Nemty ransomware is under active development, although it can not be shown by its version number. Its writers obviously strive to make this malware more effective and advanced and to start distribution more widely.
The malware is new to the company and its cold reception in the underground Ransomware community did not assist take the route its managers wished.
Process and service assassin
Despite code modifications, Nemty writers have kept the same version amount and the safety investigator Vitali Kremez’s analysis demonstrates. However, the code demonstrates changes that make the ransomware more aggressive.
The researcher noticed that the latest malware version includes code to kill processes and services to encrypt current files.
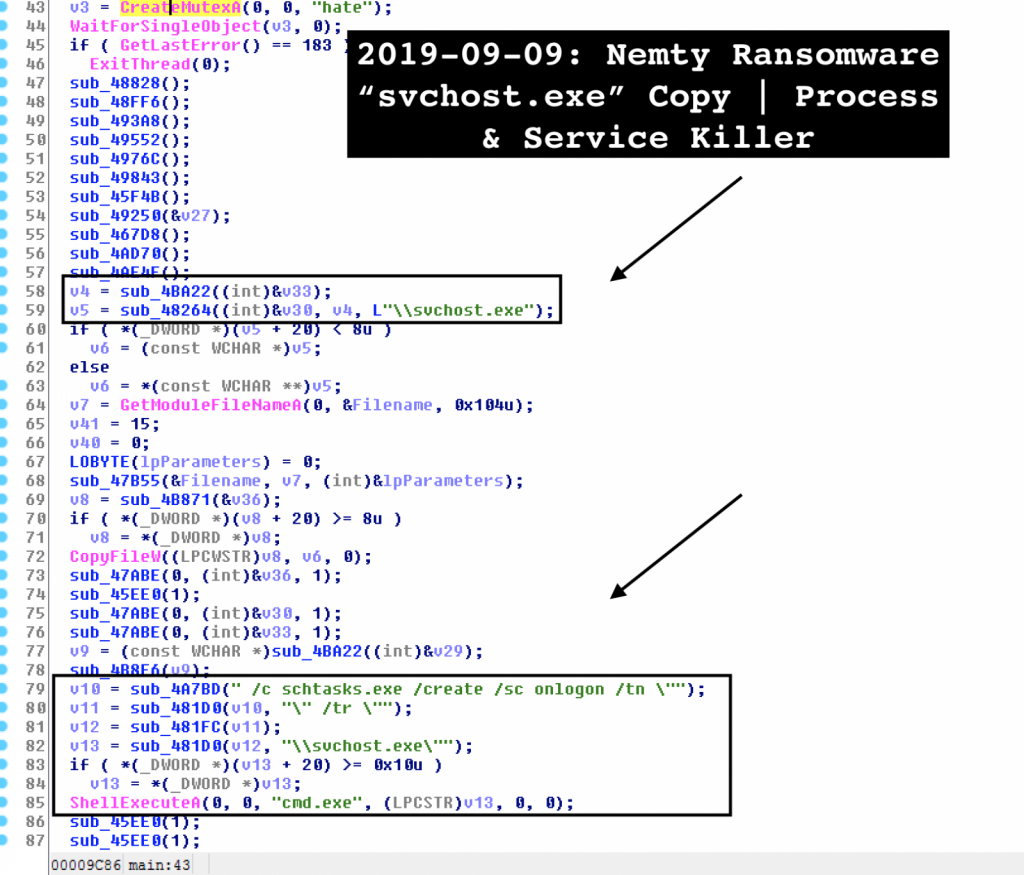
Process and service killer
A look at Nemty’s new code reveals a set of nine targeting processes including WordPad, Microsoft Word, Excel, Outlook Thunderbird email clients, SQL and VirtualBox software.
It gives us a clue that Nemty targets corporate victims with SQL and VirtualBox on the list.
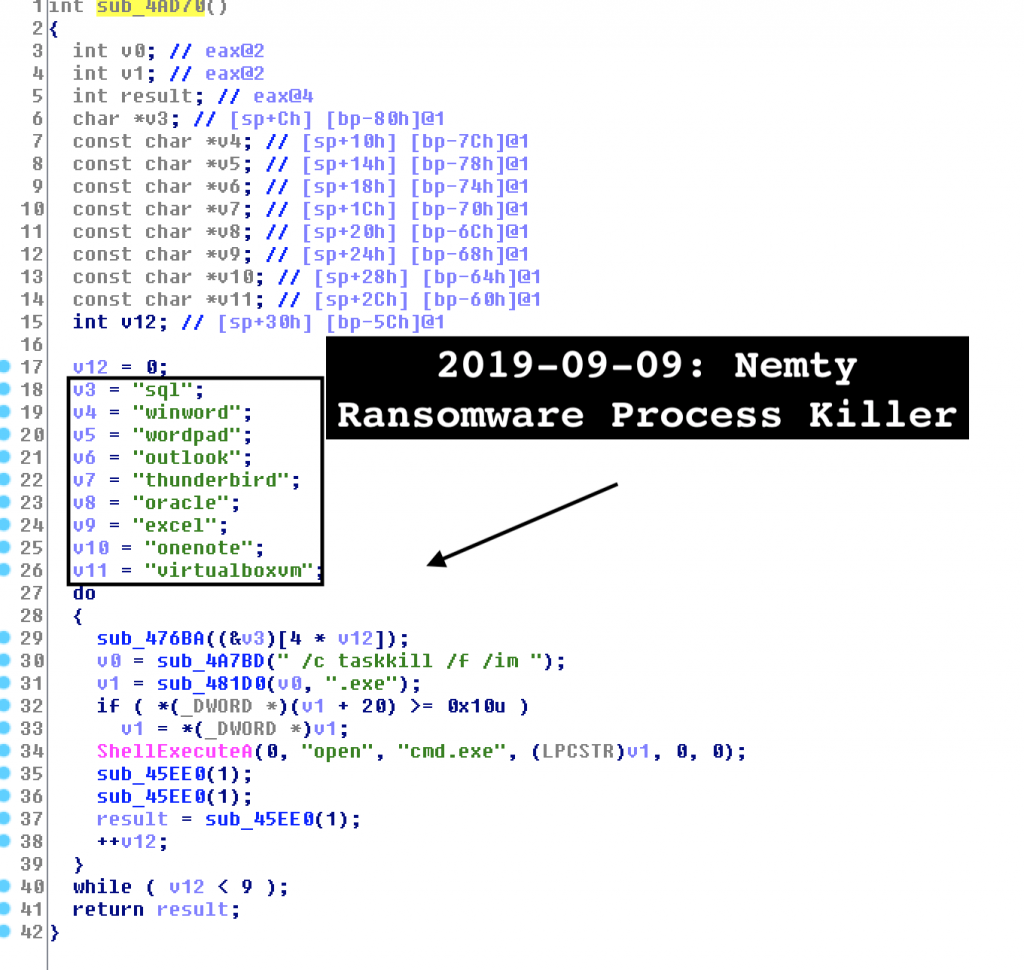
List of terminated processes
More nations on the “no-no” list
Kremez also noted that the check ‘ isRu’ has now spread to more countries. This full list now includes Russia, Belarus, Kazakhstan, Tajikistan, Ukraine, Azerbaijan, Armenia, Cyrgyzstan and Moldova.
