The reign of Retadup botnet has achieved over more than 850,000 installations with safety investigators from antivirus manufacturer Avast working with the French National Gendarmerie taking its control and control server (C2).
The botnet has mainly been used for cryptojacking, the scientists say, but it also distributes stop ransomware and the Arkei info robber.
Botnet handler(s) could have built millions
The amount of cash that the operator has created is not clear, but one monero address that Avast has found at Retadup’s C2 demonstrates a gain of over $4,200 a month (XMR 53,72).
However, the figure is from only one mining pool, and configuration files demonstrate that the operator also used others. While the projected monthly income is uncertain, much more is anticipated.
French public radio channel France Inter has released an picture of Jean-Dominique Nollet, the head of the Cybercrime Center for Crime Fighting (C3N) of the French National Gendarmerie.
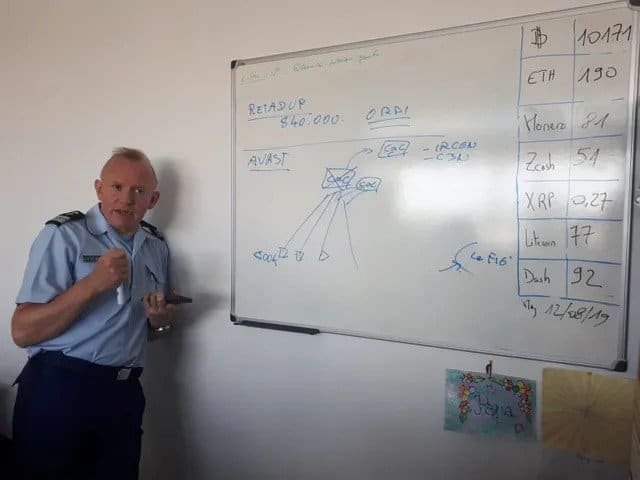
Nollet said in an interview that operators earn “several million dollars” each year from 2016.
Author leaves apparent tracks
Details on the handlers of a botnet are not public at the moment, but one investigator was able to discover data on the author of the botnet from a C2 domain released by Avast.
Ironically, the picture was a response to Trend Micro’s first malware research. Researchers found that the author belonged to the Twitter account and the data was real.
Latin America’s Most Victims
Public information on Retadup was found to be distributed to hospitals in Israel by mid-2017. It claimed to be a Windows update executable.
However, the primary malware was a backdoor with the ability to propagate. Its range of characteristics included screenshots, keylogging installation, start / restart / stop process, shutdown, restarting or logging off the machine.
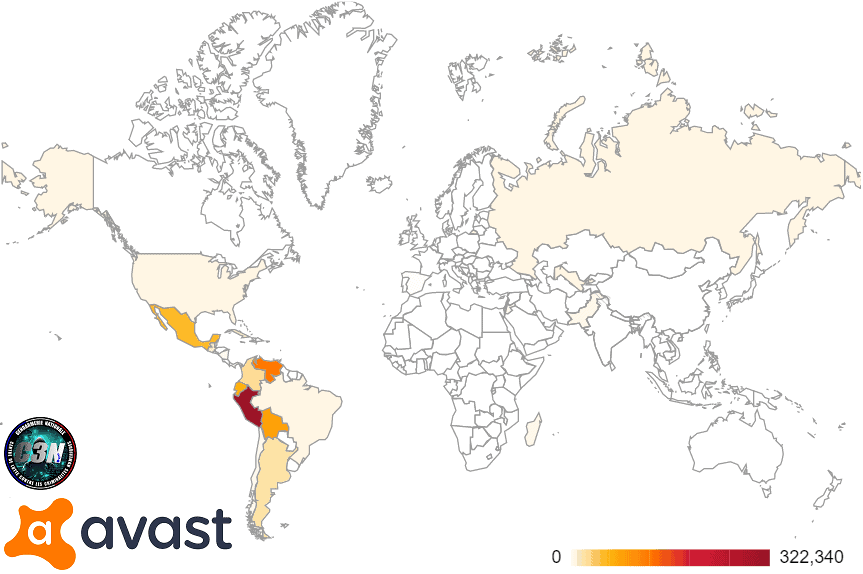
In a blog post today, Avast states that the majority of rehabilitation victims have been in Spanish speaking countries, with Peru leading the pack with more than 320,000 diseases. In all, computers in 140 nations were affected by malware.
Design flaw is bringing down botnet
It was feasible to downgrade the Redatup infrastructure owing to a design defect discovered by Avast in the botnet communication protocol. Once the C2 has been taken over, the bug enabled the scientists to wash infected hosts without user interference.
Although only a few hundred French victims were involved, the majority of botnet facilities were situated in France, so that national authorities were contacted and the alternative submitted.
Once the scheme was approved by the prosecutor, the Gendarmerie substituted the malicious C2 server with a variant of “linked cases of self-destruct retrieval.”
“In the very first second of its activity, several thousand bots connected to it in order to fetch commands from the server.” – Avast
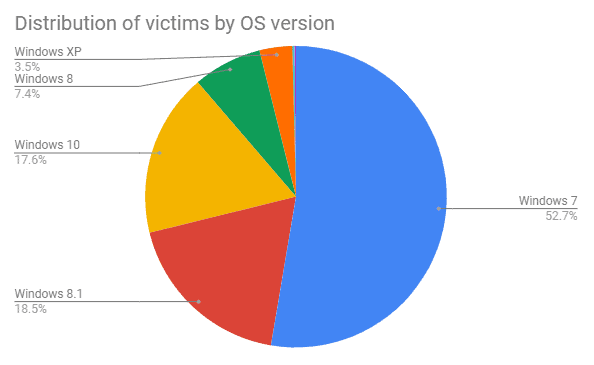
In total, there have been over 850,000 single infections neutralized. Most devices run Windows 7 and have 2 or 4 cores. More than 85% of the devices run the default antivirus solution.
Credit: Bleeping computers











Leave a Reply