A new Spambot Trojan targeted at French people has been found to record the screen of a victim while using sexual, pornographic and known pornographic websites.
We’ve all heard of the fake “sextortion” email scams telling recipients they’ve installed software to record them while you’re on adult websites. After one year of sending these emails, many people came to see them as a scam.
A new spambot is about to make things confusing in a new report released by ESET today. That’s because recording your screen while you’re on porn websites or pages with sex-related keywords has been discovered.
Spambot targets French
The new Spambot was named Varenyky by ESET scientists, who said that they discovered it when they saw a rise in French user infections in May. Any.run also found this same Trojan in June.
“In May 2019, ESET researchers observed a spike in ESET telemetry data regarding malware targeting France,” ESET said in a new report. “After further investigations, we identified malware that distributes various types of spam. One of them is leading to a survey that redirects to a dodgy smartphone promotion while the other is a sextortion campaign. The spam targets the users of Orange S.A., a French ISP. We notified them before the release of this publication.”
The Varenyky spambot Trojan is sent through malicious emails that claim to be bills or invoices. These e-mails are written to persuade the user to open malicious Word accessories.
When a user opens and enables its contents, a Word macro checkes whether Windows language is French (fr-FR) and if not, no malware is installed.
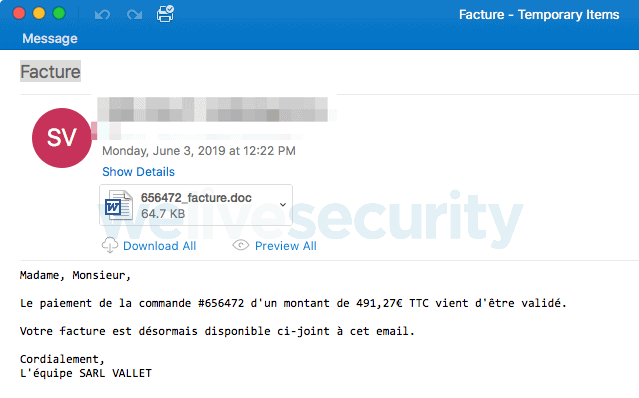
Malspam
On the other hand, it will download and run the spambot if the computer is configured in that language. The malware downloaded is also language checked, but is only looking for English or Russian this time and the malware will terminate the following error if detected.
When the malware passes the language checks, it is now configured to start automatically on the computer of the victim.
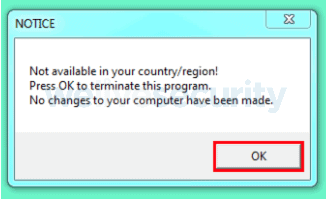
Language checks
Once executed, the Trojan connects to the Tor command & control server to get instructions on which spam to send. These spam e-mails target French ISP Orange Telecommunications company customers, and contain links to redirect recipients to scam sites such as those below.
It also connects routinely to the malware command and control servers via Tor and receives commands to run or to download other programs.

Scam sites promoted by spam
According to scientists from the ESET, this Trojan has the capability to execute batch files, executables and commands from PowerShell. In addition, some variants will download the legitimate WebBrowserPassView tools of NirSoft and Mail PassView to steal passwords from the browser and email account, which then are sent back to the C2.
Recording your screen when You are on adult sites
The Trojan included the function to follow your browser’s web browser for sex-related titles, such as sex, xxx, webcam or pornhub, as well as words related to Bitcoin and Hitler.
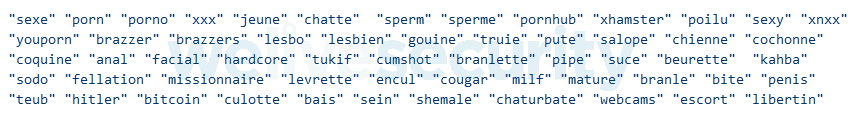
Monitored Keywords
Monitored Keywords You could use a downloaded FFmpeg executable for recording the screen by browsing a web page whose title contained one of the above words. The recorded videos were then sent via a downloaded Tor client back to their command & control server.
It is not known whether these videos are created for the curiosity of the attacker or whether there are plans to use them for sextortion emails against victims.
“These videos could have been used for convincing sexual blackmail; a practice called sextortion. It’s unknown if these videos were recorded out of curiosity by the author(s) of the spambot or with an intention to monetize them through sextortion. “
Though Varenyky Trojan was able to capture these videos, ESET saw no sign that they were used against the victim or others in a actual sextortion campaign.











Leave a Reply