Twitter has revealed a bypass of a latest Steam vulnerability that could enable malware or local attackers to obtain administrative rights. This fresh technique enables an attacker to bypass Steam’s fix and re-use the vulnerability.
If you haven’t listened to the last week’s Steam vulnerability tale, here’s a little recap.
Last week, Matt Nelson and Vasily Kravets, safety scientists, revealed Steam vulnerability that could allow a local attacker or malware to modify any registry key they wished. This allows an attacker to alter a Windows service with high privileges and start any executable that they want with the same privileges. You may use the following free web scanning tool to know the issue directly.
The scientists revealed that Valve refused to remedy this vulnerability, because they were outside the scope of their bug bounty program. Even after the CVE-2019-14743 Identifier had been allocated to this vulnerability, Steam contested this vulnerability because the Steam threat model excludes “attacks requiring physical user access” and “attacks requiring the capacity to drop files arbitrarily on the user’s filesystem”.
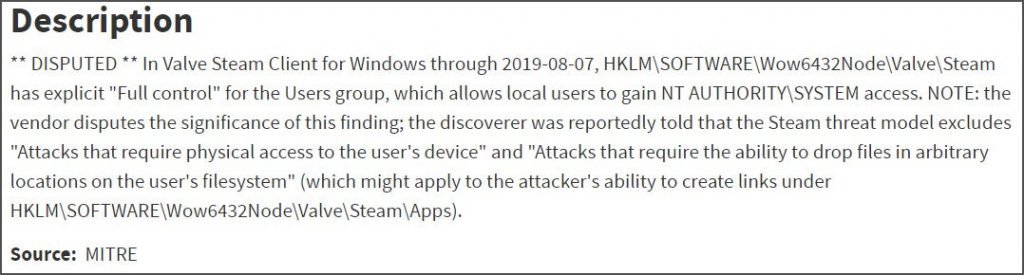
Dispute of Vulnerability
After scientists and Steam users were upset, Valve decided to release a vulnerability fix. However, several scientists thought that the solution was incomplete as the USERS group still had complete rights for the Steam setup folder and would discover fresh privilege escalation techniques.
Researchers were right
The researchers ‘ projections were right only four days later when another investigator named xiaoyin Liu revealed a bypass of Valve’s Twitter fix that enables attackers to exploit the vulnerability again.
You may wonder how can a low-level customer replace files in the folder C:\Program Files (x86) when the folders typically require high privileges? If you remember, Steam provides complete approval to that directory for some reason and so anybody can replace those files.
This implies that an assailant can add the older versions of these two documents into their malware and replace them once performed so they can run the exploit and obtain high privileges on the Windows device. The attacker will have complete access to the device at this stage, adding users, downloading more malware, or performing any command they want.
In his written submissions, Liu says that he decided not to report the bypass of this vulnerability because Valve’s bug bounty program excludes this kind of vulnerability.
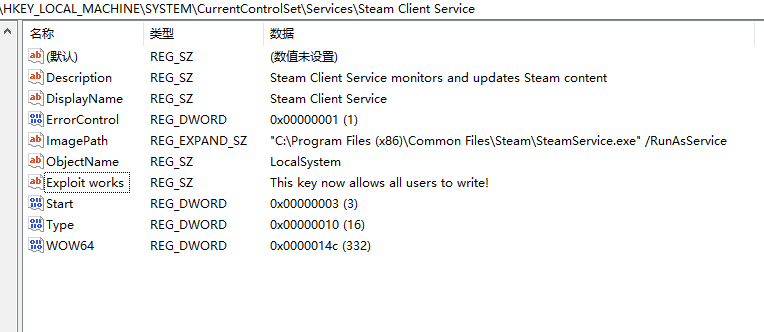
I believe that even allowance for all users to writen to C:\Program Files (x86)\Steam itself is a vulnerability because normal users may replace Steam.exe in that directory, or when admin users log in and out of this directory, and because Valve expressly excludes “assaults requiring the capacity to drop files in arbitrary places on the user’s filesystem”
We contacted Valve with inquiries about this bypass, but did not listen back when this paper was published. In the past two papers, we also approached them, but never got a response.











Leave a Reply