Fix planned for next week, with the release of Firefox 68.
Mozilla has announced today a final solution to this long-pressure issue after more than six months of constant issues with antivirus software interference with Firefox’s configuration and certificate store only for crashes of HTTPS websites.
The browser automatically enables a preference about: Config which reduces the chances that antivirus software crashes an HTTPS page, according to Mozilla Certificate Authority Program Manager Wayne Thayer, starting with Firefox 68.
The preference is”security.enterprise roots.enabled.” The browser starts with Firefox 68 and truly detects a “Man-in-the-Middle” TLS error, a typical antivirus software error which attempts to (and doesn’t) intercept an HTTPS website connection.
When this setting is enabled, Firefox will automatically import all root certificates added to the operating system’s root default certificates.
These additional root certificates are generally those installed by other applications, including antivirus.
Since Firefox uses its own root certificate store with its “authorized certificated” list which is distinct from the operating system-managed list, antivirus software should add its Firefox certificate to allow HTTPS traffic in Firefox to be intercepted, malware or bad URL to be checked.
However, installation errors and many other problems can occur which lead to Firefox showing a typical MITM HTTPS (TLS) error page, such as the one above, when an antivirus has botched the root of Firefox.
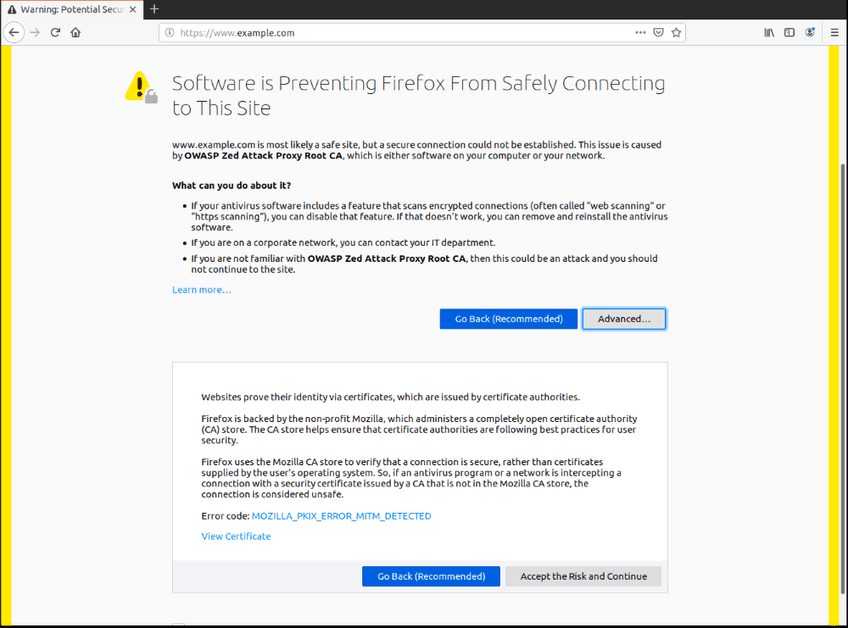
Image: Mozilla
According to Thayer, the number of errors generated by antivirus products in Firefox has increased since Firefox 65 was released last winter.
The errors were so grave that Mozilla had to stop the Firefox 65 roll-out to address the constant errors generated on systems that installed AVG and Avast antiviruses.
Other errors occurred later due, but for the same reason, to other antivirus vendors.
Thayer said that the Firefox devices were considering adding an’ fix it ‘ button to the error page at one point so that users can press it so that they can automatically enable’ company roots’ to be set so that they can automatically import the’ additional’ root certificates from OS root stores into the private list of Firefox.
Firefox engineers dropped the idea button, but now instead opt for an automatic solution.
“When Firefox 68 begins with a MITM error detection, Firefox automatically switches on’ enterprise roots’ and retries the connection,” Thayer said.
“If the problem is fixed, then the company roots preference will remain enabled (unless the user manually sets the preference ‘ security.enterprise roots.enabled’ to the wrong’).’ We also recommend that antivirus vendor allow this preference (altering prefs.js) instead of adding its root CA to its root store.
The Mozilla engineer also expressed concerns that importing root certificates automatically from the root OS store into Firefox is not a security hazard to the browser, as some users may worry.
“Every user or software that can add a CA to the OS can almost certainly add the same CA to the root store of Firefox,” he said. “Since only CAs that are not included with the OS are imported, Mozilla retains our ability to set and enforce the highest standards in the industry on publicly trusted CAs that Firefox standardizedly supports.” “Shortly, the changes that we make meet the goal of making it easier to use Firefox without sacrificing security.”











Leave a Reply