A phishing campaign with WeTransfer notifications as substitutes for malicious URLs commonly used in these types of attacks was recently detected, bypassing Microsoft, Proofpoint, and Symantec’s successful e-mail gateways.
WeTransfer is a cloud-based service for the hosting and transferring of files of up to 2 GB for the free level and up to 20 GB for the paid service plus.
Security researchers at the Cofense Phishing Defense Centre’s phishing attacks have targeted a wide range of prominent industries such as media and banking.
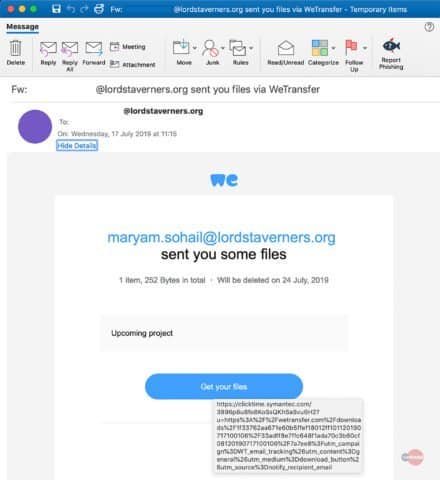
Legitimate WeTransfer ‘ shared file’ notifications were incorporated into the target inbox photo messages with weTransfer links that help the e-mails avoid the malicious content detection algorithm of the gateway.
“The attackers utilise what appears to be compromised email accounts to send a genuine link to a WeTransfer hosted file,” researchers discovered.
WeTransfer host phishing redirectors
The threat players added custom notices to their phishing-email, often choosing them as invoices ready to be checked, to make the Wetransfer notices look more convincing.
This is a popular phishing tactic to reduce the custody and take advantage of the alert drop, because the links wouldn’t even click otherwise.
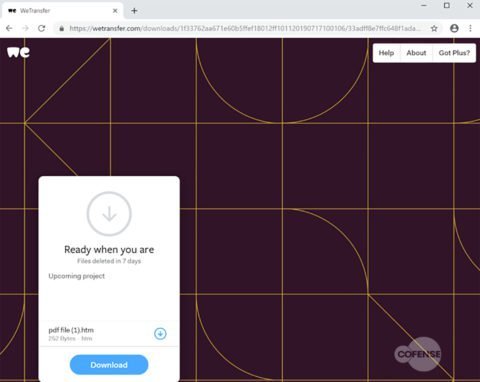
After the victims click on the “Get your files” button at the bottom of the WeTransfer notification — which passes all the security checks with flying colors — they will get “redirected to the WeTransfer download page where a HTM or HTML file is hosted and thus downloaded by the unsuspecting victim.”
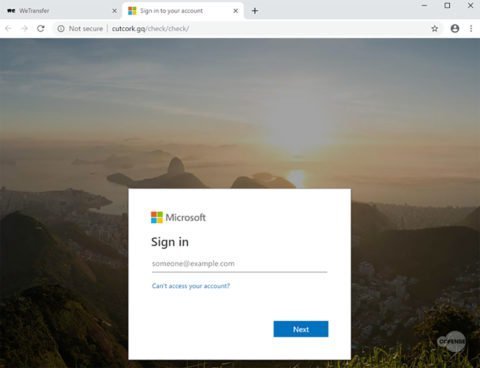
The phishing landing page will be opened in the default victims ‘ web browser once the downloaded html file is opened as part of the final phase of the attack to get them to pass on their Office 365 credentials and various other online services.
“As WeTransfer is a well-known and trusted file hosting system, used to share files too large to attach to an email, these links will typically bypass gateways as benign emails, unless settings are modified to restrict access to such file sharing sites,” conclude the Cofense researchers.
Baiting techniques
Cofense has discovered several other active phishing campaigns using a variety of techniques to steal the sensitive information of their targets while monitoring the recent trends of phishing attacks.
One week ago, phishers were seen using a basic HTML element to hide malicious URL from antispam solutions, a tactic to avoid security checking and delivering their messages to inboxes of American Express customers with an Advanced Threat Protection (ATP) Office 365.
In late July, the campaign for malicious microsoft Word document attachments was observed with fake efax messages which dropped a Trojan banking and RAT-cocktail.
Cofense investigators launched another phishing campaign in June, which abused QR codes which redirected targets to landing pages to avoid effective security solutions and controls aimed at stopping such attacks.











Leave a Reply