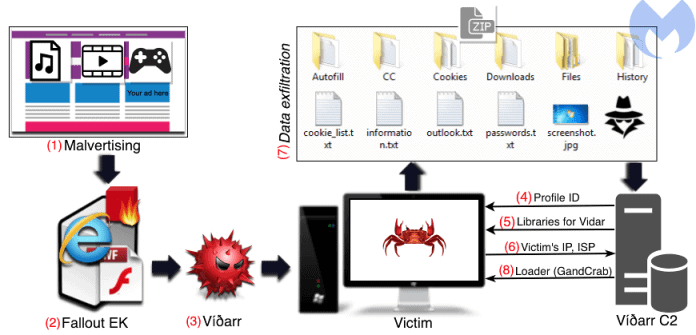
A new malware chain that uses multiple payloads to steal confidential data from the machine of the victim and encrypt their files with GandCrab Ransomware
Threat actors using the Fallout exploit kit, a toolkit designed to exploit ports, software vulnerabilities and deploy backdoors in vulnerable systems.
Malwarebytes security researchers observed a threat actor using the Fallout exploit kit to distribute GandCrab ransomware to the Vidar information stealer and secondary payload.
Credit : MalwareBytes
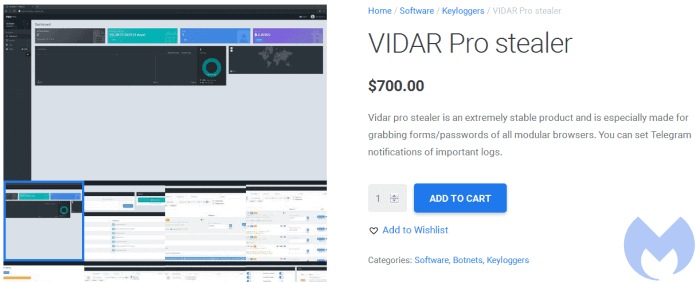
The malware identified as Vidar has the ability to steal and can be customized according to the requirements of the threat actors.
Researchers noted that Vidar is available for sale, a single license costs $700, along with usual credit card numbers and passwords, including the ability to steal digital wallets passwords.
Credit : MalwareBytes
When the vidar is executed on the client machine, it searches for the data specified in the profile configuration and sends the data back to the C2 server immediately via an unencrypted HTTP POST request.
The following system details are stolen, including specs, running processes, installed applications, IP address, country, city and ISP address. It then saves the data to the.txt file and sends it back to the attacker.
Vidar loads the secondary payload via its control and control server after extracting the information from the client machine.
“In about a minute after the initial Vidar infection, the files of the victim are encrypted and their wallpaper is hijacked to display the GandCrab version 5.04 note.”










Leave a Reply