In the WebKit browser engine, a malvertising campaign observed last year by advertisement cryptography firm Confiant abused what turned out to be a zero-day weakness.
When reviewing a campaign performed by a threat agent they call ScamClub, optimistic researchers found the security void. For many years, the community has been active, launching malvertising attacks intended to funnel users to a wide variety of tempting rewards on spam websites.
ScamClub specializes in high-volume operations; a substantial number still enter consumers even though much of their payloads are blocked.
“ScamClub has provided over 50 MM of malicious [ad] impressions over the last 90 days, maintaining a low baseline of activity enhanced by frequent manic bursts, with as many as 16 MM of affected ads being served in a single day,” Confiant said in a Tuesday blog post.
In the iframe sandboxing functionality of WebKit, the “allow-top-navigation-by-user-activation” attribute is designed to avoid malicious redirections by allowing a redirection only to occur when it is activated by user actions (e.g. a click or a tap inside the frame).
Nevertheless, Confiant found that by using an event listener for a “message” event, the ScamClub threat actor managed to circumvent this iframe sandboxing feature. It will cause the redirect if the event listener picks up a response, which enhances the probability of users being routed to their scam websites without ever tapping within their iframe to enable the redirect directly.
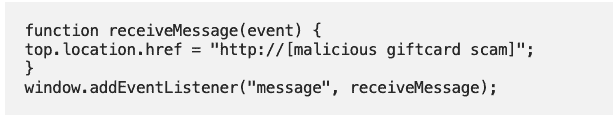
“Messages are flying around all the time in modern web apps, usually with wildcard destinations, often on user interaction,” Confiant explained.
Combined with the massive amounts and broad targeting of ScamClub that targets hundreds of different websites, it’s all about the improved effectiveness of spawning a good redirect, even though we’re talking about a single digit percentage rise, which may mean tens of thousands of impressions over the course of a single campaign,” the company added.”
In June 2020, Confiant discovered the campaign leveraging the flaw and promptly disclosed the results to Apple, whose browser Safari uses WebKit, and Google, whose browser Chrome still uses WebKit on iOS.
In December 2020, the problem was fixed in WebKit, and Apple included the patch in versions of WebKit distributed earlier this month with patches released for iOS and macOS. As CVE-2021-1801, Apple monitors the problem and appears to have solved it with “improved iframe sandbox enforcement.”










Leave a Reply