A modular worm malware exploits common defects in servers running ElasticSearch, Hadoop, Redis, Spring, Weblogic, ThinkPHP and SqlServer to be used for monero cryptocurrency.
Systemctl.exe, the malware worm module called the PsMiner from the 360 Total Security Researchers, is a Go-language Windows binary that bundles all exploit modules used to hack vulnerable servers found online.
Apart from the exploits, the PsMiner worm module also has the ability to force its way through targets that use weak or default credentials and crack user credentials with a brute force cracking password component.
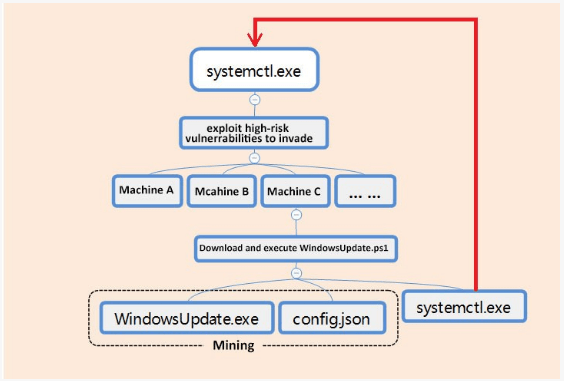
Once you manage to infiltrate a victim’s computer, PsMiner runs a PowerShell command to download a malicious payload of WindowsUpdate.ps1, the main module of the malware to drop your Monero miner in the final infection phase.
The malware also copies the malicious WindowsUpdate.ps1 script into the Windows Temp folder and creates a scheduled task for the Windows Service “Update Service,” which will restart the main malware module once every 10 minutes to maintain its endurance.
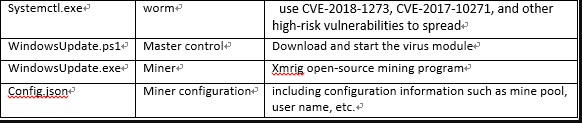
During the final stage of an infection, PsMiner will download and launch a custom mining profile for the open source Xmrig CPU miner for the Monero cryptocurrency.
While its worm capacity to spread between its victims and the way they use living off-land technology (LotL) to further jeopardize their goals and achieve persistence is very effective, it cannot be said the same about the benefits this campaign has gained for its masters.
As the 360 Total Security researchers say in their report, “Inquiring into the relevant transaction records, we found that the miner accumulated a total of approximately 0.88 Monroe (sic) coins in just two weeks.”
Cryptojacking is a threat Until Now
According to Symantec’s 2019 Internet Security Threat Report, the use of malicious PowerShell scripts increased by a whopping 1,000 percent in 2019.
Although the use of cryptojacking malware followed a downward trend in 2018, it is still in the arsenal of threat actors as demonstrated by PsMiner, a batch of eight Microsoft Store apps found to drop malicious Monero cryptomining scripts, and hundreds of vulnerable and exposed Docker hosts are actively abused in cryptojacking campaigns.
In addition, a new Backdoor Trojan dubbed SpeakUp that drops XMRig miners on its victims and the XMR-Stak Cryptonight cryptocurrency miner used to detect a new coinminer malware strain targeting multiple Linux distributions servers.
Cryptocurrency mining malware also affected ten times more organizations than ransomwaredid last year, while, as detailed in a Check Point Research report, more and more malware families have started to merge into new capabilities that target cryptocurrency within their arsenal.











Leave a Reply