Multiple massive malvertising attacks targeted iOS users in USA and multiple EU countries for almost a week used Chrome to bypass the browser’s built-in pop-up blocker by iOS vulnerability.
EGobbler, an at-risk group that flourished behind the attacks, used all through the push ‘ 8 individual campaigns and more than 30 fake creatives,’ each with a fake ad campaign that lasted from 24 to 48 hours.
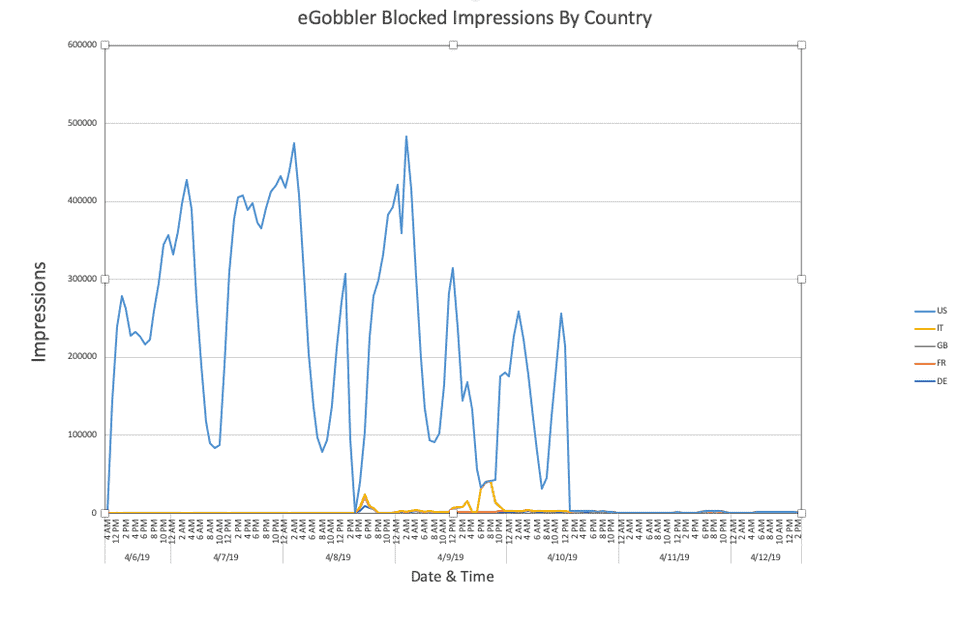
In total, around 500 million users ‘ sessions were exposed to this broad orchestrated campaign pushing false ads, according to confident researchers who discovered and monitored iOS-targeted eGobbler attacks.
The campaigns of eGobbler generally remain active for a maximum of 48 hours, followed immediately by short winter periods that end abruptly when an attack begins, as the experts of Confiant have discovered.
The April camp used landing pages on.world domains and pop-ups for hijacking user sessions and redirecting the victims to bad landing pages.
While pop-ups are used as part of similar campaigns to redirect targets to pages designed by malicious actors for use with phishing or malware, it is certainly unusual given the efficiency of browser blockers.
The decision of Crooks to use pop-ups to hijack users was revealed after the researchers tested the “two dozen devices, both physical and virtual” payloads of the malvertising campaign and “divided the test between sandboxed and non-sandboxed iframes.”
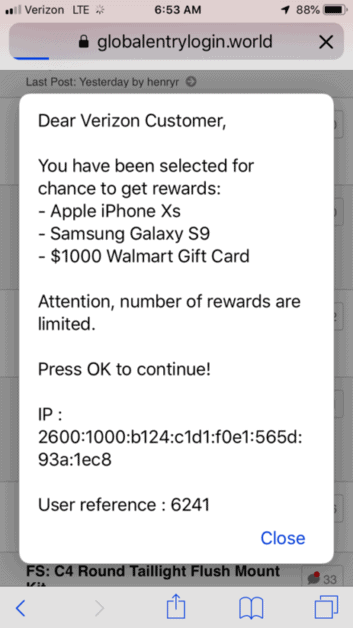
Landing page for malvertising campaign
As found, “the main session detection mechanism of payloads was pop – up, and furthermore, Chrome on iOS was a bottom line because the built-in pop – up blocker failed consistently.”
The reason for this was revealed to be the payload’s built-in “techniques which benefit from iOS Chrome detection when user activated pop – up detection, thereby avoiding pop – up blocking.
eGobbler Chrome uses sandboxing attributes to bypasses for Ios
To do so, the malicious payloads the eGobbler group used during these massive malvertising campaigns exploited an unexpected vulnerability in the Chrome for iOS Web browser— the Chrome team is looking into the issue after Confident reported that fault on April 11.
In order to make things worse, as Confiant further points out, “the malevolence exploited by eGobbler is that it can not be avoided using standard ad sandboxing attributes.”
This means that the ad sandboxing attributes integrated into ad service products, such as Google’s AdX and EBDAs, as well as their user interactions requirements are also avoided by payloads.
According to cross-border iframes policy, the fact that this exploit can bypass the need for user interaction should be impossible. Moreover, this completely circumvents the browser’s anti-redirect functionality as the attacker does not even need to redirect to hijack the user session.
The eGobbler malvertising group designed this campaign to specifically target iOS users, but it wasn’t the first one. Confiant monitored another campaign run by the ScamClub group in November 2018, capturing about 300 million iOS user sessions and transferring all of them to adult content and gift card scams.
As Confiant said in his report, “This was a stand-out campaign compared to the others, which we monitor not only on the basis of one-off payload but also on volumes.”
“After a brief pause, the campaign saw a strategic pivot to another platform on April 14 and is still active under the ‘ .site ‘ TLD landing pages. With an impact of half a billion user sessions, this is among the top three massive malvertising campaigns we’ve seen in the last 18 months.”











Leave a Reply