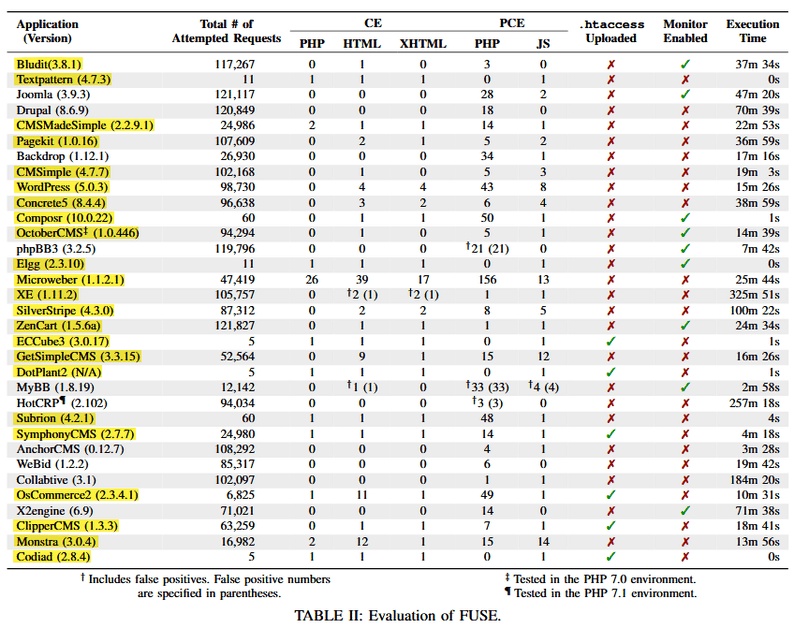
The researchers clarify that some vendors did not give priority to updates or declined to fix. Because 4 of 30 bugs need admin access to exploit and other projects did not see as a risk because an admin hacker can always mask a server through legible CMS apps.
Nevertheless, although KAIST and ETRI researchers mentioned the web apps having vulnerabilities, they did not list the ventures were fixed and were not— seeking to avoid attacks on web apps that did not yet ship a fix.
“FUSE: Finding File Upload Bugs via Penetration Testing,” and available for download in PDF format from here and here.










Leave a Reply