iNSYNQ’s cloud computing supplier encountered a ransomware attack that compelled the business to shut down some of its servers from spreading and affecting more client information to contain the malware infection.
iNSYNQ is a licensed Microsoft, Intuit, and Sage host that offers cloud-based virtual desktops for company apps such as QuickBooks, Sage, Act & Office.
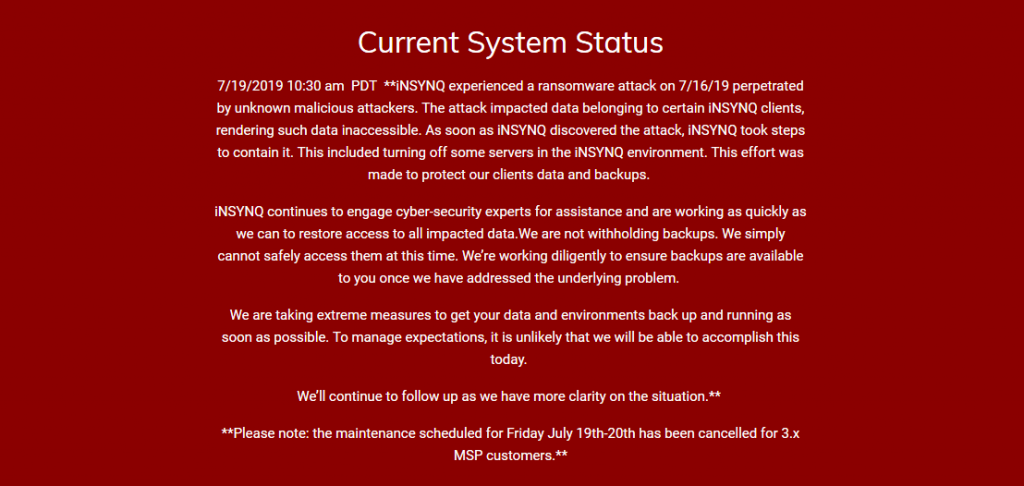
“INSYNQ encountered a 7/16/19 ransomware attack by unidentified malicious attackers. The attack affected information belonging to certain iNSYNQ customers, making such information inaccessible,” states a status update released on the company’s support page.
“As quickly as iNSYNQ found the attack, iNSYNQ took measures to contain it, including turning off some servers in the iNSYNQ setting, which created an attempt to safeguard information and backups from our customers.
The cloud hosting company also claims it has recruited cybersecurity professionals to assist restore access to impacted client information and virtual desktops for all customers, with “significant traction” to be done “by early next week,” according to a letter sent by iNSYNQ’s CEO to customers.
As iNSYNQ CEO Elliot Luchansky also added in his letter, “Uncomprehensibly, there have been many requests for backups that I want to be very clear that we are not withholding data or backups, at this time we simply cannot access them securely.
“We will still do our utmost to guarantee that backups are accessible to you once we address the fundamental issue. Our entire team is working diligently to safeguard and restore access to your affected information [..] ”
Luchansky also answered some of the issues that iNSYNQ clients have requested following the ransomware attack downtime saying that:
Unfortunately, these kinds of things are inevitable. No system is 100% impervious to malware, and we collectively were victims of an attack perpetrated by unknown malicious actors. We wish we had a quick-fix or a way to fully eliminate these risks. If we did, then obviously this kind of event would never happen.
He also said a timeline is not yet accessible for when the environments of the customers will be backed up, but the iNSYNQ team is speeding up the process of restoring the information of the customers and having all devices online.
“We switched off servers as soon as we recognized that we were assaulted and presently work closely with leading industry professionals specializing in workouts like this, so that we can restore access as fast as we can,” Luhansky added.
“We contained the case as shortly as we were conscious of this; there is no proof to suggest that any of your documents have been taken from iNSYNQ. The focus is on access to your encrypted records; it is not a question of stolen or copied your information,” said CEO of iNSYNQ.
While the letter sent by the CEO to the clients of the company after the safety event gives some additional information about what occurred, there is no mention of the ransomware attack that hit iNSYNQ on Luchansky’s Twitter account or on the no longer available iNSYNQ account— a Google-cached version of the contents of the account can be found here).
A client who contacted the iNSYNQ team said information backups of the customers were stored on a distinct server but impacted by the cyber-attack on the same network.
The business also thinks that all client information is retrieved and restored, but it takes some time before all backups are checked to make sure the malware does not influence them.
We reached out for comment to iNSYNQ but did not hear back at the moment of this release. When a reply is obtained, this article will be updated.
Update 17:29 EDT: iNSYNQ’s CEO sent us the following statement:
While I cannot share details on the specific ransomware or the number of servers affected, I can share that iNSYNQ and our customers are the victims of a malware attack that’s a totally new variant and hadn’t been detected before, confirmed by the experienced and knowledgeable cybersecurity team we’ve employed.
Unfortunately we have to keep the detail fairly minimal, as I’m sure you’re familiar with in these sorts of situations. Our customers and their data is our number one priority. Transparency is something we pride ourselves on, and it’s difficult to hold back. However, the lack of detailed information in this situation is purposeful. We’re in a behind the scenes trench warfare doing everything we possibly can to secure and restore our systems and customer data and backups, and too much information around this situation puts us and our customers at risk.
My team will continue to work around the clock to secure and restore access to all impacted data, and we believe we have an end in sight in the near future.











Leave a Reply