A Sodinokibi Ransomware supplier hacks WordPress websites and injects JavaScript that shows a forum post about the content of the initial page. This fake post has a “response” from the site’s “admin” that includes a connection to the installer.
As safety software and individuals become increasingly conscious of the techniques used for distributing ransomware and malware, affiliates need to develop more advanced techniques for infecting their victims.
This is the situation with a fresh distribution technique which overlays a forum for false queries and answers in addition to the content of a hacked site. This false forum post will contain data about the content of the site visited by the user so the response and the connection provided by the admin is valid.
But the downloaded file actually infects the user with the Sodinokibi, or REvil, Ransomware.
How the overlay attack operates with false questions and answers
BleepingComputer was first warned by Aura that several victims were infected with this new attack technique. Below is a general overview of how this attack works and how the Sodinokibi, or REvil, Ransomware installation works.
Similar to the earlier EITest assault on Chrome HoeflerText Font Update, the affiliate picks up locations to inject a JavaScript script into the HTML as shown below. The URL is activated for all users but only includes information if the customer first visits the website or has not visited the website for a certain sum of time.

Injected Overlay JavaScript Script
When someone first visits the site, the script will show the following material in a fake French Questions and Answers forum poster.

Fake Questions and Answers Forum Post
To the user, this feels like the ordinary web site since the content of the fake forum post is linked to the content of the hacked page.
If a user updates the website once again, the script does not fire and the ordinary page is shown in the demo video at the end of the article.
However, if the user does not update the website, it will appear as if someone else posted a French-language query on a photocopier model “termination agreement.”
“Hello, I am looking to download letter of termination contract photocopier model. A friend told me he was on your forum. Can you help me?”
In answer to the question, the Admin will provide a false answer, which offers a direct link to the agreement requested.
“Here is a direct download link, model letter of termination contract photocopier.”
When a user clicks on the link, a zip file will be downloaded from a random hacked site under the attackers control. In this particular example, the file will be named “modèle_de_lettre_de_résiliation_contrat_photocopieur.zip” and when opened will contain a JScript file with the same name.
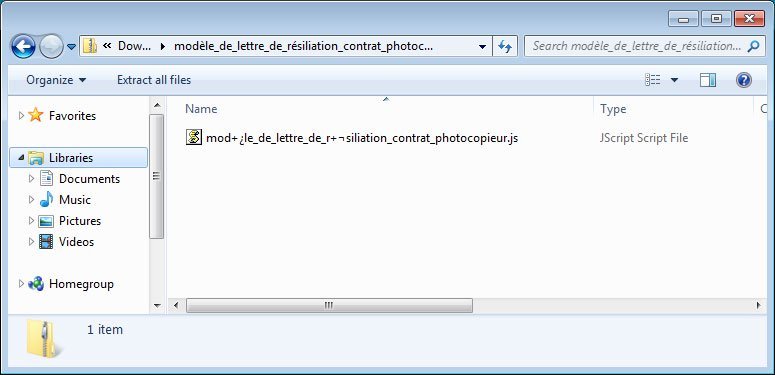
JScript Installer
This JScript file includes a flawed code that connects to a remote server that answers with a big bunch of information.
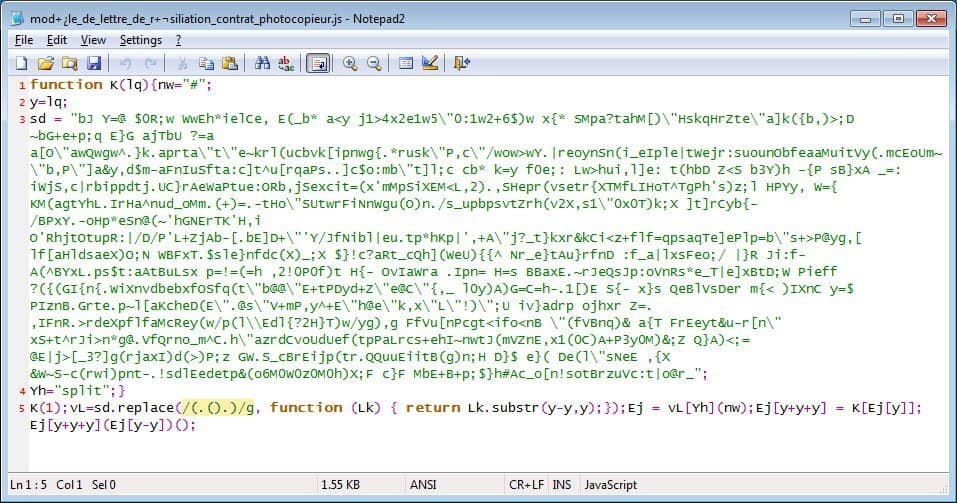
Caption
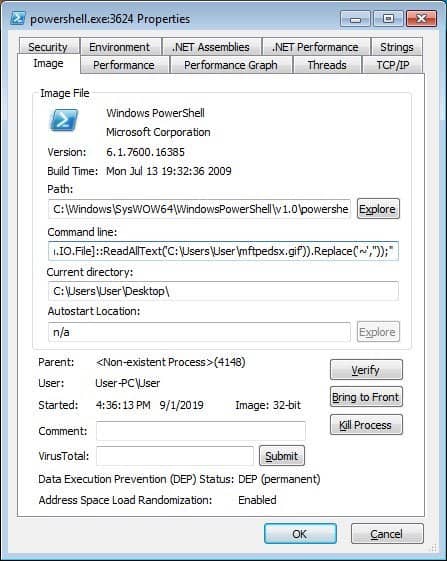
Removing ~ characters from PowerShell command
This results in a smooth PowerShell command that is then used to run the Sodinokibi DLL to encrypt a computer.

