SpeakUp Trojan backdoor can run on six different Linux and macOS distributions.
The hackers have developed a new Trojan backdoor which can run on Linux systems. Named SpeakUp, this malware is currently distributed primarily in China to Linux servers.
The hackers behind this recent wave of attacks use a feature to infect servers with this new malware strain in the ThinkPHP framework. Once the Trojan gets a foothold on vulnerable systems, hackers can use it to modify the local cron utility to persist in booting, execute shell commands, execute files downloaded from a remote C&C server, and update or uninstall themselves.
Check Point researchers, who first saw this new backdoor three weeks ago on January 14, say that SpeakUp also features a built-in Python script that malware uses to spread laterally over the local network.
This script can scan local networks for open ports, brute nearby systems using a list of predefined usernames and passwords and can take over unpatched systems using one of the seven exploits.
CVE-2012-0874: JBoss Enterprise Application Platform
CVE-2010-1871: JBoss Seam Framework remote code execution
JBoss AS 3/4/5/6: Remote Command Execution
CVE-2017-10271: Oracle WebLogic wls-wsat Component Deserialization
RCE CVE-2018-2894: Vulnerability in the Oracle WebLogic Server component of Oracle Hadoop YARN ResourceManager
CVE-2016-3088 Command Execution: Apache ActiveMQ File Server Upload Remote Code Vulnerability Execution.
When new machines are infected, SpeakUp is deployed on these new systems. Check Point states that SpeakUp can run on six different Linux and macOS systems.
The group behind this recent scan and infection campaign used SpeakUp to deploy cryptocurrency miners from Monero on infected servers. The Check Point team says that the group has made approximately 107 Monero coins since the start of its campaign, which is approximately $4,500. While the SpeakUp authors currently exploit vulnerability (CVE-2018-20062) in a Chinese-only PHP framework, they can easily switch to other exploits to spread their backdoor to even a wider range of targets, although nothing except ThinkPHP has been seen to target them.
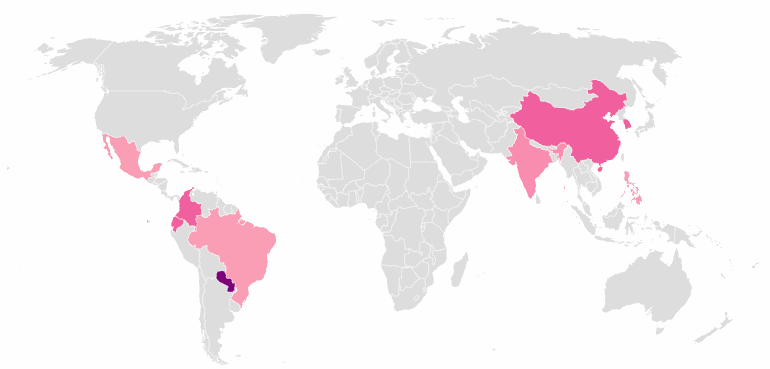
A map of current infections shows that victims of SpeakUp are predominantly in Asia and South America.
Speaking to ZDNet, Lotem Finkelstein, one of the Check Point researchers told us that SpeakUp infections in non-Chinese countries use its second-stage exploits to infect the internal networks of companies, which led to Trojan spreading outside the normal geographical area of a Chinese-only PHP framework.
Checkpoint The SpeakUp backdoor group is the latest threat actor in the ThinkPHP exploitation car. Scans and attacks on websites and web applications built on this Chinese PHP framework began last year.
According to our previous coverage, attackers initially only prodded websites that searched for vulnerable hosts and tested proof of concept. As many security experts predicted, these scans moved into full use in January.
Trend Micro reported two hacker groups with the same ThinkPHP vulnerability to Hakai and Yowai IoT / DDoS malware infect Linux servers.
Akamai experts have also seen a different set of attacks, with web shell backdoors, cryptocurrency mining software and even Windows malware dropped by threatening actors.
The SpeakUp malware group appears to be the most organized of all threat actors targeting the ThinkPHP ecosystem at the moment.
The complete Check Point report including compromise indicators (IOCs) can be found here.











Leave a Reply