Mozilla has roll-out protective measures in the Firefox web browser to avoid software injection attacks by eliminating evalual()-like functions and inline scripts.
“A proven way of combating software injection attacks is by increasing the surface of the attack by eliminating potentially dangerous objects from the codebase and thereby hardening the code at various levels,” Mozilla’s security team told today. Check for mozilla vulnerability scanner here.
“We’ve added occurrences of inline scripts and disabled eval()-like functions in order to make Firefox robust against such software injection attacks.”
Removal of inline scripts
Mozilla has re-written all inline event handlers and moved JavaScript inline code to packaged files for all Firefox on: pages — all 45 of them are listed here— and are subject to code injetion attacks using inline scripts.
This type of pages was intended to provide users with a simple interface for inspecting the details about Firefox’s internal working, like the one about: config page that “exposes an API for inspecting and modifying preferences and configurations.” Because about: pages like standard websites use HTML and JavaScript, potential attackers can make use of it in order to insert malicious scripts into Th
“This allowed us to enforce a strong Content Security (CSP) policy such as’ default-src chrome’ that ensures that the JavaScript code that was injected doesn’t work,” Mozilla says.
“Instead, JavaScript software only runs when loaded from a packed resource using internal chrome: a Protocol.” Mozilla built an effective barrier against code injection attacks by making it impossible to insert inline scripts in Firefox’s about: pages that could lead to arbitrary code execution by using this vector of assault.
Execution of functions to deactivate evalual () functions
The JavaScript function eval() is a strong but dangerous tool, together with the related’ new function’ and’ set timeout()/setInterval().’ It parses and performs an arbitrary string in the same security sense as itself, “also the Mozilla Security Team adds.
“This execution scheme allows to execute software created at runtime or stored in non-script places, like the Document-Object Model (DOM), as Mozilla provides additional data about the dev web docs,” eval() is a dangerous feature which executes the code it transfers with caller privileges.
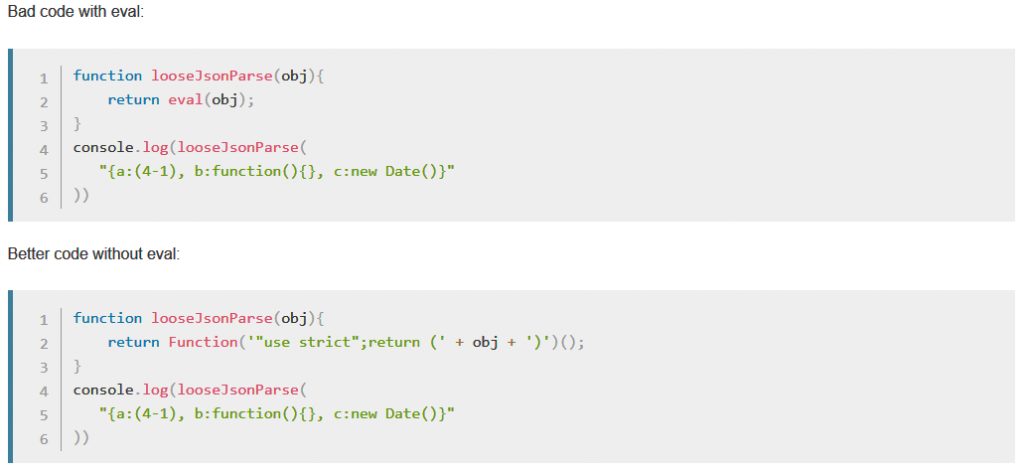
Coding without eval()
Runtime statements have also been introduced to Firefox’s codebase, a move designed to deprive system-privileged script meaning of assessment() like features.
Mozilla also noticed calls to eval() outside Firefox while it removed all eval() like features. For example, users of Firefox would include eval() functions in custom files like userChrome.js to configure Firefox at runtime.
Runtime checks by the Mozilla Security Team showed that users included evaluations in some of these customization files. To allow users to adapt their experience to Firefox, Mozilla says the app will remove “blocking mechanisms and allow for use of evalual().” “With this in mind, our implemented eval() assertions will continue to notify Mozilla Security Team about the unknown instances of eval().











Leave a Reply