Deobfuscated GIF File
During encryption, the attackers clear Shadow Volume Copies from the victim using the following command PowerShell:
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$_.Delete();}When finished the victor will encrypt their documents and take a ransom note to a Tor payment site containing data on how to buy a decryptor.
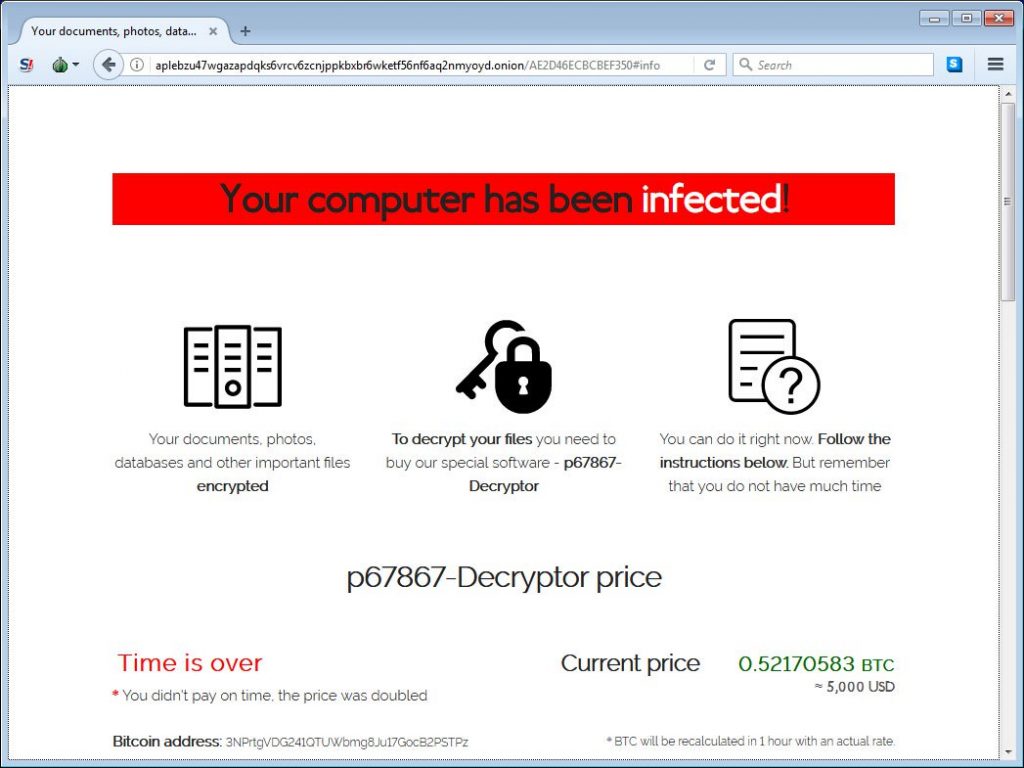
Sodinokibi Tor Payment Site
To safeguard yourself against this attack, make sure you have a kind of safety software installed with real-time protection and never run files that end with the.js extension.
We developed a video demonstration for those interested in seeing how the fake Forum overlay works.











Leave a Reply