Researchers noticed a new cyber attack wave of Russian speaker hackers who use the armed TeamViewer to jeopardize government network systems and gain full control over them.
Teamviewer is the best-known tool for remote desktop control, desktop sharing, online meetings, web conferencing and file transfer.
Based on the entire infection chain and the instruments designed and used for this attack, subterranean activities make the researchers believe that the attack was carried out by a financially motivated Russian-speaking hacker.
Recent malicious campaign continually uses TeamViewer to provide powerful malware that Steals sensitive data and money from diverse government and financial networks with malicious Team Viewer DLL.
Weaponized TeamViewer Infected Chain
The initial stage of the infection chain starts by sending a spam mail to the attached malicious XLSM document containing integrated macros in the “Military Financing Programme.”
As the US Department of State, it is a well-crafted malicious document that is a top secret to persuade the victims to open it.
Once the victims open the macro decoy document, the XLSM document extracts two files from the hex-encoded cells.
First is a legitimate AutoHotkeyU32.exe program, the second is an AutoHotkeyU32.ahk that is an AHK script for communicating with the C&C server and downloading and executing the additional script.
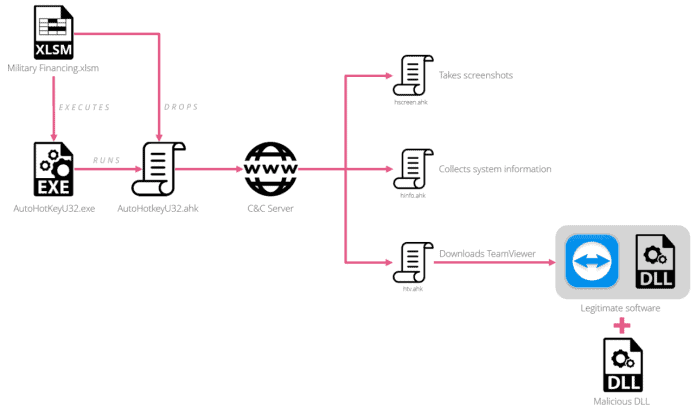
There are three malicious AHK scripts which can carry out different activities,
- hscreen.ahk: Takes a screenshot of the victim’s PC and uploads it to the C&C server.
- hinfo.ahk: send username and computer information of the victim to the C&C server.
- htv.ahk: download TeamViewer malicious version, run it and send the C&C server login credentials.
In this case, threat protagonists using the TeamViewer DLL side loading technology (htv.ahk) and this technique allows attackers to add more functionality to the TeamViewer.
Use this technique to prevent attackers from seeing the TeamViewer interface and to save current session credentials of TeamViewer to a text file, enabling them to transfer and execute additional EXE o DLL files.
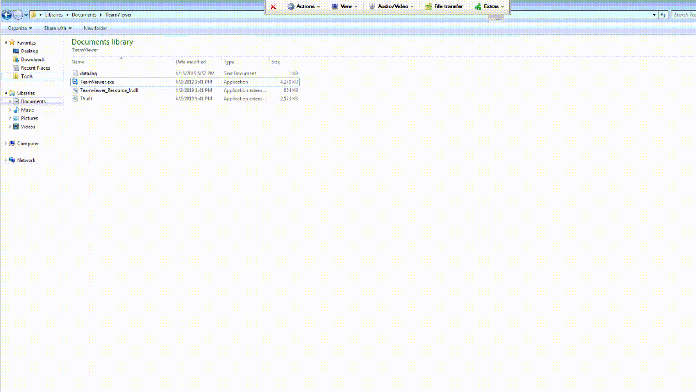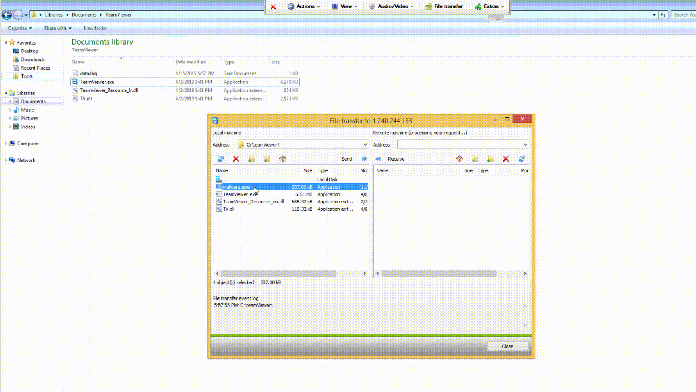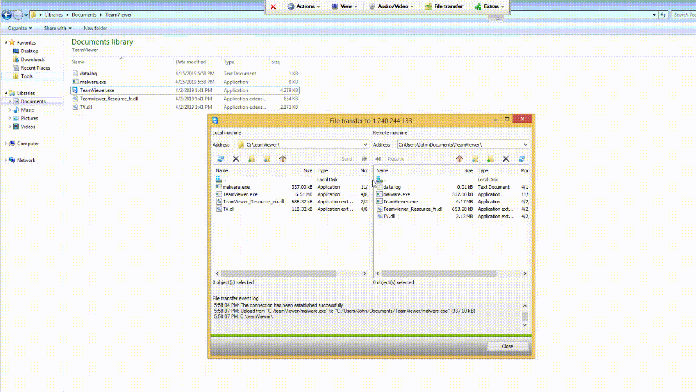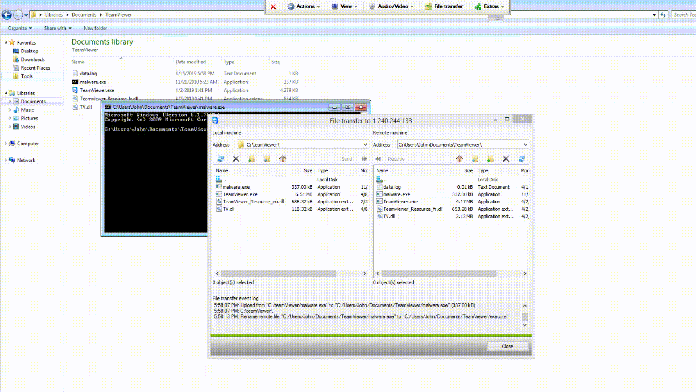
Remote demonstration of payload execution
According to Checkpoint Research, once a malicious TeamViewer provides remote access, one of the first uses of AutoHotKey Scripts is to upload a screenshot from the affected PC.
Based on the Telemetry Record, this attack targets countries such as Nepal, Guyana, Kenya, Italy, Liberia, Bermuda, Lebanon, public sector finances and public officials.
Indicator of Compromise
DLLs
013e87b874477fcad54ada4fa0a274a2
799AB035023B655506C0D565996579B5
e1167cb7f3735d4edec5f7219cea64ef
6cc0218d2b93a243721b088f177d8e8f
aad0d93a570e6230f843dcdf20041e1e
1e741ebc08af09edc69f017e170b9852
c6ae889f3bee42cc19a728ba66fa3d99
1675cdec4c0ff49993a1fcbdfad85e56
72de32fa52cc2fab2b0584c26657820f
44038b936667f6ce2333af80086f877f
Documents
4acf624ad87609d476180ecc4c96c355
4dbe9dbfb53438d9ce410535355cd973
C&Cs
1c-ru[.]net/check/license
intersys32[.]com/3307/
146.0.72[.]180/3307/
146.0.72[.]180/newcpanel_gate/gate.php
185.70.186[.]145/gate.php
185.70.186[.]145/index.php
193.109.69[.]5/3307/gate.php
193.109.69[.]5/9125/gate.php











Leave a Reply