Attackers target potential victims through a malicious AutoHotkey script to prevent detection and stolen information, to lower payloads and to access compromised machines remotely via TeamViewer.
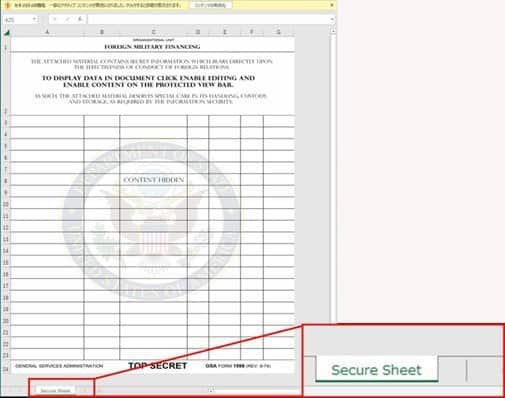
AutoHotkey (a.k.a. AHK) is an open-source scripting language that was used for Windows back in 2003 in order to add keyboard shortcuts (hotkeys). A malicious AutoHotkey script payload is provided by the US FMF program using a decoy Excel Macro-Enabled Workbook email attachment known as Military Financing.xlSm.
Agency for Defense Security Cooperation to trick potential targets to enable macros to view the contents of the file. As discovered by the Cyber Threat Research Team of Trend Micro. The XSLM document’ drops the AutoHotkey legitimate script engine together with a malicious scripting file’ once the victims have enabled the macro in Microsoft Excel, and will immediately after that the malicious script will be run and connected automatically to its C&C server by downloading more scripts on the damaged machine based on the commands it receives from attackers.
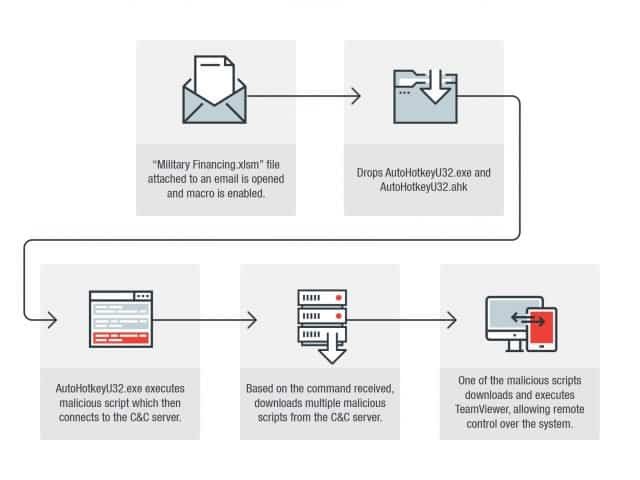
The researchers analyzed the activity of the dropped AutoHotkeyU32.ahk script and saw that the following commands are executed: As researchers have found, one of the malicious scripts downloaded will eventually drop the TeamViewer copy, allowing the wrong actors to have remote access to the infected computers.
“These files allow an attacker to get the computer and take screenshots. Most importantly, one of those files also allows TeamViewer to download, a remote user access tool providing remote control over the system by threatened actors,” says Trend Micro.
Although the purpose of this malicious campaign is still unknown, it may be used by the actors behind it to collect cyber spy information, as it is aimed at the victims potentially interested in military funding programs from the Defense Security Co-operation Agency.
However, the attackers may use seemingly harmless AutoHotkey scripts that help to avoid detecting other payloads, from bank Trojans, coinminers and backdoors to more risky ransomware or wiper malware. AHK-based malware strains appeared in 2018 and AutoHotkey-based malware began to appear early 2018 in the form of different targetbots and game cheating tools while Ixia’s security research team distribute multiple AHK malware samples of cryptomas and a clipboard hijacker in February.
One month later the research team at Cybereason Nocturnus stumbled upon an AHK malware strain that they labeled Fauxpersky because they tried to pass as a legitimate antivirus copy from Kaspersky. “Every day we find the same clipbankers / droppers / keyloggers with minor code changes only, and also samples with complex file structure and obstruction techniques,” said Ixia security researcher Gabriel Cirlig at that moment.











Leave a Reply