With the previous malware version,’ isRU’ made no difference to the encryption task and just marked the hosts to send system information to the control server. This was amended by an update and computer encryption was aborted for this check.
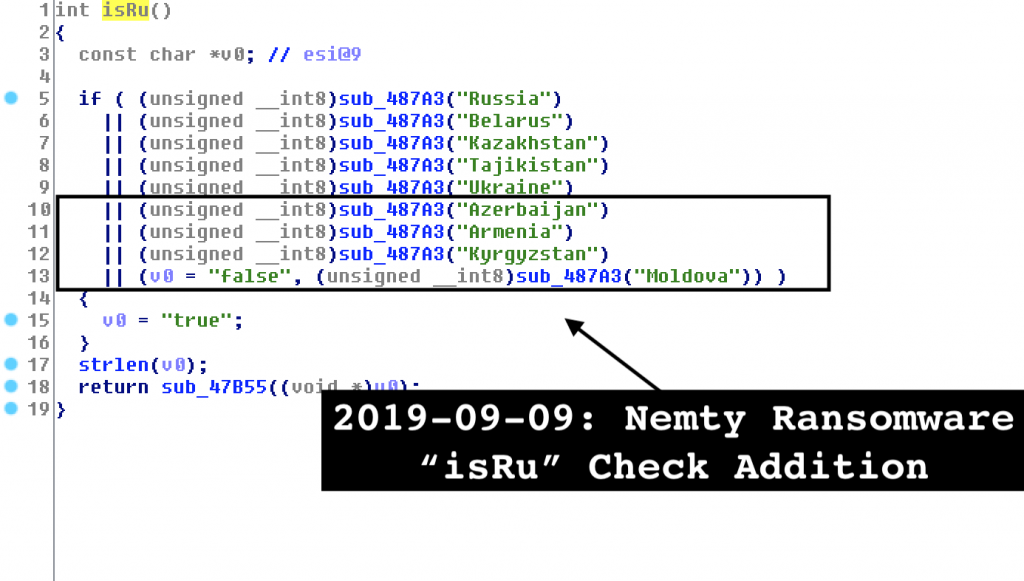
Blacklisted countries
New pipeline for distribution
One of the first versions of Nemty was distributed via RIG EK (exploit kit), while the later release 1.4 was distributed via a fake PayPal page.
At the beginning of this week, security researchers noted changes in the way victims are selected and the process of encryption worked.
The malware operators have a new distributor, Radio EK, on their list, as found at the start of the week by nao sec.
However, because EK exploits a JScript and VBScript vulnerability for Internet Explorer, that Microsoft patched three years ago, the researcher told BleepingComputer. This is not a superior distributor.
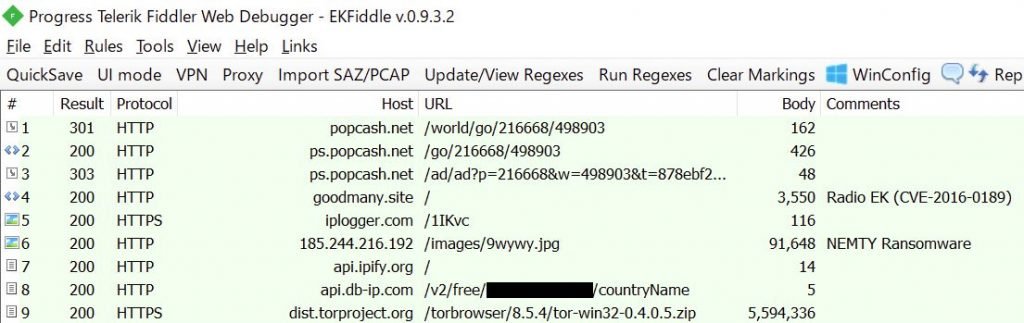
RadioEK in a malvertising campaign
Nemty is not currently very successful, but its authors seem to put energy into earning respect for cyber criminals in ransomware forums and turning their malware into a lucrative business.











Leave a Reply